- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Problem with implicit rule in SMB Firewall and use...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Problem with implicit rule in SMB Firewall and use of dropbear as ssh client
Good morning,
I'm telling you my problem, let's see if someone can help me, in a backup center we have installed 2 FWs checkpoint model 1800 splunk smb, gaia embedded R80.20.35, the problem is that in the global properties there is a rule for default "image attached" and it is a frist rule and cannot be modified unless you disable it, this rule exposes services to the outside and represents a serious security problem, not if this is given by the dropbear program, but our SOC alerted of services exposed through the shodan page, can you think of how this can be changed? Is the only option is to disable that rule? Even if I put a drop rule first in the Firewalls, this rule will be implicit. Thank you all for your time.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Once again, this risk, however small, can be mitigated by setting up IP addresses for admin access. Please refer to the specific chapter in the admin guide, for example: https://sc1.checkpoint.com/documents/SMB_R80.20.50/AdminGuides/Locally_Managed/EN/Topics/Configuring...
21 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How is it a security risk? Those are management interfaces for your appliance, and only authenticated admin accounts can connect to them.
If you want to disable this implied rule, create an explicit rule with Source IPs assigned to your dedicated admin devices and put it on top of your policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Val
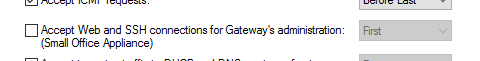
When you have enabled that rule, which is an implicit rule and in accept, they appear published for the Firewall that we have output to intenert the public IP and my security team was able to connect via web and via ssh to this firewall until it disables the rule this does not change and puts between parenthesis small office appliance, as are these models. The rule says accept web and ssh connections for administration.
My security partner was connected to the appliance from outside our infrastructure.
Or can it be due to the dropbear he has running?, The truth is that I do not understand what is happening, but if I am clear that when I disable that rule my security colleagues no longer came from outside.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Once again, I do not really understand the concern. You can actually configure the management access and disable it on the WAN interface while still allowing it from internal networks. But say someone is trying to connect to the appliance from outside your networks. There is still an authentication to do before the access is granted.
What are you trying to achieve?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your answers and your time, apparently the problem came through port 264, I have already been reading several cases about this. And the security group understood that it is normal behavior.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"Accept Remote Access Control Connections" setting is one option to negate this but due diligence is required if Check Point is used for remote access here.
As you say plenty of SK articles available on this and related topics otherwise.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I prefer not to touch that rule at the moment, if it creates confusion for me that I had to disable the other implicit rule for ssh access and web access, it is in the image of my first query, in the end I don't know if it is an appliance configuration issue. Or is it due to the firewall model, but I think switching to these appliances was not a good idea.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry like @_Val_ says I don't understand what your concern is?
These are global properties mostly irrespective of appliance model/type.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let's see how I commented in my first comment, My security group alerted me that the appliance was accessible via the web and via ssh from outside, I know that later you have to have a username and password, but there are attacks to access it. And our device came out public in shodan as vulnerable via ssh and via the web and I had to disable the implicit rule that I commented in the first post. I don't know if it is a configuration issue of the WAN interface of the equipment or why this behaviour. This device was exchanged two months ago for another checkpoint model and this did not happen with that model.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the previous model was an appliance running full GAiA that setting wouldn't have applied before.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The previous model was a checkpoint 12200, it has been changed to a splunk 1800 model with gaia embedded. Are you referring to this? I don't understand your answer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct 1800 (GAiA embedded) is classified as small office gateway hence why the setting now applies and didn't before.
(Note: Spark not splunk)
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, that's why I had to disable that implicit rule, can you think of another way so that this doesn't happen without disabling that rule? I understand that no, but I ask you, thanks for your time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Luis,
As the guys said, it is somewhat confusing what your concern here is. Just so we can help you properly, can you maybe attach simple diagram or drawing of what exactly you are trying to do? Nothing too fancy, but at least paint drawing that can help us understand this better.
If you want to keep that option off, you can follow below article, which is literally what @_Val_ indicated in his very first response:
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Change the setting to 'before last' rather than first and create rules in the policy itself per your requirements for the access behaviour you desire. But again I'm not sure why this is relevant If you don't want the access to succeed.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am sorry, but this statement is not okay: "...but there are attacks to access it". What are you referring to?
If you know how to log into the appliance without a valid account, it should be reported as a vulnerability through appropriate channels.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm sorry I expressed myself badly, I don't know any vulnerability, I mean already known methods, brute force for example.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My concern is that the topic-starter claims external access to WebUI/SSH presents a security risk and makes his system vulnerable. Open ports by themself do not actually represent a security risk unless there is a way to break in without knowing admin credentials.
Or are you asking about something else?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Once again, this risk, however small, can be mitigated by setting up IP addresses for admin access. Please refer to the specific chapter in the admin guide, for example: https://sc1.checkpoint.com/documents/SMB_R80.20.50/AdminGuides/Locally_Managed/EN/Topics/Configuring...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your response and your time. If Internet access was sectioned, I already left it configured.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My question wasn't directed at you @_Val_ sorry have clarified it some to hopefully make it clearer now.
CCSM R77/R80/ELITE
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter