We have made good progress on depreciating all versions of NTLM in our environment. With us getting assistance from Microsoft premier support, from a non-public knowledge base article, we were able to migrate AD CS (Active Directory Certificate Services) over to Kerberos as well for automated certificate enrolment interactions.
CheckPoint identity awareness is now the last remaining item in our environment which appears to break when we disable NTLM completely. Surely CheckPoint, as a security focused vendor, have a method for gateways to retrieve the security event logs without relying on NTLM?
Group Policy (GPOs) are applied to members servers and workstations to disable NTLM:

This then breaks CheckPoint Identity Collector, unless we apply the following policy just to the DCs (whilst continuing to apply the above policy to the dedicated Windows Server 2022 host running Check Point Identity Collector v81.035.0000). The following GPO is exclusively applied to our Domain Controllers:
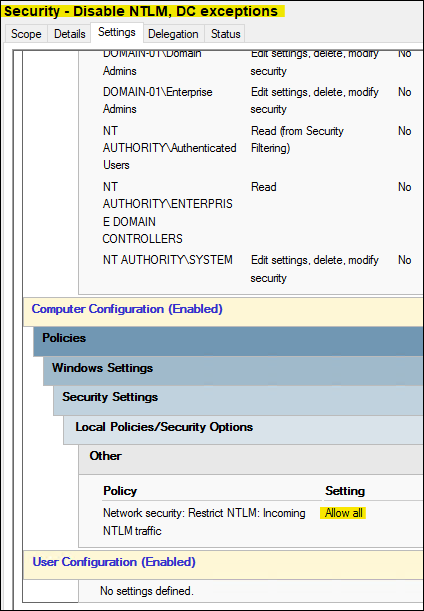
With this applied everything works perfectly:
Wanted to reach out to the community before opening a case with TAC, we have Kerberos AES integration working between the gateways and the DCs, it's purely the Identity Awareness application which does not appear to provide support for Kerberos.
Edit:
My unenlightened understanding is that the DCOM call from the Identity Collector to the DC isn't using NTLM, otherwise it should have been blocked by the GPO blocking any and all NTLM. I thus presume the NTLM auth is within the LDAP TLS tunnels to the individual DCs then.
Problem currently is that the NTLM auth doesn't originate from anywhere, we can't even lock down NTLM by adding an exception via the 'Network security: Restrict NTLM: Add server exceptions in this domain' GPO.
Herewith a sample:
NTLM server blocked audit: Audit Incoming NTLM Traffic that would be blocked
Calling process PID: 4
Calling process name:
Calling process LUID: 0x3E7
Calling process user identity: REDACTEDDC01$
Calling process domain identity: REDACTED
Mechanism OID: 1.3.6.1.4.1.311.2.2.10
Audit NTLM authentication requests to this server that would be blocked if the security policy Network Security: Restrict NTLM: Incoming NTLM Traffic is set to Deny all accounts or Deny all domain accounts.
If you want this server to allow NTLM authentication, set the security policy Network Security: Restrict NTLM: Incoming NTLM Traffic to Allow all.





