- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Replace expert password on SMB Appliance
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Replace expert password on SMB Appliance
Hi everyone,
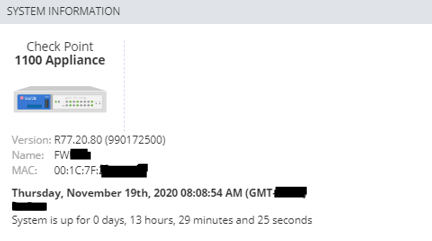
Some time ago a customer requested changes at expert level for compliance purposes. The thing was that since the locally managed SMB device (1140) was inherited from another administrator, the expert password was unknown. Tried a ton of usual passwords for the organization, none of them worked.
After a fast search on SK, I landed on sk106025 and read the following statement:
That was a little bit dissapointing, because I still was able to access as web gui admin and perform many administrator operations. So I decided to find a way to gain expert access without having to factory default the device and reconfigure all parameters from scratch (maybe my lazziness was the main cause of this haha).
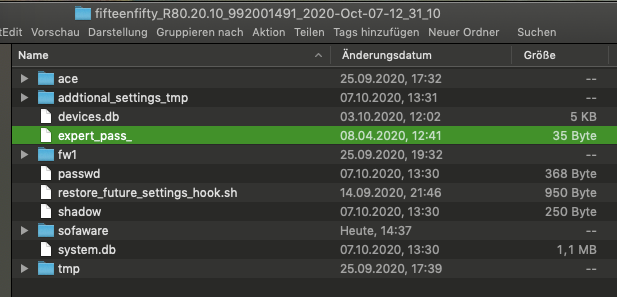
So, moving on. On Web GUI, I generated a backup as usual. This is so important since all the required configurations are contained on this file. Also previous experience from backup restore on different smb hardware, reminded me that all the time expert password was replaced for the one contained on backup.
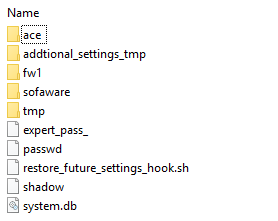
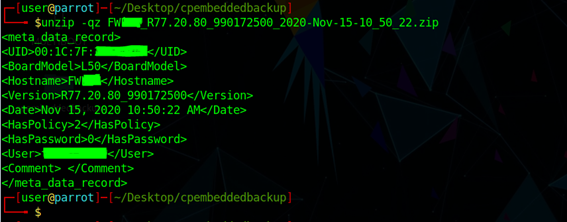
Opening the backup I found the following files:
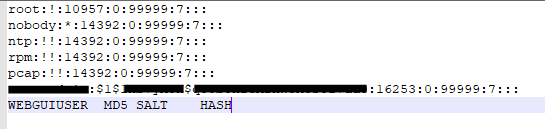
According to sk106025 expert_pass_ file contains the MD5 expert password hash, as expert it can be deleted so the system will ask again for a new password. Also there is the shadow file, that contains MD5 hashed credentials for all users; the web admin among of them (notice the last line was added by me to explain the segments):
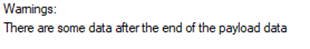
One interesting fact when extracted the ZIP backup on a Windows computer was the following message:
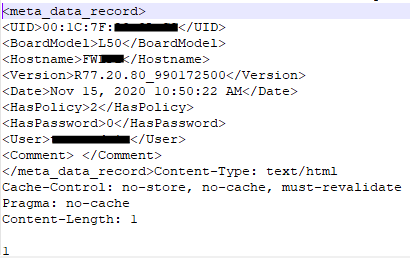
I opened the ZIP file as text to verify, and found the following:
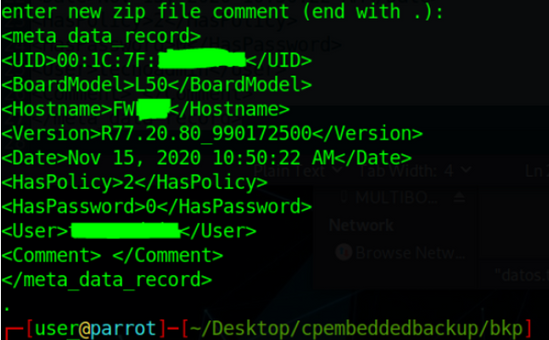
Some metadata is added to the ZIP file, I presume that is to identify the device and proceed with restore. Because of this, I needed to undrestand how backups are generated. I can't only modify the contents under windows since the metadata will be missing after recompression.
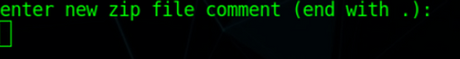
After some digging on Internet, I found a 2016 blog entry by John Fleming where he does a great analysis of backup routine using strace. This gave me the necessary flags to recreate the file using any linux distro with ZIP support. So started a live usb image of Parrot linux (you can use whatever you want). The first thing I did was to check the comment for the previously generated backup and found that not all data is added as comment:
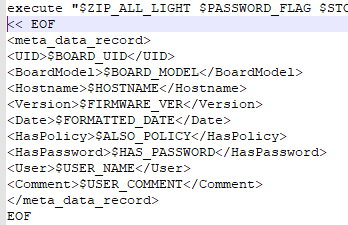
At backup creation, this comment is generated by /pfrm2.0/bin/backup_settings.sh execution, adding the relevant info for the appliance:
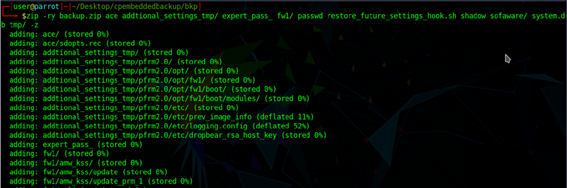
So copied the backup to a new directory and unzipped:
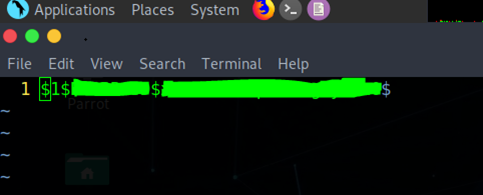
Once all files were extraced, procedeed to edit expert_pass_ file using vim. The unknown expert password hashed data was located here, I replaced it with the information of web gui admin from shadow file (only $1$SALT$HASH is needed):
Zipped a new file named backup.zip using the flags -ry (recursive - include sym links only where is necessary) and -z at the end to add the same comment extracted some steps ago:
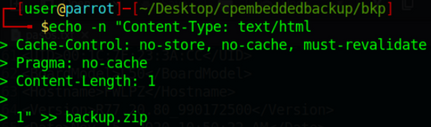
The new generated ZIP backup contains almost exactly the same information at the end of the payload. Using echo, I added the final information (maybe this step is not necessary, I didn't test the restore up to this point) EDIT: After downloading a backup through SCP noticed this information doesn't exists; it's only added when the backup is obtained through a web browser. Used -n flag to avoid a line jump at the end, so it matches the original format:
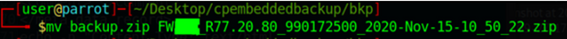
Changed the name back to original to match the CP format:
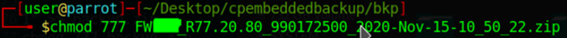
Finally changed file permissions as the original backup (777):
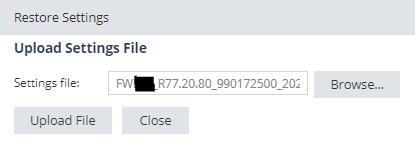
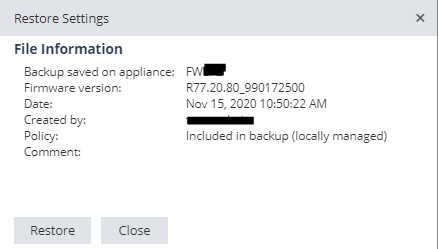
Backup was uploaded and restored to appliance sucessfully:
Finally I got expert access with same password as web gui admin user:
All configurations (policy, vpn, filtering, etc) worked perfectly!!!
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah ! That is the spirit i love 8) !!!
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
😄😄
It should work up to R77.20.XX versions. Still not tried on R80.20.XX since I don't have the hardware.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It seems that the file structure is identical and we have expert_pass_ here also:
So it should work for R80.20.xx also...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's good to know! 😃
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Excellent hack I must say. Thanx for sharing it.
However, I find this as a potential security issue. Tampering with backup files for security devices should not be possible. They must at least be signed. Something CheckPoint should think about...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's right, it can be considered as security issue because the modification of sensitive information. Maybe administrators should document the SHA2 hash of the file itself after the backup generation and manually verify at restore that is not a modified file. This until CP propose new backup procedures to avoid tampering.
Luckily for my case, there was no other checks than zip's comment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Impressed you worked that out.
Thanks for sharing!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're welcome!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
w00t! I remember finding backup info in the comments and thinking that was an interesting abuse of comments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It was there for a reason haha! On my very first test, without comments, the file was recognized as "Invalid backup".
BTW, thank you for the blog post!
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter