- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- Firewall and Security Management
- :
- Re: CheckPoint appliances behind other CheckPoint ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CheckPoint appliances behind other CheckPoint firewall
Hello everybody
Faced with strange issue. In our company we use 2 CheckPoint appliances (a cluster) as gateway to Internet. Now we purchased 2 more gateways (they also joined to a cluster) to protect our servers network segment. So, these gateways are behind our Internet gateway. To allow them to get updates, check licenses, etc., I added rules to Internet gateways and everything is working. The gateways for servers able to see Internet but when I install policy for them they stop to see anything. If I unload policy (fw unloadlocal) they start to see the Internet again. I tried to enable proxy server on 'internet' gateway in hope that these servers gateways will contact with Internet through that proxy but no luck...
Still googling to solve the problem but no ideas at all.
17 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sounds like your drop rule is doing it. Have you checked logs for dropped traffic originating from server gateways? Or adding specific rule to permit this traffic?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kasparas,
Thank you for fast reply. There are 2 permit rules were created - one installed on 'internet' gateway to allow access to Internet for 'servers' gateway and one 'allow all to all' which is installed onto 'servers' gateway. When I check logs I see that 'internet' gateway allows all for 'servers' gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But do you see a log for unsuccessful case for "server" firewall? Have you tried packet capture to see if traffic actually leaves "server" firewall when it does not work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here the log. Traffic from 'server' gateway is allowed but it can not reach requested destination.

Here what I see if I perform 'fw unloadlocal' command at 'server' gateway
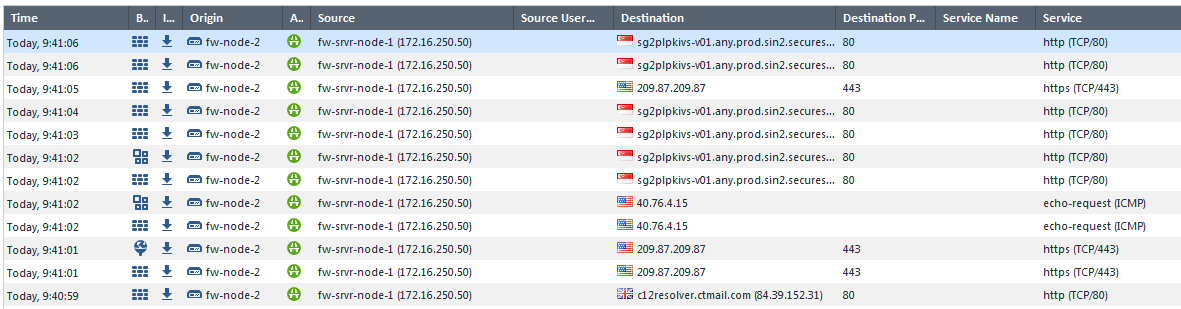
As you may see traffic is always allowed. The problem is in 'server' gateways themselves.
I did not try to capture the packets yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please make sure those "internal GWs" are NAT-ed properly. They should be either using NAT Hide on the external GW with other elements of the internal networks or be statically NAT-ed on the external GW with automatic NAT.
Also, make sure they are defined with main IPs that are mentioned in your NAT rules.
Finally, putting traces with fw monitor would help to see where the internet packets are going, after policy installation
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally solved it...
These 2 gateways were joined into 'active-active' cluster with 'multcast' load sharing. I changed it to 'unicast' and set 'use virtual mac' option and everything started to work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why oh why Russian guys always want LS clustering??? It creates more issues than resolves
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do we? 🙂 Is LS bad feature?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes you do. I rarely see LS in production in Europe while it is all over Russia for some reason. LS is not "bad" per se, but it needs to be used with caution and understanding of all implications. It is definitely should not be the default clustering mode for physical gateways, and it does not really boost performance of a two GW cluster on a level that would "compensate" all inconveniences and limitations.
Mind all above is my private opinion, and it is off-topic here 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We love challenges and something interesting to fix!
But usually it's just difficult to explain to managers or engineers of customers why active-active is not recommended, why it causes more issues than adds performance. Because "if vendor makes it available in configuration, then why it is not recommended"? Active-active adds some more performance, so for them it is seen as a good thing. And if customer really wants it, integrators will implement it in that way.
Can Check Point provide an official statement that active-active is not recommended (although supported) for a cluster with two gateways?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is the misconception: Active-active adds some more performance, so for them it is seen as a good thing.
LS in Multicast mode does add some throughput in sterile conditions without any significant load, but it also introduces some other limitations and caveats, such as SDF, Flash&ACK Sync requirements, loss of SecureXL acceleration, etc.
Unicast mode with two members means 70% of traffic being forwarded to the second member, so once more, increased performance here is questionable.
There is actually a document describing the limitations of LS mode: ClusterXL Load Sharing mode limitations and important notes
In addition, you can always refer to ClusterXL ATRG to the relevant chapters.
As for the official recommendations, you may have mentioned Check Point is very cautious about calling supported features as "non recommended" in any general sense. Each functionality can be required and productive in specific scenarios. For example, using unicast LS mode might help to cope with outdated switches and routers that cannot handle multicast traffic and gratuitous ARPs.
In my personal experience, however, the usual justification of using LS mode specifically in your region is usually "why the second box does not pass any traffic if we paid for it". It is not a proper engineering argument, in my book.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree with Valeri here.
Unicast mode with two members means 70% of traffic being forwarded to the second member, so once more, increased performance here is questionable.
I already had the following problem with LS Unicast mode:
In unicast mode I already had problems with sync interface. For example, if the firewall has 10x1GBit network interface, it must transmit the flash and ACK trafic over the sync interface. This can overload the sync interface in special cases. Here RX-DRP errors occurred. Then the cluster didn't work properly anymore and I had many side effects.
I wouldn't use LS Unicast mode and it doesn't look likes any better with LS Multicast mode.
Regards
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
>>> it must transmit the trafic over the sync interface
This is incorrect. Forwarding is done on the interface that receives a packet. You sync issue most probably is caused by excessive Flash&Ack.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have been mispronouncing here. Your statement is correct.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
no prob.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"why the second box does not pass any traffic if we paid for it".
Exactly. And don't forget "if the vendor put a checkbox for this setting, then it must work well".
So, as you noticed, all technical explanations go away. And that's the answer to your question about why it is popular in Russia.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
...which is personally find not compelling enough...
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 31 | |
| 19 | |
| 13 | |
| 10 | |
| 9 | |
| 8 | |
| 6 | |
| 6 | |
| 5 | |
| 5 |
Upcoming Events
Tue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáTue 24 Mar 2026 @ 06:00 PM (COT)
San Pedro Sula: Spark Firewall y AI-Powered Security ManagementAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


