Check Point has recently teamed up with Silver Peak in order to create a seamless experience for managing SD-WAN and Security.
Silver Peak is a leading SD-WAN vendor, empowering enterprises and service providers to connect users to applications while embracing broadband and delivering 10x the bandwidth for the same budget.
If you have Silver Peak Orchestrator of version 8.8.3 and above, you will find a new navigation topic Check Point CloudGuard Connect.
This means that you can now enable Check Point security from your Silver Peak management dashboard.
Step 1: Generate an API Key.
From the Check Point Infinity Portal, navigate to GLOBAL SETTINGS > API Keys. Create an API access key. Make sure that Service is set to CloudGuard Connect.
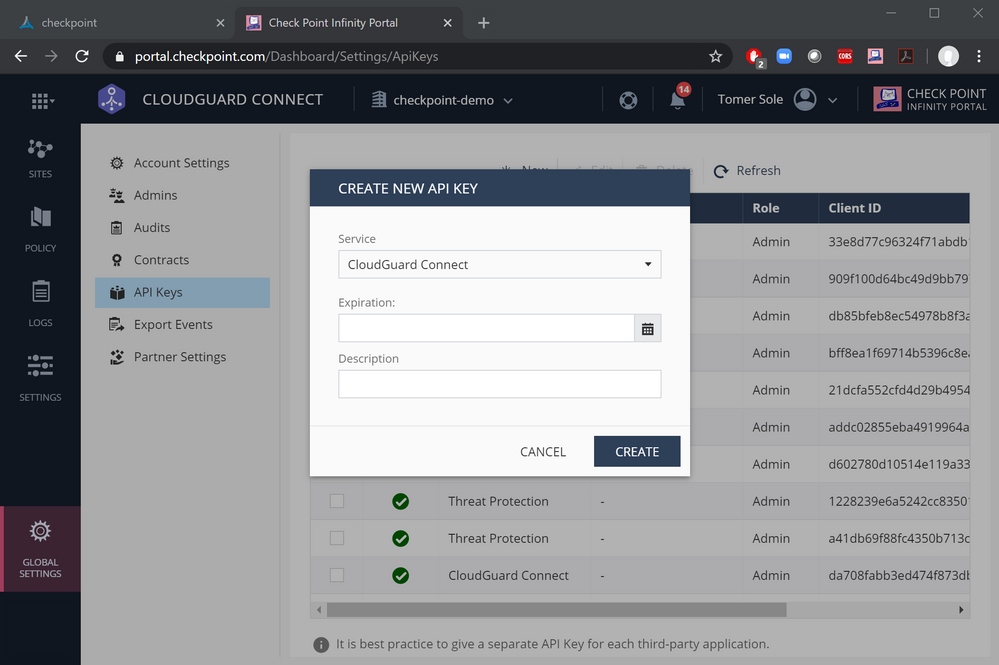
Click CREATE.
Copy the pair of Client ID and Access Key have been generated.
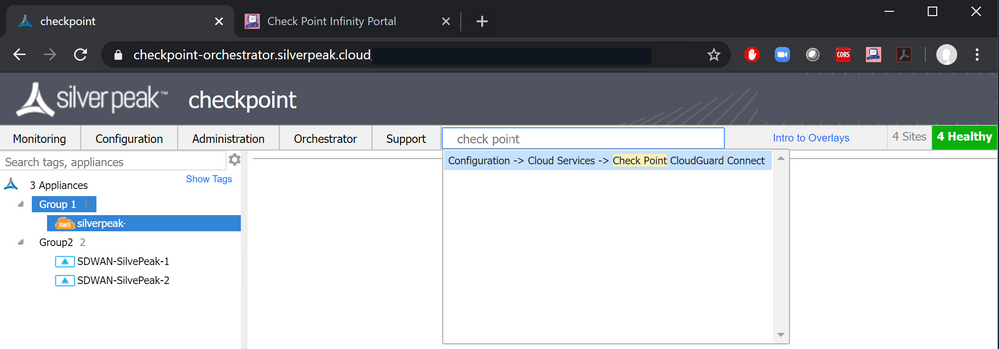
Step 2: Configure your Check Point integration
From the Silver Peak Orchestration, use the search bar in order to navigate to the page Check Point CloudGuard Connect.
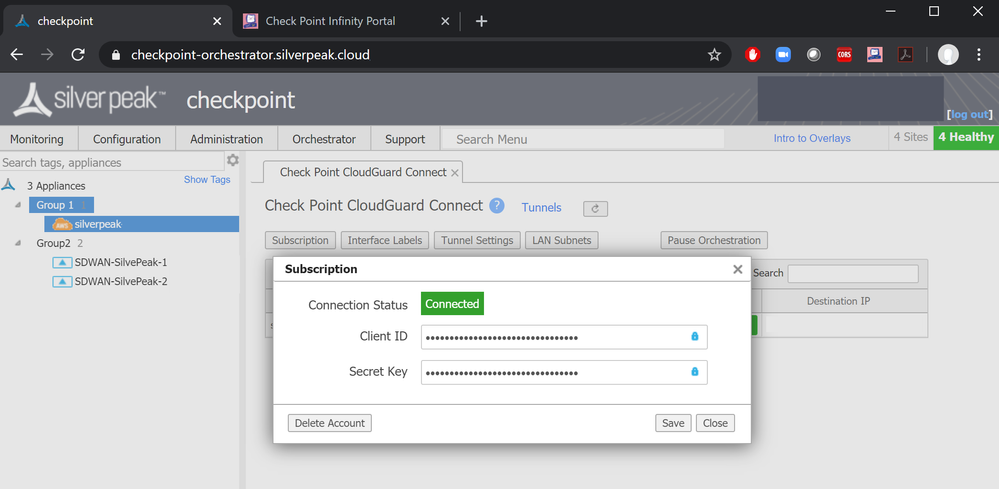
Click Subscription.
Paste the Client ID and Access Key from the previous steps.
Save your changes.
Click Interface Labels.
Silver Peak uses labels in order to create a consistent global policy across many edge devices. Any edge device that has the labels that you have selected, will eventually get Check Point automatic security.
Save your changes.
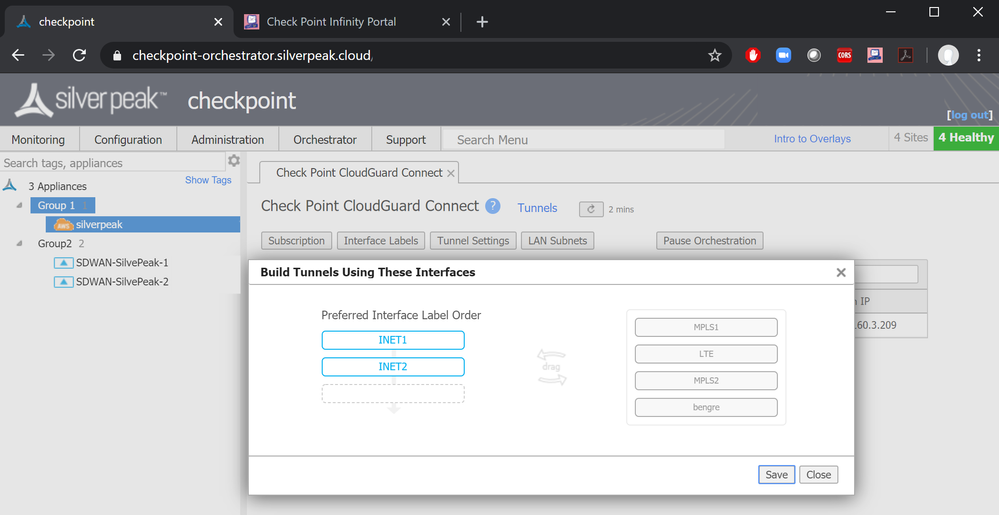
Step 3: Label your branch devices
From the Silver Peak Orchestration, select a device which you would like to have Check Point Security applied to, open its menu and navigate to Deployment.
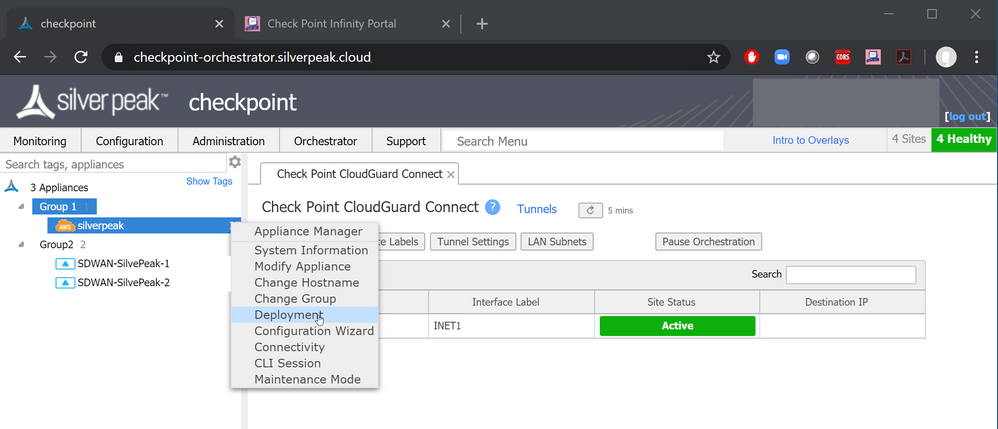
Make sure that at least one interface label that was selected as the labels for the Check Point integration, appears as part of its deployment settings.

Step 4: Configure business intent policy
From the Silver Peak Orchestration, navigate to Silver Peak's Business Intent Overlays page.
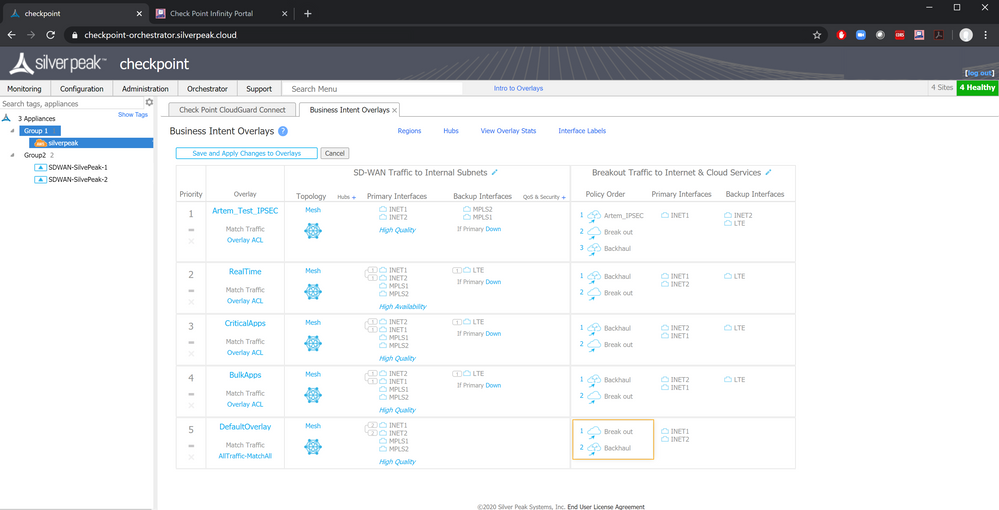
Double-click a rule which should have traffic going through Check Point Security. A pop-up dialog opens. Navigate to the Breakout Traffic to Internet & Cloud Services page.
From the Available Policies column, drag the Check Point CloudGuard option and drop it at the Preferred Policy Order column. The Check Point option is only available if you created a subscription at step 2.
Click OK.
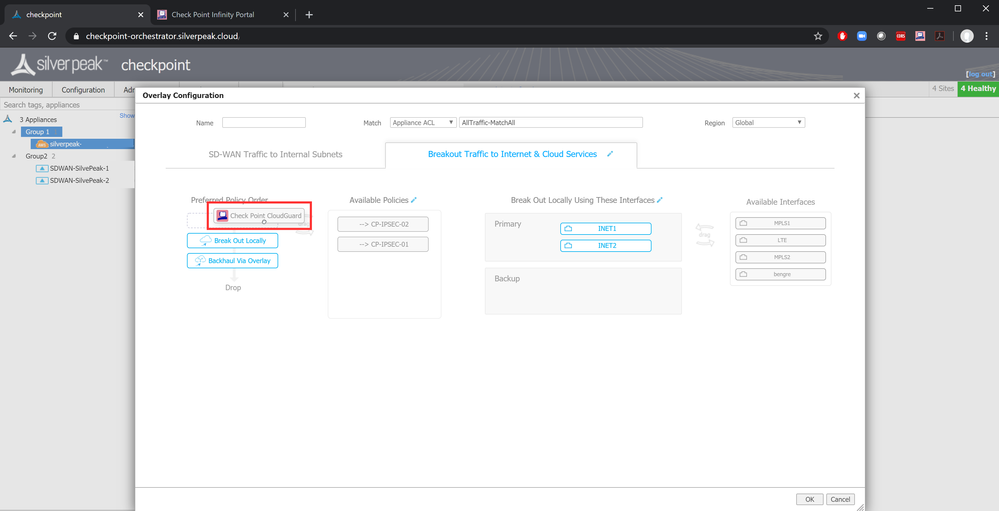
This drag-and-drop deployment is the heart of this integration. You can then repeat this process for the remaining rules at your business intent overlay policy. Please note that traffic going to Check Point will only apply for edge devices which have the specific interface labels, as set at step 2.
Once you are done, click Save and Apply Changes to Overlays.
The policy gets applied.
Step 5: Watch the magic
From the Silver Peak Orchestration, navigate to the Check Point CloudGuard Connect page.
You should now see progress of the Check Point sites being created. This could take several minutes.
Once the status changes from In Progress to Active, that means that the deployment has finished.
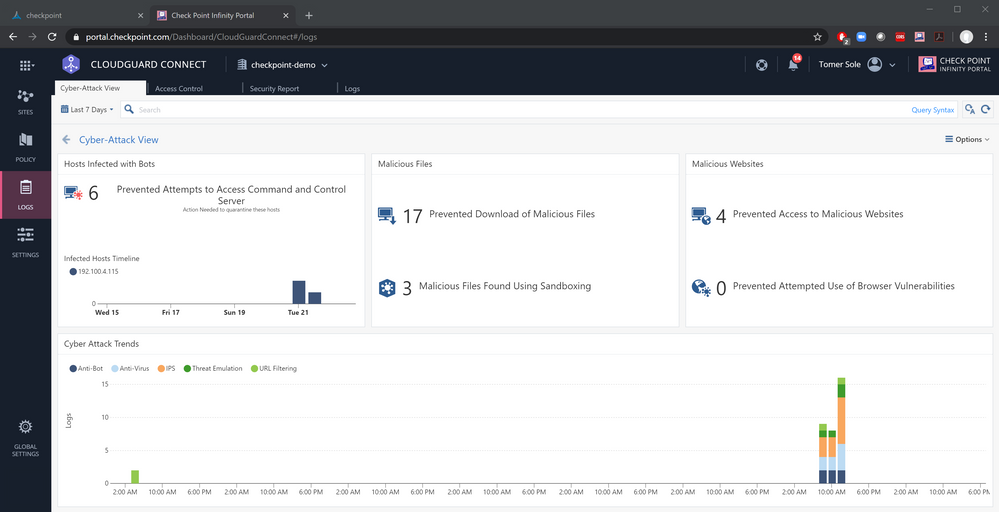
Step 6: Prevent cyber-attacks
Check Point's default policy prevents known attacks using reputation services, signatures and bot communication prevention, prevents unknown attacks using cloud-based sandboxing, over all protocols, unencrypted and encrypted. It also contains an application-aware access control policy and a web-based management for security events and log monitoring.
So this means that from the moment the sites are active, security gets applied - no intervention from the administrator is needed.
By default, all administrators get a weekly security report to their emails.
You can also access that report, as well as dashboards and traffic logs, by navigating to the Logs page at Check Point's Infinity Portal.