- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Allow access to specific truncated URL's
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Allow access to specific truncated URL's
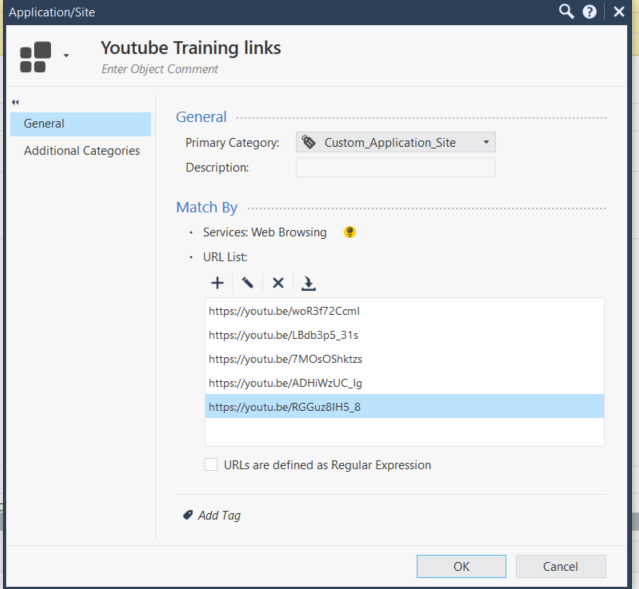
Is there a way to allow access to specific truncated URL's, in this case ones at "youtu.be" ? It seems the checkpoint blocks them all by default, I tried creating a custom application/site with the specific links I want in it, but it is still being blocked;
The policy is just an allow any any basically;
The checkpoint ver is R80.30. I'm pretty new to Checkpoint, so I assume I am just missing something. Either that, or there is no way around the truncated URL block.
Thanks
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
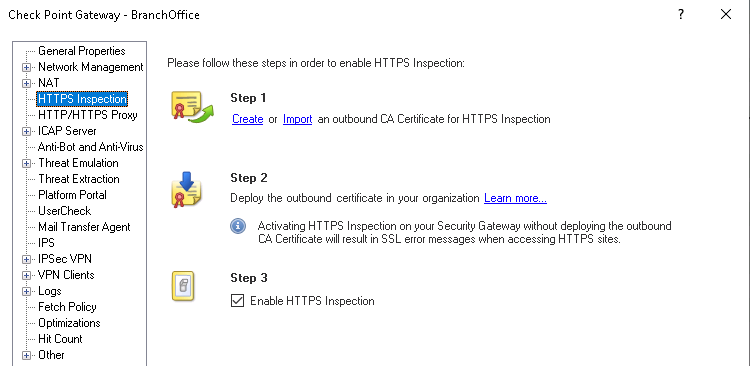
You can look on the gateway object:
The fact it doesn't work suggest it's probably not enabled.
Note: this has significant impact to your users and your overall gateway performance, not to mention requires some level of planning to do correctly.
This is not something that can or should be enabled lightly.
What I suggest in this case is, since you generally allow access to YouTube anyway, allow access to its URL shortener prior to the rule that blocks URL shorteners (e.g. just the URL https://youtu.be)
This should work since we only need to see the certificate (more precisely the SNI portion) and it's not really a general purpose URL shortener.
When R80.30 shipped, SNI verification did require HTTPS Inspection be enabled (could be with an any any bypass rule), but I believe this is addressed in recent JHF (above Take 111) as well as in R80.40 and above.
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First of all, without HTTPS Inspection enabled, nothing like this will work since it's impossible for the gateway to see the URL otherwise.
Second of all, a YouTube page involves many connections, which may not be caught by this rule and blocked by the other rules.
You might need to enable something like YouTube Strict mode.
You can force that on the gateway with HTTPS Inspection enabled and: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
Corresponding Google Help article: https://support.google.com/a/answer/6214622?hl=en&ref_topic=6248111#zippy=,option-http-headers
Then you can control what videos your users can see.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't think I explained that very well. We do not block YouTube at all. Users can go to any youtube video as youtube.com is completely allowed.
The issue is the truncated links. I work for a state agency, and a different state agency posted some training videos on youtube, but for some reason the only links they put on the website for them are the truncated ones. Truncated links are a known security issue, so I don't want to allow all of them, just these 5 so users can get to the training videos.
So we are not trying to restrict youtube to certain videos, I am trying to allow certain truncated links.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You still need HTTPS Inspection enabled to "see" the precise URL.
Do you have this enabled or not?
Without it, you will not be able to allow access to these precise URLs since they are HTTPS links.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm actually not sure if it is enabled or not. I inherited this Checkpoint, and have no experience with them prior, so figuring things out as I go. How do I tell if it is enabled, and if not, how do I enable it?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can look on the gateway object:
The fact it doesn't work suggest it's probably not enabled.
Note: this has significant impact to your users and your overall gateway performance, not to mention requires some level of planning to do correctly.
This is not something that can or should be enabled lightly.
What I suggest in this case is, since you generally allow access to YouTube anyway, allow access to its URL shortener prior to the rule that blocks URL shorteners (e.g. just the URL https://youtu.be)
This should work since we only need to see the certificate (more precisely the SNI portion) and it's not really a general purpose URL shortener.
When R80.30 shipped, SNI verification did require HTTPS Inspection be enabled (could be with an any any bypass rule), but I believe this is addressed in recent JHF (above Take 111) as well as in R80.40 and above.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks PhoneBoy, that did it. I would have rather narrowed it down to those specific URL's, but like you said this isn't a general purpose URL shortner, but the YouTube specific one. I have put a request in to the other agency to use the full links on their webpage also, so hopefully I can remove this in the future.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Taking advantage of the reason for this thread, I make the following query.
Is it mandatory to activate HTTPS Inspection, when you activate the APPC+URLF blades?
I have done a lab, where I activate these 2 blades, and manually block certain URLs that are in HTTPS, and the firewall, without problems, blocks the traffic, thus obeying my explicit rule.
So, it leaves me with the doubt, is it mandatory to activate HTTPS Inspection?
Or is it more related to a "Best Practice" issue?
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Its not mandatory, but since probably 98% of sites nowdays are https, thats where benefits of https inspection come in.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This link bro explains inspection very well...its not official CP one, but same would apply.
https://www.thesslstore.com/blog/ssl-inspection/
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mandatory? No.
However, it will be required to do any form of content inspection (either threats, DLP, or other).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey,
Message me privately and I can help you. I did https inspection for few customers and Im pretty experienced in it, if I say so myself : ). Im confident I can give you some insight. But, phoneboy is 100% correct...this will NEVER work without that feature enabled, because firewall will never know what is supposed to inspect. Technically, if you have url filtering blade enabled, you can allow those custom categories, but again, it might be tricky to make it work like that. Anyway, hit me up offline and lets fix this on webex or zoom.
cheers,
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 20 | |
| 16 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter