- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Understand some cases of Access Role better
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Understand some cases of Access Role better
Dear Guy!
I am configuring an Access Role for VPN Remote Access related usage.
Specifically, with Access Role there will be 4 data fields is: Networks, Users, Machines, Remote Access Clients.
Let's say I configure a Role with values.
Networks: Any
Users: User local on Checkpoint
Machines: Machine On LDAP
Remote Access Clients: Any
So if I VPN in with a user that matches the user field but the Machines are different, can I access the data according to the rule?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear @_Val_
1. You need to access the Client machine, open MMC => Certificate => Personal tab and request certificate.
2. Now there will be a certificate on the local machine and export it.
3. Finally go to Smart Dashboard and import it into trust ca server of checkpoint at https inspection.
*Note: Remember to create Trust CA object in Smartconsole with CA certificate first. After completing the above, just create an Access Role with the information you want.
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No. In your case, you are locking access for specific machines only. Clients who can authenticate but not on those specific machines, or when their machine identity cannot be checked, will not be matched to the rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So does that mean, if we use machines for Access then we only need specific machines only. And the other values not change?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct.
Note that we only acquire identities when a user generates a login event.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I’m not sure if what i am doing below is correct? i am still trying to lab it before asking customer to do it. If you have step by step, could you share with about that?
Much respect to anyone who has adopted this configuration and shared it with me. Is it necessary to use User login and AD user? or any user is fine?
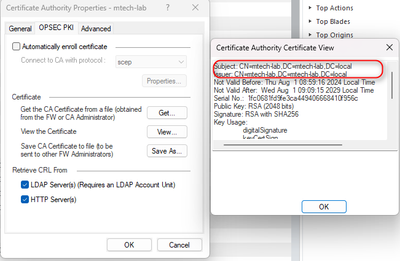
I have created a CA named mtech-lab.local and created a Trust Server CA on Check Point.
Next, I go to IPsec in Object GW and create an enroll cert, then put it in CA issue and complete on GW.
I have installed the machine and CA certificates on the local machine and in the Personal & Trusted Root Certification Authorities folders.

Next, I enabled cert authen and created a policy. I use local user created on Check Point to authenticate VPN and machine is on AD.


As a result, when VPN we still cannot connect to internal resources. When we switch Auhen Machine to Mandatory and VPN, we get an error message "Machine Certificate Is Required". This means that the Import Cert is still incorrect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Identity Awareness only works with Active Directory users.
For requirements on Machine Certificates, see: https://sc1.checkpoint.com/documents/R81.20/WebAdminGuides/EN/CP_R81.20_RemoteAccessVPN_AdminGuide/C...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you see is there config i provide above, i tried it as document you share but it not work!
Do you have configure machine authen before?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Personally? No.
Check if this SK applies: https://support.checkpoint.com/results/sk/sk175111
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I track the log file trac.log and I see it not found the cert between root CA and SMS, how can create that certificate?

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now the certificate part is passed, however. I still don't understand because no traffic still doesn't match Access Roles.I tested with 2 Test cases as follows:
Case 1:
I configure the access role with:
- Nework: 172.168.100.0/24
- User: Internal Group
- Machine: choose device from LDAP CN=DESKTOP-B1L79C9,CN=Computers,DC=mtech-lab,DC=local
After VPN we used command pdp monitor and see, it's not work if IP not match access role

Case 2:
I configure the access role with:
- Nework: 172.168.100.0/24
- User: Internal Group
- Machine: Any
After VPN we used command pdp monitor and see, this time the IP match role and traffic pass.
I'm not sure why when specific machine it doesn't match role
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have solved this problem, thanks everyone for your support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@MarcuzShinz Would you please share the solution?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear @_Val_
1. You need to access the Client machine, open MMC => Certificate => Personal tab and request certificate.
2. Now there will be a certificate on the local machine and export it.
3. Finally go to Smart Dashboard and import it into trust ca server of checkpoint at https inspection.
*Note: Remember to create Trust CA object in Smartconsole with CA certificate first. After completing the above, just create an Access Role with the information you want.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, this was for the community
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Wed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter