- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Re: SMB Central Management Best Practices
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
SMB Central Management Best Practices
Dear friends,
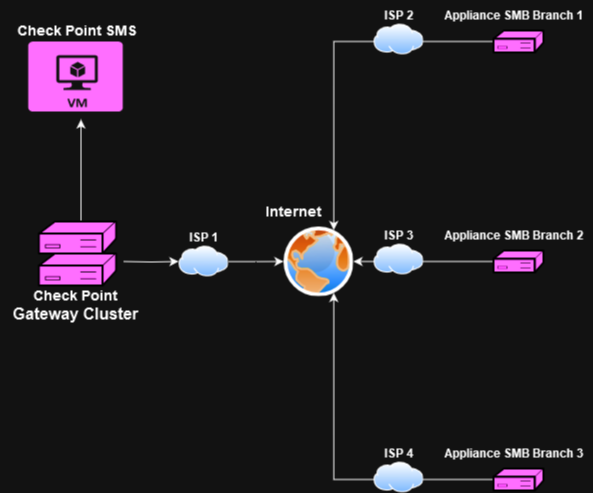
I would like to request assistance with a specific scenario. We have an environment where the customer has a Check Point cluster (26000) and an SMS (VM) in their main office.
We are starting a project where several 1500 (Spark) appliances will be installed at different points of presence.
These appliances need to be added to the SMS in the main office, meaning they will be configured as 'Central Management.' These appliances will be connected to the internet with dynamic IP, and the topology will look similar to the image below.
My question is as follows:
What is the best practice or Check Point's recommendation for this scenario?
Do I need a public IP for this SMS so that the appliances can connect?
Is there any Zero Touch Provisioning (ZTP) process?
I haven't found any clear documentation on this. Thanks for your help in advance.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Bernardes these check is done by SIC. Connection of an unknown gateway to SMS has to be allowed to reach the SMS, but the gateway must "authenticate" to SMS via SIC. You configure a first time SIC- password on your remote gateway if you deploy this. After first connection SIC will be established and your SMS trusts your gateway, this is the same way how it works with your existing gateways. For you're gateways with dynamic IPs you can't filter based on IP addresses because they are unknown, you need some more "authentication". That's what's down via SIC.
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, my friend @G_W_Albrecht , thank you for getting back to me. I had already come across this guide, but it's not clear regarding my specific needs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can use https://zerotouch.checkpoint.com/ for first time deployment. No need to do anything on the SMB gateway. You can prepare a configuration in the zerotouch portal including connection to your on premise SMS.
Follow instructions in Zero Touch Cloud Service for Check Point Appliances
And yes, you need a public IP for your SMS which is normally NATed on your gateway tho the internal IP of your SMS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, my friend @Wolfgang , thank you for your help. So I will indeed need a public IP for the SMS, whether it's dedicated or NATed by the gateway, that was a doubt.
But regardless of the option I choose, how can I ensure that only the SMB appliances are allowed to connect to the SMS, given that it now has a public IP, and the appliances have dynamic IPs, making source-based control difficult? The guide doesn't clarify this, and I couldn't find any other useful documents.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Bernardes these check is done by SIC. Connection of an unknown gateway to SMS has to be allowed to reach the SMS, but the gateway must "authenticate" to SMS via SIC. You configure a first time SIC- password on your remote gateway if you deploy this. After first connection SIC will be established and your SMS trusts your gateway, this is the same way how it works with your existing gateways. For you're gateways with dynamic IPs you can't filter based on IP addresses because they are unknown, you need some more "authentication". That's what's down via SIC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Geo based enforcement could be a potential option to explore if you must restrict this somewhat.
There are examples shared previously here as relevant to VPN and implied rule enforcement that bare some similarities.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
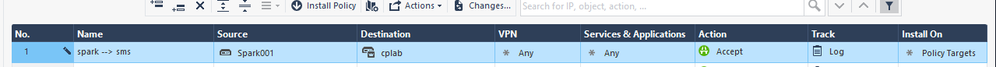
Hello @Wolfgang , after establishing the SIC on the first connection, could I use a rule like the one below? Using the object that represents the SMB appliance as the source. Would this have any effect or would it make no difference?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
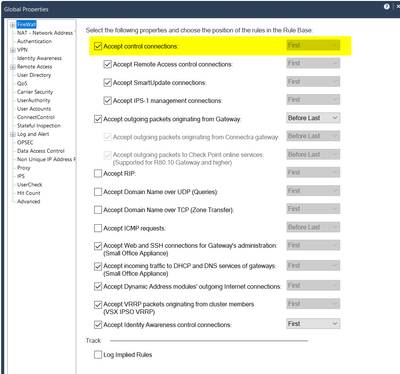
@Bernardes if you use the defaults ther's no need for such a rule. Control connections are allowed via global properties.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Wolfgang , I understand. Is there any other document besides the guide that provides more information about the deployment or that contains information regarding the public IP and control connections for SMB with Central Management?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think Dynamically Assigned IP Address (DAIP) Gateway FAQ answer your questions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, thank you very much for your help! I believe I now have the necessary information to start the deployment.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter