- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Certificate Renewal - how is this task processed -...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Certificate Renewal - how is this task processed - Reporting options required
Hello,
Can someone help me to check the certificates installed on Check Point appliances?. I have two requirements, need to check whether these appliance/gateways are installed valid certificate for WebUI and SSH access and what is the validity and expiry date and who provided the certificate (ether ICA or third-party certificate authority)
Any update on this is greatly appreciated
Thanks in advance
Thanks,
Somasekharan
- Tags:
- cpca_client
5 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Moving to Appliances and Gaia
Every time you connect to one of the web portals, the public certificate of that portal should be offered.
This is how TLS works.
I suppose you could use something like the following to programmatically evaluate the various portals: Proactively Handling Certificate Expiration With ssl-cert-check -- Prefetch Technologies
SSH keys are not issued by a certificate authority.
They are almost always internally generated and do not have an expiration date.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your response
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you need to check all certificates expiration, you may check also the ones which are used to establish IPSec tunnels. By default they are generated for 5 years ... if some of your Security Gateways have to be in place approx this time, you should pay attention to that expiration : if expired, you will not be able to establish VPN IPSec tunnel.
I use the following command on the Security Management Server:
cpca_client lscert -kind IKE -stat Valid > /var/ValidIKECert_`/bin/date +%Y-%m-%d_%H%M`.txt
More details on cpca_client lscert command (from Command Line Interface Reference Guide of R77😞
Description Show all certificates issued by the ICA.
Syntax
> cpca_client [-d] lscert [-dn <substring>] [-stat {Pending|Valid|Revoked|Expired|Renewed}]
[-kind SIC|IKE|User|LDAP] [-ser <ser>] [-dp <dp>]
Parameter Description
-d Runs the command in debug mode
-dn substring Filters results to those with a DN that matches this <substring>
-stat Filters results to the specified certificate status: Pending, Valid, Revoke, Expire, or Renewed
-kind Filters results for specified kind: SIC, IKE, User, or LDAP
-ser <serial> Filters results for this serial number
-dp <dp> Filters results from this CDP (certificate distribution point)
The content of the file generated should be something like:
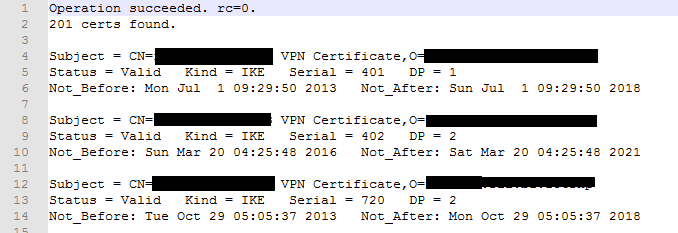
which could be transform to:

... in order to be imported in any spreadsheet software.
Cybersecurity Evangelist, CISSP, CCSP, CCSM Elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your input
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you all for your feedback. I will go through your comments.
If we have the certificate from the internal Certificate authority for For the administrative access (via ssh, WEB-UI) on the security components, hope the same can be pushed to use laptop using Group Policy.
My organization is asking for the certificate for administrative access (via ssh, WEB-UI) on the security components.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 17 | |
| 11 | |
| 8 | |
| 7 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


