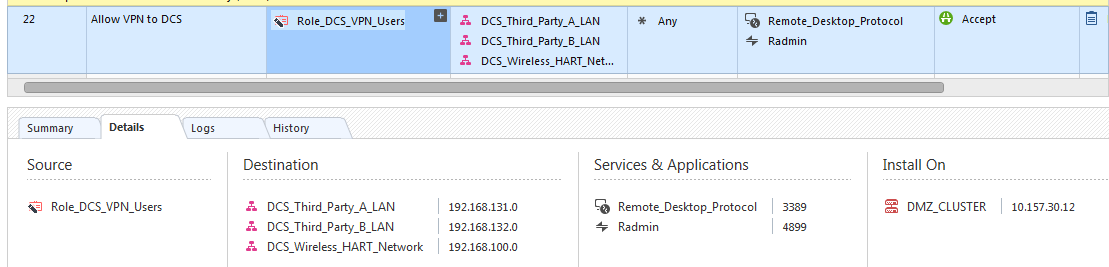
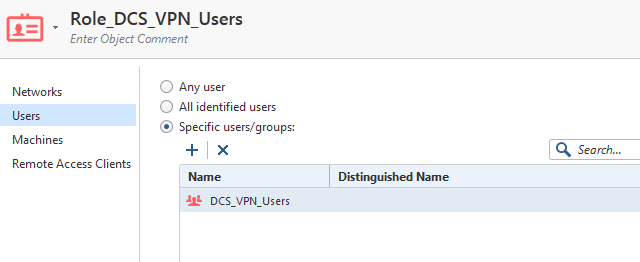
Yes, the machine is set to ‘any’ in the Role:
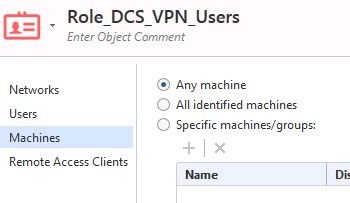
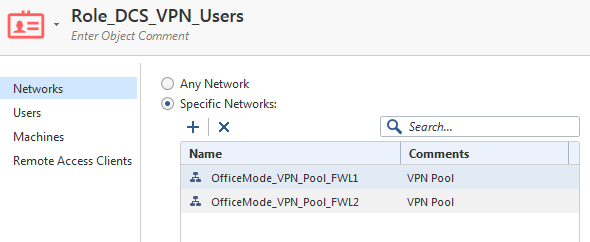
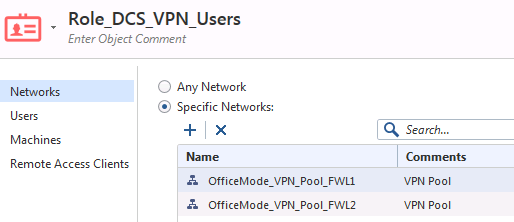
The network is set to the office mode pool(s) – but removing these and setting to ‘any network’ does not make it work.
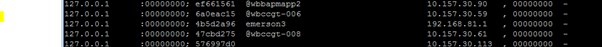
The pep show user all results are interesting:
The gateway firewall shows lots of users, all obtained from 127.0.0.1 and includes the Check Point Mobile test user for this job ‘emerson3’ and gives the IP address as the correct office mode pool address applied to this connection:
The second-line firewall has a list of users, all obtained from 10.157.30.3 (the LAN side IP address of the primary member of the gateway cluster) – all as one would expect.
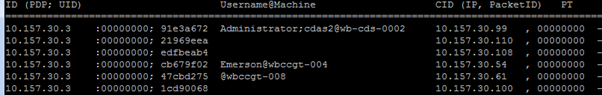
And these users are all users on the LAN who have some access *through* the second-line firewalls.
The test user (who is a local Check Point mobile user only and not an AD user) is visible on the gateway as soon as I authenticate with Check Point mobile. The first time I tested it today this user did *not* appear on the second-line firewalls.
I reverted to the old rule (allowing the whole office mode IP pool) over the weekend. Then today when I put the Role back in the rule and tested again, the second-line firewalls, displayed the test user (in pep show users all) even before I tried to access through the second-line to the secure zone.
When I did test it…it all worked!
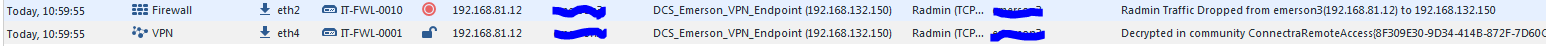
Here’s the user with its ID on the outer gateway and on the second-line:

Why did it not work before? No idea, but the ‘pep show user all’ command helped me to get to this point anyway, so thanks very much for that!
I am pleased that we have been able to pass user details from the gateway to the second-line firewalls with *NO* user capturing method on the second-line firewall other than ID sharing from the gateway cluster; this is what I hoped would work and it has!
Following your suggestion to ue that command, I looked up PEP and PDP etc. in the Identity Awareness guide and I understand the purpose of each process but I can't find what PEP and PDP stand for? It's help to know for committing it to memory.
Thanks again for your reply.