Hi all,
I need some advice for an unusual setup regarding two ISP connections and Site to Site VPN Link Selection settings( or possibly other settings as well).
So far I learned that it is no problem to have an ISP connection over an interface with a private IP (public network gets routed to this IP from the next Hop). We create a dummy cluster interface with the public IP we want to use and set LinkSelection to use this IP.
I also learned that it should work having two ISP connections and set Link Selection to use the IP of the outgoing(initiating) or incoming(responding) interface. This we have not tested so far, but in Theory it should work, right?
Now we come to the problem: Our customer has a mix of these. The first ISP connection is an interface with a public IP on it where all traffic goes out. Now we got a second ISP with more bandwidth, to where we want to move the Site2Site VPNs in the future. This is connected to the gateways on an interface with a private IP.
We need to be able to have Site to Site VPNs on both interfaces, as we cannot move all at once and also there will be 3rd party Gateways(so no link probing possible). And further we also need to be sure about the Link selection settings before changing them, as we do not want to affect existing tunnels.
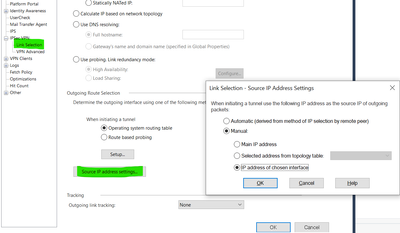
The Link Selection Settings we use now:
- first option for locally managed VPN peers is set to MainIP(public IP of first ISP)
- outgoing route selection is set to "reply from same interface"
- source IP settings are set to automatic
We then proceeded to set up a tunnel for testing, which on our end we configured with the dummy interfaces public IP address as the remote peer. On the customers end we set up the tunnel in the usual way and configured a static route for the remote network to point to the interface for the second ISP, so the traffic would go out that way and not per default route over the first ISP link.
The Tunnel itself builds up just fine, Phase1 and Phase2 are completed successfully and in a tcpdump we see the correct IP addresses talking to each other. When we send some ICMP requests, we see those requests arriving at the customers gateway, they get decrypted and the destination responds to these requests. But then we see that those ESP pakets leave the Gateway on the correct interface, but sadly with the private IP of this interface and not the public one from the dummy interface. Of course they never reach the other end.
Why is it that the IKE stuff on port 500 is handled with the correct IP, but the ESP traffic on port 4500 is not?
Is there anything we can do to make this work?
Any insight into this is much appreciated, as this has given me some headaches already for some time now.
Cheers,
Alex