- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- About SMB 1600 bridge mode
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
About SMB 1600 bridge mode
Hello Sirs,
I've received a requirement where the current network architecture consists of an external firewall, CoreSwitch, LAN DHCP, and various devices such as PCs, ESXi servers, and other servers. During vulnerability scanning, it was discovered that certain ports on the internal servers are potential attack targets.
To enhance security and compliance, I'm considering adding a SMB CheckPoint firewall to the network and enabling IPS functionality without disrupting the existing network architecture. I've thought about using CP's Bridge Mode for this purpose, but I have some questions.
In my proposed architecture, I plan to make ESXi and problematic servers part of the Bridge Mode setup. Would it be possible to control traffic rules using this CheckPoint firewall? For instance, can I set up rules to restrict specific IP traffic through this configuration?
such as :
Oracle Database Server Vulnerabilities (Port 0):
- Restrict access to this port to specific IPs that need access.
- Implement IP whitelisting for authorized connections.
PCI DSS Compliance: Detected Remote Access Software (Ports 139 and 445):
- Limit access to these ports to specific IP addresses (privileged computers) that require remote access.
- Utilize IP whitelisting to control access.
Oracle Database Vulnerabilities (Port 1521):
- Apply IP restrictions to limit connections to this port.
- Ensure that only relevant hosts (e.g., AP and CP) are allowed access.
PCI DSS Compliance: Detected Remote Access Software (Ports 21 and 22):
- Restrict access to these ports by specifying authorized IP addresses (privileged computers).
- Employ IP whitelisting to enforce the restriction.
Unsupported Linux Kernel Version Detected (Port 23):
- Implement IP-based access control to this port.
- Limit connections to privileged computers.
SSL/TLS Vulnerabilities (Ports 443 and 8081):
- Apply IP restrictions to these ports to allow access only to authorized IP addresses.
- Consider disabling older SSL/TLS versions and weak cipher suites if feasible for security
Does it work?
Thanks kindly support
23 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Read here: sk101371: Bridge Mode on Gaia OS and SecurePlatform OS
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Sir
I just read the document, but I don't quite understand it
Regrettably I don't have physical machines in my company.
Just want to make sure, in my architecture if i want to release 2 server under to Brige mode SMB FW1600 , does that function were make same of the traditional firewall as we know, to install policy setup the rule , Source ,Destination , VPN action ?
The purpose of this is to eliminate changes to the current architecture and to control traffic and IPS functions.
Thanks your time.
Jordan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Legend:
= Supported
= Supported, but requires a software package, or limitations exist
= Not supported
Software Blade /
FeatureSupported in
Gateway mode?Supported in
VSX mode?Firewall 

CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You realize you can also run a virtual security gateway inside your ESXi environment, right?
Also, it's not clear how the traffic will flow here or be restricted to going through the bridge, or might flow through the bridge more than once.
Having traffic traverse the bridge more than once is not supported (i.e. double inspection).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Sir,
We have two ESXi virtual machines in our environment, and we need to implement IPS and security protection for the VMs within them. If we connect both ESXi hosts to a CheckPoint 1600 in Bridge mode, will the traffic flow be sufficient?
However , According to my CheckPoint distributor partner in Taiwan, the recommendation is to add an additional switch in this scenario. However, I don't fully understand the purpose of adding a switch without making changes to the network environment and IP settings. Additionally, I'm unsure about where this switch should be placed...:(
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ask the CP TAC engineers !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the physical connectivity between the ESXi server and the 1800 and how will that map to the VMs in question?
And why not run a Quantum Security Gateway as a VM instead?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
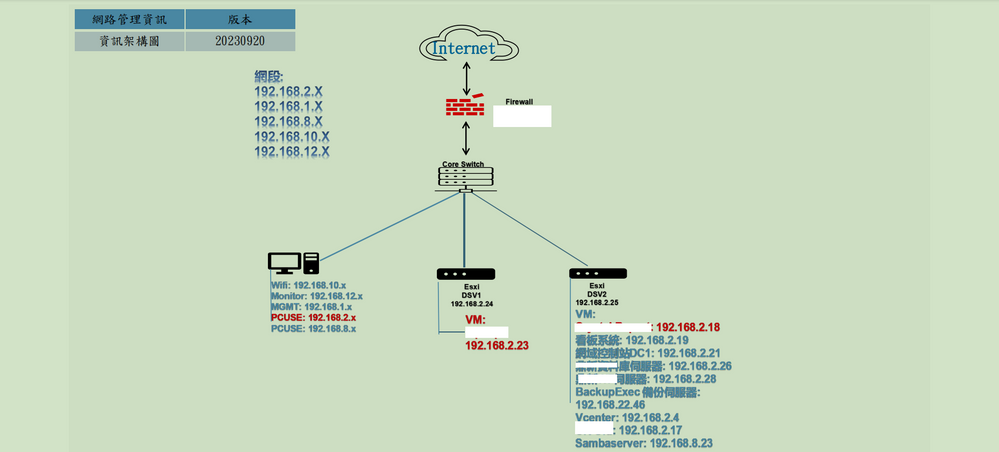
Hello Sir,
That is my new writed layout as below,
If i don't want to change my current service IP address, where is the CP1600 good for this case
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Where is the CP1600 ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are not deiced where is the locale of CP1600
As regarding of support team recommend
I am really confuse why we need to added a new switch between the CoreSwitch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
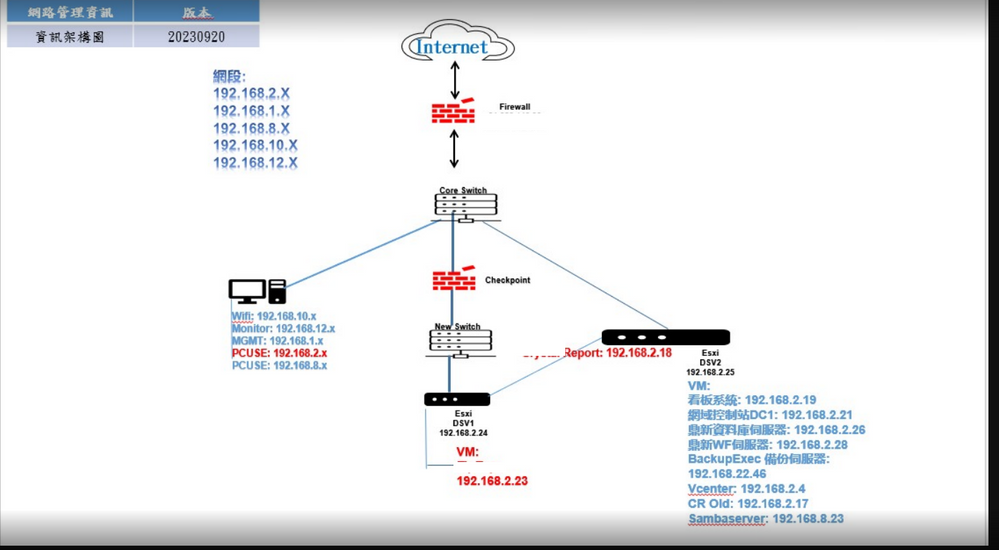
This looks wrong, i see a loop !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How about that ?
Could you please let me know why be setting to the loop ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you explain to us in detail what servers and its IP needs to be in the protected scope...like the direction of the connections?
Note that if the servers IP that's running on ESXi is in the same network segment, typically IPS would not be enforced in the first place, or can only protect a certain asset and not both at the same time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Sir,
We would like to protected these VM segment of 192.168.2.X
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you referring to North-South traffic to different segments or, East-West traffic to protect traffic from/to servers in the same segment?
<e.g.>
192.168.2.0 <-> 192.168.2.0 : do you want security inspection to be enforced on inbound/outbound traffic between servers in the same segment?
192.168.2.0 <-> 192.168.1.0 : Or between other networks that traverses through the core switch? or both patterns?
just to make things clear.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Sir,
We just to define and protect 192.168.2.X segment , Because we have going to vulnerability scan had 1433 port issue in that DB server.
So we just to confirmed Intranet traffic, actually in customer layout that have set the policy on that outside firewall.
All intranet segments can access 192.168.2.X
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
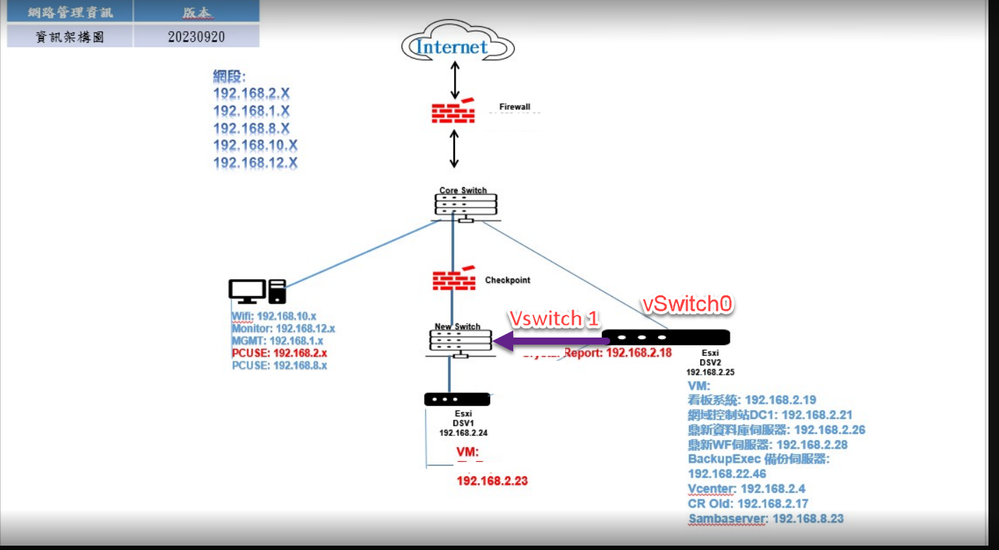
What about this:
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Sir,
According of your graphic your mean is that all ESXI to connected to new deploy switch DSV2 vswitch0 , 1 ?
That is my our expectations, but we afraid will the traffic be insufficient.. does it cause a loop if I keep my layout ? Vswitch0 to core switch ?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All traffic that has to be inspected must pass thru the 1600.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
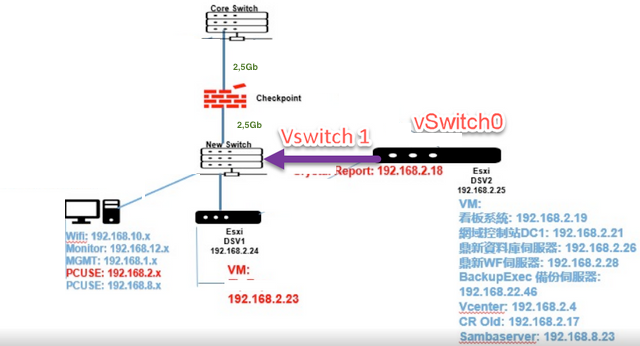
we afraid will the traffic be insufficient - do you need more than 2,5 GB ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately , we encountered a failure after last week's testing. We have an Esxi host that, after migrating through a Vswitch, is unable to successfully obtain the Gateway. We suspect that the issue may be related to the Edge Switch, which might require a Layer 2 switch that can be configured as a trunk. It's worth noting that even though our company environment doesn't utilize VLANs for control, everything is currently operating on VLAN 1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Even when you do not explicitly use VLANs, VLAN 1 always "exists" as it is the default LAN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is a Layer 2 Switch behind the firewall necessary? In CheckPoint, using Bridge mode,
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 25 | |
| 20 | |
| 8 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter