- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- AW keeps deleting Dameware Service
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
AW keeps deleting Dameware Service
We have been working with Check Point on this issue nearing 3 months.
Despite all of the exclusions and updates we have made, the Anti-Malware Blade insists that the Solarwinds: Dameware Mini Remote Control service is malicious and deletes the corresponding .exe files.
-DWRCS.exe
-DWRCST.exe
-DWRCSET.dll
-LogAdjuster.exe
What we've done:
-Followed ALL of the steps in sk13132
-Analyzed the forensics reports and made suggestions for new exclusions
-Tested several "new" AW policies that Check Point suggested
-Selected "Skip File" under "Riskware Treatment"
-Updated our SmartEndpoint (R77.30.03-990003009, e80.86 version)
-Tested the software on different client versions (Same result between e80.70-e80.86)
-Applied the necessary hotfixes to the Smart Endpoint
-Added Dameware as a whitelisted application under "Application Control"
-Sent various updates and cpinfo's, logs, and screenshots to Check Point
-Reached out to SolarWinds for advice (No such luck)
Was wondering if anyone else has experience with the Dameware service while using Checkpoint Endpoint Protection and whether or not they need exclusions/if their exclusions are working properly?
I realize that there are businesses in the same boat as us and that this may be a shot in the dark, but I thought it was worth a try.
20 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What SRs have you opened on this issue?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Currently, I have 3-0414220611 open in regards to this.
(This is an amalgamation of calls, chats, and other various SR's compounded.)
In the past, I've had:
3-0535640411 (Concerning what the special client version build did to our computers in a test environment.)
and a few various other SR's in relation to the behavior/ how the suggested actions have affected us.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We use DameWare and simply edited the "Scan all files upon access" section and added the following:
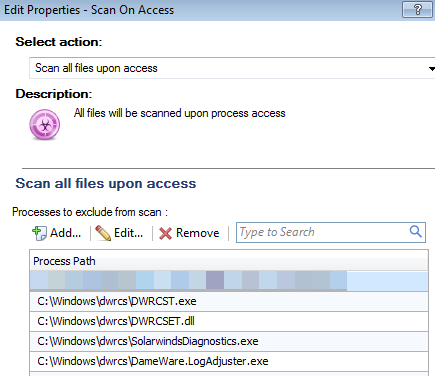
Seems to work fine for us. R77.30.03
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So yours is working with the following exclusions:
-C:\Windows\DWRCS\DWRCSET.dll
-C:\Windows\DWRCS\DWRCST.exe
-C:\Windows\DWRCS\SolarwindsDiagnostic.exe
-C:\Windows\DWRCS\DameWare.LogAdjuster.exe
Ours has:
-C:\Windows\DWRCS\DWRCSET.dll
-C:\Windows\DWRCS\DWRCST.exe
-C:\Windows\DWRCS\SolarwindsDiagnostic.exe
-C:\Program Files\SolarWinds\DameWare Mini Remote Control x64\solarwindsdiagnostic.exec:\windows\dwrcs\DameWare.LogAdjuster.exe
(Based on what was given in their sk for this issue.)
Sounds like I need to take out the last exclusion and add C:\Windows\DWRCS\DameWare.LogAdjuster.exe instead.
"C:\Program Files\SolarWinds\DameWare Mini Remote Control x64\solarwindsdiagnostic.exec:\windows\dwrcs\DameWare.LogAdjuster.exe" is literally how they have it listed in their sk. As well as "DWRCSET.exe" which is incorrect.
Thank you so much for your insight!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not a problem. I did some more digging and found we did put in an exception in quarantine as well. Picture below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you! Those are the exceptions we have in place there, as well.
We also have these exclusions under "Scheduled Scan Targets":
I made the adjustments to the "Scan on Access" section and hope that changes things. It mirrors what you have in that respect now. (@Alex Weldon)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We're still experiencing this issue, even after the changes I made similar to yours. Quick question: Are you using R77.30.03?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Stacey, I am using R77.30.03 on a standalone vmware server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you, we were wondering if perhaps R80.20 was a solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The changes seem to have helped significantly, but we are still getting scattered deletions that are failing to report to our email alerts.
I am wondering if adding "C:\Windows\dwrcs\dwrcs.exe" will help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are having this exact same issue as well. All the exclusions are added above as you have in your setup, but sporadically we are still seeing dameware files removed from endpoints. We had a ticket opened and closed but I think its about time to open one up again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah, seemingly it was working for a period of time. But, we are still getting scattered deletions. (My own laptop deleted it this morning upon startup.)
Do you mind if I asked why the ticket was closed? Was it believed to have been solved?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, when we were seeing the issue of dameware being removed we had whitelisted all of the above folders and .exe that you all have gone over above. I thought it was possible that it was removing the dameware product before it was gathering the policy, like on a new install of checkpoint client on an endpoint. Meaning it would scan and remove before gathering our default policy. Checkpoint said it was how the product behaved where it would take up to five minutes to gather policy so we closed the ticket. However now we are seeing like 5 or 6 computers a day where dameware is still getting removed, yet their policies should be current. Not really sure where to go from here. Another ticket I suppose
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes! That's exactly where we are with it. We've had the same ticket open this entire time, though. I appreciate your comments. It's good to know we aren't the only ones this is happening to.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Currently I have gone back over and made the changes recommended from sk131312 exactly, and removed any other additions we had added for dameware. Going to watch for updates and probably open another ticket.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
They've built a client version for us to test specifically for this issue. (It's an e80.85 EPS.msi, strictly for 64 bit machines.)
Thus far, I haven't had the best of luck with it, but I'm going to test it on an old laptop I have sitting in my office. The first time I deployed it to my production laptop, it crashed it and I had to completely blow it away and re-image it. Lesson learned: I will never test any software outside of a VM or test environment again. Hahaha.
I'll let you know if we have any progress or hear of any news.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Update: We still haven't made any traction. I have been instructed to implement the test client they have provided on to production PC's to further test.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Stacy,
We have since reopened our ticket on this issue as we have not made any headway either. Will keep you updated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Update, after opening a ticket we were told that the fix was to update our fleet to 80.85 version of the endpoint so we are working on that now. I will let you know if it makes a difference.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The special build seemed to have worked for us, as well. I was told there was going to be an addition that included whatever helped fix it in the newest client release.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 21 | |
| 19 | |
| 11 | |
| 8 | |
| 7 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


