- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Re: R80.20 missing basic/critical rootCA's is ther...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
R80.20 missing basic/critical rootCA's is there any public CA bundle from checkpoint?
I have tried to access https://www.clalit.co.il and from this it appears that the R80.20.20 is missing the basic RootCA certificates update.
For this specific domain the the relevant RootCA is:
DigiCert Global Root G2 | DigiCert Global Root G2 | Fri Jan 1 14:00:00 2038 |
the ones in the R80.20 are:
DigiCert High Assurance EV Root CA | DigiCert High Assurance EV Root CA | 11/10/2031 12:00:00 AM |
DigiCert Global Root CA | DigiCert Global Root CA | 11/10/2031 12:00:00 AM |
DigiCert Assured ID Root CA | DigiCert Assured ID Root CA | 11/10/2031 12:00:00 AM |
So, is there a global bundle that CheckPoint supply or I need to download one from Firefox or Chrome or Windows?
Thanks,
Eliezer
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All
CA list gets frequently updates, and actually, was just updated in our last release, so the issue was not an outdated CA list, but an issue in the upgrade code.
clean install get the list updated, and thanks to your feedback, the issue in the upgrade code is now fixes - so CA list gets updated also in upgrade.
will be release soon as GA. for those who needs it now, you can contact support.
thanks!
28 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
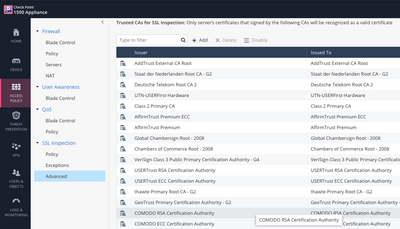
In HTTPS inspection settings in SmartConsole there is Trusted CAs menu. Check if this certificate is listed and if not, you can download the predefined ca-bundle from CheckPoint using the Automatic update menu in the bottom. Otherwise you can upload it by yourself.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I want to install the ca-bundle from CheckPoint since I do not have that automatic update menu.
If I had it I wouldn't ask...
Is there any specific place this ca-bundle can be downloaded from manually?
I can ... add trusted CA's however it's weird that an update to R80.20.20 doesn't contain these.
If the browser and the OS has this I assume that the NGFW 1530 should have it in the firmware upgrade.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just ask TAC in a quick chat !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You wouldnt believe me what is their level of Chutzpa even if I would have qutoted their response in the chat.
And believe me I didn't wanted to write what i am writing here...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please send me the SR in a private message.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The CA bundle is probably part of the firmware.
I doubt it can be updated outside of a firmware update or manually adding the relevant missing CA keys manually here:
Having the CA bundle auto-update is most likely an RFE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK then, auto-update but I'm stuck with the device that cannot be auto-updated.
And the firmware currently doesn't contain these.
My most best solution to resolve this issue to allow traffic is to use Debian or RHEL or SLES or Firefox pem CA bundles in one file.
I would like to get a practical solution from TAC or R&D.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK So I have verified, CP wants a subscription and support contract to operate the device.
Not enough I have paid a really lot of money for the device and the support I need to pay monthly for extra something.
Sorry But it's too much investment and above my poor pocket, If someone wants my 1530 let me know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is no such thing as a free lunch 8) Subscription and Support are needed for any CP product, so your sales contact should have told you so when you bought it. If not, you could ask for your money back, anyway...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm curious what is the issue with simply adding the needed CA keys into the device as shown?
Have you actually tried it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First, I would have expected from an Israeli company to release a firmware with the 2021 relevant ca bundle and not 2016..
If you don't understand this then I cannot answer other questions.
We have a saying: לא תשנא אחיך בלבבך
it's ridiculously amazing to even ask me your question.
the number of updated ca's since 2016 is not something that should be left for any admin.
If checkpoint tech support do not understand the issue with this i assume the certificate blinds their eyes from the real world.
In what world MS windows version do not contain/include a ca bundle, do you think .gov.il domain will use such a product?
also let say they will, if they expect me to use such a product then they are missing something in their brain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for bringing the issue to our attention, we appreciate the feedback.
I feel pretty confident this will be addressed in a future firmware build.
I’ll check if there is a different workaround in the meantime.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Going your own... so ..uh... could it be one of these? Should you do a firmware upgrade these will most likely get over written, but it sounds like you're in no danger of that.
[Expert@1500]# find / -name "*bundle*" | grep -v chroot
/pfrm2.0/opt/fw1/bin/ca-bundle.crt
/pfrm2.0/opt/fw1/database/ca_bundle.pem
/pfrm2.0/config1/fw1/conf/te_remote_gw_ca_bundle.pem
/pfrm2.0/config1/fw1/database/ca_bundle.pem
[Expert@1500]#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried to reburn he image and it seems that the list of certificates was updated.
It's a bit weird for me that this was the only solution I had tried and worked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All
CA list gets frequently updates, and actually, was just updated in our last release, so the issue was not an outdated CA list, but an issue in the upgrade code.
clean install get the list updated, and thanks to your feedback, the issue in the upgrade code is now fixes - so CA list gets updated also in upgrade.
will be release soon as GA. for those who needs it now, you can contact support.
thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Amir_AyalonJust to verify, I have checked what have changed and it seems that the Root CA which Lets Encrypt is using was changed in the last month or more.
Due to this every site which updated the certificate was un-reachable.
It includes many many sites behind sni.cloudflare.com
For example:
https://www.sefaria.org.il/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Elicro,
not sure i understand what you meant.
have you used clean install and still experience an issue ?
(BTW, an official R80.20.20 firmware with some important fixes (including this), will be released today)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Amir_Ayalon Please explain which clean install you are thinking of - including reset to factory settings ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For a new SMB image this would be via USB I expect.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a bit more complicated:
1. upload new firmware in WebGUI and install it
2. after reboot, export the System Settings
3. reboot from USB and install backup and active firmware
4. after FTW, import System Settings
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
New image is available from sk170534 - R80.20.20 (1869)
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This update resolves the issue with:
https://wiki.squid-cache.org/
Another one is:
https://www.sefaria.org.il/
which is missing the:
DigiCert Baltimore Root
# true|openssl s_client -showcerts -connect www.sefaria.org.il:443
CONNECTED(00000003)
depth=2 C = IE, O = Baltimore, OU = CyberTrust, CN = Baltimore CyberTrust Root
verify return:1
depth=1 C = US, O = "Cloudflare, Inc.", CN = Cloudflare Inc ECC CA-3
verify return:1
depth=0 C = US, ST = CA, L = San Francisco, O = "Cloudflare, Inc.", CN = sni.cloudflaressl.com
verify return:1
---
Certificate chain
0 s:C = US, ST = CA, L = San Francisco, O = "Cloudflare, Inc.", CN = sni.cloudflaressl.com
i:C = US, O = "Cloudflare, Inc.", CN = Cloudflare Inc ECC CA-3
-----BEGIN CERTIFICATE-----
MIIExjCCBG2gAwIBAgIQB+CHD8vdd+kG+1SK23EkJTAKBggqhkjOPQQDAjBKMQsw
CQYDVQQGEwJVUzEZMBcGA1UEChMQQ2xvdWRmbGFyZSwgSW5jLjEgMB4GA1UEAxMX
Q2xvdWRmbGFyZSBJbmMgRUNDIENBLTMwHhcNMjAwNzMwMDAwMDAwWhcNMjEwNzMw
MTIwMDAwWjBtMQswCQYDVQQGEwJVUzELMAkGA1UECBMCQ0ExFjAUBgNVBAcTDVNh
biBGcmFuY2lzY28xGTAXBgNVBAoTEENsb3VkZmxhcmUsIEluYy4xHjAcBgNVBAMT
FXNuaS5jbG91ZGZsYXJlc3NsLmNvbTBZMBMGByqGSM49AgEGCCqGSM49AwEHA0IA
BPiqegg/gbj42QMKwqiuQleDNc/5F3gZ8h5z7qzUf8yCRiPtR157Xq+Jmcxw5f3H
9Du3eTlkiPWjDRajnPqmkAyjggMQMIIDDDAfBgNVHSMEGDAWgBSlzjfq67B1DpRn
iLRF+tkkEIeWHzAdBgNVHQ4EFgQU0mL0OKunXhWSD0MAQ2pYGgougMMwQgYDVR0R
BDswOYIVc25pLmNsb3VkZmxhcmVzc2wuY29tgg5zZWZhcmlhLm9yZy5pbIIQKi5z
ZWZhcmlhLm9yZy5pbDAOBgNVHQ8BAf8EBAMCB4AwHQYDVR0lBBYwFAYIKwYBBQUH
AwEGCCsGAQUFBwMCMHsGA1UdHwR0MHIwN6A1oDOGMWh0dHA6Ly9jcmwzLmRpZ2lj
ZXJ0LmNvbS9DbG91ZGZsYXJlSW5jRUNDQ0EtMy5jcmwwN6A1oDOGMWh0dHA6Ly9j
cmw0LmRpZ2ljZXJ0LmNvbS9DbG91ZGZsYXJlSW5jRUNDQ0EtMy5jcmwwTAYDVR0g
BEUwQzA3BglghkgBhv1sAQEwKjAoBggrBgEFBQcCARYcaHR0cHM6Ly93d3cuZGln
aWNlcnQuY29tL0NQUzAIBgZngQwBAgIwdgYIKwYBBQUHAQEEajBoMCQGCCsGAQUF
BzABhhhodHRwOi8vb2NzcC5kaWdpY2VydC5jb20wQAYIKwYBBQUHMAKGNGh0dHA6
Ly9jYWNlcnRzLmRpZ2ljZXJ0LmNvbS9DbG91ZGZsYXJlSW5jRUNDQ0EtMy5jcnQw
DAYDVR0TAQH/BAIwADCCAQQGCisGAQQB1nkCBAIEgfUEgfIA8AB2APZclC/RdzAi
FFQYCDCUVo7jTRMZM7/fDC8gC8xO8WTjAAABc5/v9osAAAQDAEcwRQIhAJJaJY8P
UsfDZ4pLwYyV6n07cx2eYfWpo1lhVHagzy5MAiA4RFwktErfCDmq05x3tdOL9mCU
IjHfcNOFMlChUq68cgB2AFzcQ5L+5qtFRLFemtRW5hA3+9X6R9yhc5SyXub2xw7K
AAABc5/v9sAAAAQDAEcwRQIgJVmnFuuk4VPK8+mYMVOahtDubRywV04JvpRatYl9
vTYCIQD4tIs4TyYrZDYb8PB3a+8y+hDrfHr00zLViVsark3L8jAKBggqhkjOPQQD
AgNHADBEAiBygUy7z4CoXOVBgGXWMXv3sCb6V+6F4gabw4ASYQrvHwIgaeBgH3Sj
llg8CgcIuHQ+INUnyDS8NUnBQgZFhpl2DcU=
-----END CERTIFICATE-----
1 s:C = US, O = "Cloudflare, Inc.", CN = Cloudflare Inc ECC CA-3
i:C = IE, O = Baltimore, OU = CyberTrust, CN = Baltimore CyberTrust Root
-----BEGIN CERTIFICATE-----
MIIDzTCCArWgAwIBAgIQCjeHZF5ftIwiTv0b7RQMPDANBgkqhkiG9w0BAQsFADBa
MQswCQYDVQQGEwJJRTESMBAGA1UEChMJQmFsdGltb3JlMRMwEQYDVQQLEwpDeWJl
clRydXN0MSIwIAYDVQQDExlCYWx0aW1vcmUgQ3liZXJUcnVzdCBSb290MB4XDTIw
MDEyNzEyNDgwOFoXDTI0MTIzMTIzNTk1OVowSjELMAkGA1UEBhMCVVMxGTAXBgNV
BAoTEENsb3VkZmxhcmUsIEluYy4xIDAeBgNVBAMTF0Nsb3VkZmxhcmUgSW5jIEVD
QyBDQS0zMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEua1NZpkUC0bsH4HRKlAe
nQMVLzQSfS2WuIg4m4Vfj7+7Te9hRsTJc9QkT+DuHM5ss1FxL2ruTAUJd9NyYqSb
16OCAWgwggFkMB0GA1UdDgQWBBSlzjfq67B1DpRniLRF+tkkEIeWHzAfBgNVHSME
GDAWgBTlnVkwgkdYzKz6CFQ2hns6tQRN8DAOBgNVHQ8BAf8EBAMCAYYwHQYDVR0l
BBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMBIGA1UdEwEB/wQIMAYBAf8CAQAwNAYI
KwYBBQUHAQEEKDAmMCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5kaWdpY2VydC5j
b20wOgYDVR0fBDMwMTAvoC2gK4YpaHR0cDovL2NybDMuZGlnaWNlcnQuY29tL09t
bmlyb290MjAyNS5jcmwwbQYDVR0gBGYwZDA3BglghkgBhv1sAQEwKjAoBggrBgEF
BQcCARYcaHR0cHM6Ly93d3cuZGlnaWNlcnQuY29tL0NQUzALBglghkgBhv1sAQIw
[root@mail-125 ~]# true|openssl s_client -showcerts -connect www.sefaria.org.il:443
CONNECTED(00000003)
depth=2 C = IE, O = Baltimore, OU = CyberTrust, CN = Baltimore CyberTrust Root
verify return:1
depth=1 C = US, O = "Cloudflare, Inc.", CN = Cloudflare Inc ECC CA-3
verify return:1
depth=0 C = US, ST = CA, L = San Francisco, O = "Cloudflare, Inc.", CN = sni.cloudflaressl.com
verify return:1
---
Certificate chain
0 s:C = US, ST = CA, L = San Francisco, O = "Cloudflare, Inc.", CN = sni.cloudflaressl.com
i:C = US, O = "Cloudflare, Inc.", CN = Cloudflare Inc ECC CA-3
-----BEGIN CERTIFICATE-----
MIIExjCCBG2gAwIBAgIQB+CHD8vdd+kG+1SK23EkJTAKBggqhkjOPQQDAjBKMQsw
CQYDVQQGEwJVUzEZMBcGA1UEChMQQ2xvdWRmbGFyZSwgSW5jLjEgMB4GA1UEAxMX
Q2xvdWRmbGFyZSBJbmMgRUNDIENBLTMwHhcNMjAwNzMwMDAwMDAwWhcNMjEwNzMw
MTIwMDAwWjBtMQswCQYDVQQGEwJVUzELMAkGA1UECBMCQ0ExFjAUBgNVBAcTDVNh
biBGcmFuY2lzY28xGTAXBgNVBAoTEENsb3VkZmxhcmUsIEluYy4xHjAcBgNVBAMT
FXNuaS5jbG91ZGZsYXJlc3NsLmNvbTBZMBMGByqGSM49AgEGCCqGSM49AwEHA0IA
BPiqegg/gbj42QMKwqiuQleDNc/5F3gZ8h5z7qzUf8yCRiPtR157Xq+Jmcxw5f3H
9Du3eTlkiPWjDRajnPqmkAyjggMQMIIDDDAfBgNVHSMEGDAWgBSlzjfq67B1DpRn
iLRF+tkkEIeWHzAdBgNVHQ4EFgQU0mL0OKunXhWSD0MAQ2pYGgougMMwQgYDVR0R
BDswOYIVc25pLmNsb3VkZmxhcmVzc2wuY29tgg5zZWZhcmlhLm9yZy5pbIIQKi5z
ZWZhcmlhLm9yZy5pbDAOBgNVHQ8BAf8EBAMCB4AwHQYDVR0lBBYwFAYIKwYBBQUH
AwEGCCsGAQUFBwMCMHsGA1UdHwR0MHIwN6A1oDOGMWh0dHA6Ly9jcmwzLmRpZ2lj
ZXJ0LmNvbS9DbG91ZGZsYXJlSW5jRUNDQ0EtMy5jcmwwN6A1oDOGMWh0dHA6Ly9j
cmw0LmRpZ2ljZXJ0LmNvbS9DbG91ZGZsYXJlSW5jRUNDQ0EtMy5jcmwwTAYDVR0g
BEUwQzA3BglghkgBhv1sAQEwKjAoBggrBgEFBQcCARYcaHR0cHM6Ly93d3cuZGln
aWNlcnQuY29tL0NQUzAIBgZngQwBAgIwdgYIKwYBBQUHAQEEajBoMCQGCCsGAQUF
BzABhhhodHRwOi8vb2NzcC5kaWdpY2VydC5jb20wQAYIKwYBBQUHMAKGNGh0dHA6
Ly9jYWNlcnRzLmRpZ2ljZXJ0LmNvbS9DbG91ZGZsYXJlSW5jRUNDQ0EtMy5jcnQw
DAYDVR0TAQH/BAIwADCCAQQGCisGAQQB1nkCBAIEgfUEgfIA8AB2APZclC/RdzAi
FFQYCDCUVo7jTRMZM7/fDC8gC8xO8WTjAAABc5/v9osAAAQDAEcwRQIhAJJaJY8P
UsfDZ4pLwYyV6n07cx2eYfWpo1lhVHagzy5MAiA4RFwktErfCDmq05x3tdOL9mCU
IjHfcNOFMlChUq68cgB2AFzcQ5L+5qtFRLFemtRW5hA3+9X6R9yhc5SyXub2xw7K
AAABc5/v9sAAAAQDAEcwRQIgJVmnFuuk4VPK8+mYMVOahtDubRywV04JvpRatYl9
vTYCIQD4tIs4TyYrZDYb8PB3a+8y+hDrfHr00zLViVsark3L8jAKBggqhkjOPQQD
AgNHADBEAiBygUy7z4CoXOVBgGXWMXv3sCb6V+6F4gabw4ASYQrvHwIgaeBgH3Sj
llg8CgcIuHQ+INUnyDS8NUnBQgZFhpl2DcU=
-----END CERTIFICATE-----
1 s:C = US, O = "Cloudflare, Inc.", CN = Cloudflare Inc ECC CA-3
i:C = IE, O = Baltimore, OU = CyberTrust, CN = Baltimore CyberTrust Root
-----BEGIN CERTIFICATE-----
MIIDzTCCArWgAwIBAgIQCjeHZF5ftIwiTv0b7RQMPDANBgkqhkiG9w0BAQsFADBa
MQswCQYDVQQGEwJJRTESMBAGA1UEChMJQmFsdGltb3JlMRMwEQYDVQQLEwpDeWJl
clRydXN0MSIwIAYDVQQDExlCYWx0aW1vcmUgQ3liZXJUcnVzdCBSb290MB4XDTIw
MDEyNzEyNDgwOFoXDTI0MTIzMTIzNTk1OVowSjELMAkGA1UEBhMCVVMxGTAXBgNV
BAoTEENsb3VkZmxhcmUsIEluYy4xIDAeBgNVBAMTF0Nsb3VkZmxhcmUgSW5jIEVD
QyBDQS0zMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEua1NZpkUC0bsH4HRKlAe
nQMVLzQSfS2WuIg4m4Vfj7+7Te9hRsTJc9QkT+DuHM5ss1FxL2ruTAUJd9NyYqSb
16OCAWgwggFkMB0GA1UdDgQWBBSlzjfq67B1DpRniLRF+tkkEIeWHzAfBgNVHSME
GDAWgBTlnVkwgkdYzKz6CFQ2hns6tQRN8DAOBgNVHQ8BAf8EBAMCAYYwHQYDVR0l
BBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMBIGA1UdEwEB/wQIMAYBAf8CAQAwNAYI
KwYBBQUHAQEEKDAmMCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5kaWdpY2VydC5j
b20wOgYDVR0fBDMwMTAvoC2gK4YpaHR0cDovL2NybDMuZGlnaWNlcnQuY29tL09t
bmlyb290MjAyNS5jcmwwbQYDVR0gBGYwZDA3BglghkgBhv1sAQEwKjAoBggrBgEF
BQcCARYcaHR0cHM6Ly93d3cuZGlnaWNlcnQuY29tL0NQUzALBglghkgBhv1sAQIw
CAYGZ4EMAQIBMAgGBmeBDAECAjAIBgZngQwBAgMwDQYJKoZIhvcNAQELBQADggEB
AAUkHd0bsCrrmNaF4zlNXmtXnYJX/OvoMaJXkGUFvhZEOFp3ArnPEELG4ZKk40Un
+ABHLGioVplTVI+tnkDB0A+21w0LOEhsUCxJkAZbZB2LzEgwLt4I4ptJIsCSDBFe
lpKU1fwg3FZs5ZKTv3ocwDfjhUkV+ivhdDkYD7fa86JXWGBPzI6UAPxGezQxPk1H
goE6y/SJXQ7vTQ1unBuCJN0yJV0ReFEQPaA1IwQvZW+cwdFD19Ae8zFnWSfda9J1
CZMRJCQUzym+5iPDuI9yP+kHyCREU3qzuWFloUwOxkgAyXVjBYdwRVKD05WdRerw
6DEdfgkfCv4+3ao8XnTSrLE=
-----END CERTIFICATE-----
---
Server certificate
subject=C = US, ST = CA, L = San Francisco, O = "Cloudflare, Inc.", CN = sni.cloudflaressl.com
issuer=C = US, O = "Cloudflare, Inc.", CN = Cloudflare Inc ECC CA-3
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: ECDSA
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 2517 bytes and written 396 bytes
Verification: OK
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 256 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
DONE
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@G_W_Albrecht Yes a re-burn from a usb with the image.
Its also reset the device to factory settings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
Upgrading your GW to the new release should fix the CA issue - no need to run clean install
Thanks,
Dafna
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Should and would are different.
I will try to test this with the tech support next week or tommorow and will update.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A clean install and re-burning the device at-least 3 times and the results is that the device doesn't decrypt the traffic.
TAC and R&D claims it works for them in their environment after in mine it doesn't work and they have seen it.
It's a little bit weird to ask from me in the last 4+ month to do the work of Your company QA..
I hope it will be resolved but the product can be enhanced easily, I just don't understand how can a product sell when it doesn't work at all?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Eliezer
We have tens of thousands of happy customers so we can safely say that the product works. Yet, if you have any technical issue we are committed to resolve it.
R&D is looking into your case, and we have now escalated it internally.
we will update soon.
Thanks for your feedback
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Amir, After 4 month and only now they seem to see and replicate the issue.
I would say it's a case for a lesson to learn.
Even if you have thousands of customers happy it doesn't mean that "it works for us" is an answer...
I have more then 50k clients and this sentence that it works for us or for others is not an acceptable service answer and 4 month to get to the point which
someone admits that there is an issue that needs to be resolved.... I expect a compensation for the time I couldn't enjoy the service.
If in 30 days from the purchase of the device someone would have got to the point to say "We want to replicate your setup to resolve this issue" instead of asking me to call someone else I would have been more calm about this.
However since the reality is that it took so little time to reproduce it from the point I spoke to R&D then it forces me to really say there was a failure from your company side.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter