- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: Two ways to handle Remote Access: How seamless...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Two ways to handle Remote Access: How seamlessly can they integrate?
Hi all,
I've been struggling to find an answer to the following two questions, so hoping someone here might be able to help. I also think some of us might also have the same questions.
---
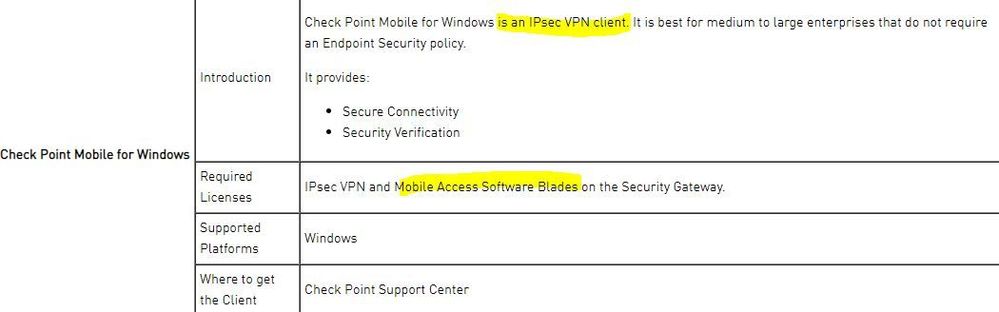
First, the easy question. As I understand it both Endpoint Security VPN and Mobile for Windows are IPSec clients that can wrap the communication to the gateway in HTTPS (aka visitor mode). Am I right in assuming that this is simply a case of IPSec over port 443 and there is no SSL involved? I am trying to work out if adding, for example, 200 extra VPN client users will have a big effect of gateway performance. If they are simple IPsec tunnels then no, but if they each need to be SSL decrypted, then that is more of an impact.
---
Second, the harder question. Imagine I have an existing deployment of Endpoint Security VPN with appropriate endpoint container licensing for VPN and FW and that I have enough licensing for 50 VPN users. Due to the COVID-19 situation I want to use the Check Point's 60-day MAB license offer for an additional 200 remote users. I understand that these extra users won't have the client FW capability as it's not part of the MAB license. Let's assume that I have obtained the 200 MAB user license from Check Point and added it.
1) Can I deploy the Endpoint Security VPN client to ALL users. I understand users connecting under MAB licensing will not get the endpoint FW capability, but I would like to keep things simple by only having a single client type deployed.
2) I now have two two remote access VPN license schemes installed (50 Endpoint containers and 200 MAB licenses). When a remote VPN user connects, which license scheme is used first? This is important as it will dictate whether the user gets the endpoint FW or not.
1) When enough remote users connect to exhaust one licensing scheme, will it automatically start using the next licensing scheme? For example, if the endpoint container scheme is used first, when the 51st user connects will it automatically see this as a MAB license?
Thanks,
Dave
31 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can find all answers in sk67820: Check Point Remote Access Solutions !
Please remember that the IP Sec VPN and MAB blade have very different licenses, so seamless integration is impossible.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I have actually been reading the sk67820 article before posting my questions, so apologies, but I don't think it answers any of my questions.
It does not specify how IPsec over HTTPS is implemented. I believe that visitor mode works by simply taking an IPsec packet, adding a TCP header and sending it to port 443. In other words is it not really HTTPS (and so does not need any form of HTTPS decryption). But I was really after some confirmation that this is right (or wrong!)
It does not specify the order in which licensing is used, if two license schemes are available. It does not specifiy anything at all about what happens when there are two valid, but different, licensing schemes in place at the same time.
And, apologies in advance (as I do not want to appear rude as it is not my intention) but when you state: "Please remember that the IP Sec VPN and MAB blade have very different licenses, so seamless integration is impossible." I am not sure you have understood my questions. I know that they two blades can function is very different ways (client vs. clientless), but that is not what I am asking. I am not talking about using MAB as a blade. I am talking about using MAB licensing to support an IPsec client and how that works with other IPsec clients using the Endpoint Security (or Sandblast basic).
Thanks,
Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
MAB does not license any IPSec VPN client at all ! We speak about two different products that have very different licensing (seat based with IPSec and concurrent with MAB). The only thing both IPSec and MAB use is OfficeMode - and that is where the seats or number of concurrent users become important !
In fact, both RA VPN client types use different licensing schemes that have no cross-dependencies at all. This situation has grown out of historic development, namely old SecureClient (IPSEc VPN) and old Connectra (predecessor of MAB) representing very different products...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
> MAB does not license any IPSec VPN client at all
Are you saying that if I only have the MAB blade enabled I cannot use a VPN client (such as Endpoint Security VPN or Mobile for Windows)? I ask as they are both IPsec VPN clients. Also, when you enable MAB, the wizard does ask if you want use the Endpoint Security VPN and Mobile for Windows clients. I am assuming that if you do use the Endpoint Security VPN client, there is no firewall policy as it isn't a MAB function, but MAB does gives you the option to use it as a VPN client.
And I do understand that the two licensing schemes are different, but it is possible to have both enabled at the same time. So, my question really is the same: when a client connects to a gateway and both MAB licensing and Endpoint containers (or Sandblast Basic) licensing is available, with is used first?
If you are right and you cannot use a client with a MAB license, then it cannot be the MAB license. But, since sk67820 states IPSec VPN clients *can* be used with MAB (see below) - and we have customers doing exactly that - I don't understand your " MAB does not license any IPSec VPN client at all" statement.
Thanks,
Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let me get back to real basics with this one
You can use Endpoint Security VPN and Mobile Access Blade on the Same Gateway.
ie One User connects with Endpoint Security VPN Client and another connects with say Capsule Connect or Check Point Mobile for Windows Client.
However they use different licenses.
So if you have 50 Endpoint Security VPN Licenses and a 200 Seat MOB license then then you can have 50 Endpoint Security Users and 200 MOB Users connected to the Same Gateway at the same time
However what it won't do is take a 51st Endpoint Security VPN Client Connection and use a Spare MOB license for that user.
It won't take the 201st MOB Connection and use a spare Endpoint Security VPN licensse to allow to connect.
So you can use both at the same time but they won't use others licenses.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
> Let me get back to real basics with this one
Yes, at least then there is little room for confusion.
> You can use Endpoint Security VPN and Mobile Access Blade on the Same Gateway.
> ie One User connects with Endpoint Security VPN Client and another connects with say Capsule Connect or Check Point
> Mobile for Windows Client.
> However they use different licenses.
Yes, agree completely - as I have been saying exactly this in my previous posts.
> So if you have 50 Endpoint Security VPN Licenses and a 200 Seat MOB license then then you can have 50 Endpoint Security
> Users and 200 MOB Users connected to the Same Gateway at the same time
Again, completely agree - I have been saying this too in my previous posts.
> However what it won't do is take a 51st Endpoint Security VPN Client Connection and use a Spare MOB license for that
> user.
> It won't take the 201st MOB Connection and use a spare Endpoint Security VPN licensse to allow to connect.
Are you sure? I mean - do you really know this for certain?
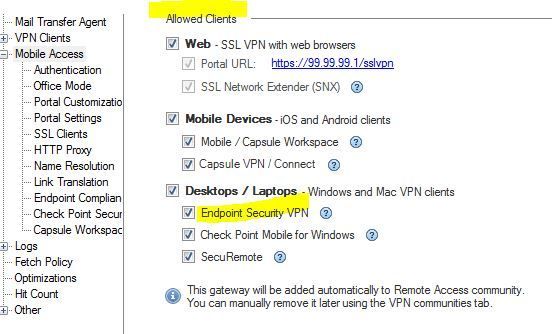
The reason I ask is one (1) The Mobile Access Blade configuration explicitly allows you to use the Endpoint Security VPN client with MAB licensing - see screenshot below:
(2) it allows you to connect to a gateway with only the MAB blade ticked and SSLVPN licensing (and no IPSec blade and no Sandblast Basic or Endpoint container licensing).
As I have stated in previous posts, I am not asking whether an Endpoint Security VPN client will get the FW functionality if connecting via MAB licensing - of course it won't.
What I am asking given that the MAB blade clearly supports the use of the Endpoint Security VPN client and counts such a connection again the MAB license and given that I have a 50 seat endpoint container license then:
(1) which licence is used first and
(2) is the product "clever" enough to realise that it has two licensing schemes, both capable of allowing an Endpoint Connect VPN client and so automatically start counting new clients towards the second license once the first is depleted?
Thanks,
Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is a reason why specifically separated Endpoint Security VPN and Mobile for Windows.
Endpoint Security VPN is an IPSec VPN Client that uses the VPN Blade from the Endpoint Suite Licenses, ie the Suite that has FDE, MEPP, Sandblast Agent etc. It does NOT use MOB licenses even if trying to connect to a Gateway without the Desktop Security configured. It does not connect to the Mobile Access Blade but connects to the IPSec VPN Blade.
If you are using the Endpoint Suite then you won't be using the Endpoint Security VPN Client as that is the Standalone VPN Client, but does use the same license as the Endpoint Security VPN.
Mobile for Windows is a VPN Client that terminates against the Mobile Access Blade and uses MOB license. It won't use a Remote Access VPN Client License.
As has been pointed out lower down it is the same installation file but gives you different client.
There is also the 3rd Option of SecuRemote that requires no Client License but has not Office Mode.
All 3 are the same install file but will give you different clients
When you enable the Mobile Access Blade then it also has to have the IPSec VPN Blade enabled and be a part of the Remote Access Community.
So if rolling out the client then ensure that installing as Mobile for Windows and then they will use the MOB license
At that point you are installing Mobile for Windows and NOT the Endpoint Security VPN product (even though is the same installation file)
At this point the the Gateway will respond to Remote Access IPSec VPN Client connections such as Endpoint Security VPN or SecuRemote or even the VPN part of the Endpoint Suite, you just have to create rules
So if on your laptop you install Endpoint Security VPN and connect to the Gateway then it will look for a VPN license.
If you install the Mobile for Windows and connect to the Gateway then it will look for a MOB License
Even though are the same installation file.
Endpoint Security VPN Client is licensed per Seat ie deploy 200 client then you should have a 200 license even if only 50 at a time connect.
Mobile for Windows using MOB is licensed per Concurrent Connections so if deploy 200 seats but never have more then 50 connect at a time then you only need a 50 license
Whilst the same installation file they give you different clients with different termination points and different license requirements.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
> It does NOT use MOB licenses even if trying to connect to a Gateway without the Desktop Security configured.
I understand what you are saying but (and apologies in advance for saying) I think you're misunderstanding the process that is occurring. I am not saying that I am right, but all I can report is what I'm seeing in debugs and what you say is not what we are seeing. Can you point me in the direction of where this is documented please?
I am beginning to suspect that, due to how the two licensing options for a VPN client are 'sold' that this is where a lot of the confusion is coming from. I'll try and explain (I say 'try' as I am trying to understand all of this myself), but - again - we are NOT using the desktop firewall. We are using the VPN tunnel and OM addressing.
This all seems to be related to what one of our endpoint guys has been saying which is: when a client connects to a gateway and established a VPN tunnel with either the Endpoint Security VPN or the Mobile for Windows clients, it does not look for a MAB license or a Endpoint container license - all it looks for is whether there is a free office mode address available. As we all agree upon, the available office mode address space can be provided by either the MAB license or the endpoint security container/sandblast license, or potentially both.
When a Mobile for Windows user connects in, this is not shown as a MAB user, but it is shown as a OM license being consumed. The same is true when a Endpoint Security VPN client connects into to a gateway without policy server, but with MAB enabled and the SSLVPN license component - another OM address being consumed, but this is not seen as a MAB user.
So, that is why I disagree with your statement. Rather I do agree with it, but it is an invalid in this case. I agree with you because I think you are right: an Endpoint Security VPN client will not use a MAB license. But that is irrelevant as neither does a Mobile for Windows client. You can easily see this when you try connecting with either client with only the MAB blade enabled - the MAB user count does not increment. What they are really using is the OM address space that a MAB or endpoint container license provides and you can see this is various place, including a VPN debug.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check Point Mobile (which is the Endpoint VPN Client without the Desktop Firewall) can be used with MAB licenses and is tracked based on concurrent connected users.
Check Point Mobile can operate as IPsec or SSL VPN (Visitor Mode).
SNX is the same deal except it uses Visitor Mode only (I believe).
The Full Endpoint VPN client uses Endpoint licenses and is licensed based on number of installed clients (not necessarily connected ones).
Full Endpoint VPN clients should never use MAB licenses.
Likewise, Check Point Mobile/SNX will never use full Endpoint licenses.
Hope that clears things up.
Check Point Mobile can operate as IPsec or SSL VPN (Visitor Mode).
SNX is the same deal except it uses Visitor Mode only (I believe).
The Full Endpoint VPN client uses Endpoint licenses and is licensed based on number of installed clients (not necessarily connected ones).
Full Endpoint VPN clients should never use MAB licenses.
Likewise, Check Point Mobile/SNX will never use full Endpoint licenses.
Hope that clears things up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To be honest, no. When you refer to full Endpoint client, I'm thinking you mean VPN with FW, correct? If so, this is exactly what I am NOT meaning. I mean to use the Endpoint Security VPN client as VPN only.
But you do raise an interesting question. You mention that Mobile for Windows can act as IPsec or SSL VPN (visitor mode). Is this implying that Mobile for Windows in Visitor mode is actually a full SSL VPN tunnel as I was told differently by our Check Point SE. I thought that visitor mode only added a TCP packet to IPsec data and used port 443, but was not actually "real" SSL. Are you saying it is?
Also, it you cannot use the Endpoint Security VPN client. why is is even an option the MAB configuration pane on the gateway object, let alone is actually work. Again I am NOT wanting FW functionality, simply a VPN tunnel.
Thanks,
Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Full Endpoint client includes the firewall, Check Point Mobile doesn't.
For Windows, it's the same installation package for both, with the difference being which option you choose on installation.
I'm not familiar with how Visitor Mode is actually implemented at the protocol level.
"It is implemented by adding additional encapsulations to the traffic" according to the following SK:
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
A protocol analyzer on the necessary traffic will probably tell you for certain what it's doing.
And yes, you can use the Endpoint Security VPN client with MAB if you have a full Endpoint license.
What the client will use license-wise is determined by which option was chosen on install.
For Windows, it's the same installation package for both, with the difference being which option you choose on installation.
I'm not familiar with how Visitor Mode is actually implemented at the protocol level.
"It is implemented by adding additional encapsulations to the traffic" according to the following SK:
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
A protocol analyzer on the necessary traffic will probably tell you for certain what it's doing.
And yes, you can use the Endpoint Security VPN client with MAB if you have a full Endpoint license.
What the client will use license-wise is determined by which option was chosen on install.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there a reason you are calling it the "full Endpoint client" as opposed to the Endpoint Security VPN client - specifically is there a reason on you keep using the word "full"?
I ask is, as whilst the Endpoint Security VPN license does include the necessary code to implement a client-side firewall, it is not mandatory and I was under the impression that it was disabled internally upon the VPN being established and no policy server being defined. In other words, it might still be *called* the Endpoint Security VPN client but it would then actually be functioning as the Mobile for Windows client. I'm not sure I can find the SR number where I wnet through this with TAC as it was years ago but it sounds like you are saying that this was incorrect?
As for your comment: "you can use the Endpoint Security VPN client with MAB if you have a full Endpoint license.
What the client will use license-wise is determined by which option was chosen on install." I'm sorry but that makes no sense and does not match what we've seen in the lab, or on customer sites. From what you are saying then, if an Endpoint Security VPN license connects, it will look for either a Sandblast license or an endpoint container license and if it does not find them, it will not work. But it doesn't do that , or at least it might first look for those licenses, but it will also work with a MAB license. This has been tested.
I was talking to one of our Endpoint guys and the theory is that this is more to do with there being sufficient office mode addresses licenses available. And as OM is a feature of both MAB licensing and Endpoint container/Sandblast licensing, then the client (which only wants a VPN tunnel) is simply happy to have available OM addressing.
And once again I stress that this is without the FW blade on the endpoint client. I mentioned this again as I'm getting the impression from the replies that people think Endpoint Security VPN = FW. It doesn't. The firewall is an option; not mandatory.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're absolutely correct in that that firewall is "optional" on the "full" Endpoint Security VPN client.
I should have been more precise.
If you're not using the Desktop Firewall feature and the Endpoint VPN client connects, where only a VPN tunnel is configured, I can see how it can potentially act as "either or" depending on what license(s) are available.
Will have to clarify which is used first.
Note that Endpoint Security VPN clients on a Mac will always use the Endpoint VPN license.
They cannot use the Mobile Access Blade licenses except with the SNX client.
I should have been more precise.
If you're not using the Desktop Firewall feature and the Endpoint VPN client connects, where only a VPN tunnel is configured, I can see how it can potentially act as "either or" depending on what license(s) are available.
Will have to clarify which is used first.
Note that Endpoint Security VPN clients on a Mac will always use the Endpoint VPN license.
They cannot use the Mobile Access Blade licenses except with the SNX client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm guessing that's because there is no client in the "Endpoint" part of the suite that terminates on MAB for Mac?
I.E. there's no "Check Point Mobile" for Mac clients, other than SNX which is something rather different and deployed/accessed differently.
Whereas the VPN functionality that is in the Endpoint client for Windows, has the ability to terminate on MAB "in-house" based on how it's installed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To make the confusion complete, Endpoint Security VPN Client (!!!) has three modes of installation out of the same Win .exe, find details in Changing the Standalone Remote Access Client flavo...:
- Endpoint Security VPN including Desktoip FW
- Mobile Endpoint Client (SSL for MAB)
- SecuRemote VPN client (without OfficeMode, works without license !)
Interestingly, the first variant uses EP RA IPSec VPN licensing by seats, the second SSL VPN MAB concurrent licensing and the third needs no license at all 8)!
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think the confusion is, in part, as the names used are quite similar.
The is no "Endpoint Security VPN client" installable as you suggest. There is a "Endpoint Security" installable that does indeed have three deployment options: Endpoint Security VPN; Mobile for Windows and SecuRemote.
I would also want to clarify your next statements:
> Endpoint Security VPN including Desktoip FW
Endpoint Security VPN includes the ability to enforce an optional desktop FW. It is an IPsec client and provides office mode address assignment. If using the optional desktop firewall, it requires an IPsec gateway license and either endpoint container licensing (VPN + FW) or Sandblast client licensing and is licensed per-seat. If not using the optional desktop firewall, it uses MAB licensing and is licensed per-connected-user.
> Mobile Endpoint Client (SSL for MAB)
Mobile for Windows offers VPN connectivity only. It is an IPsec client and provides office mode address assignment. It requires a IPsec gateway license and MAB gateway license. If a cluster, MAB licensing must be on both cluster members. It is licensed per-connected-user.
- SecuRemote VPN client (without OfficeMode, works without license !)
SecuRemote offers VPN connectivity only. It does not provide office mode address assignment and so can cause users issues if used with more than a small number of VPN users. It requires an IPsec gateway license. There are no licensing restrictions on the number of users.
To clarify the two terms: "per-seat" and "per-connected-user". Per seat means that, if you have 1500 potential remote access VPN users you need 1500 licenses, even if only at most 200 are connected one one time. Per connected user means that with 1500 potential users, you only need to buy licenses for 200 tunnels if that is the most that connect at one time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So you did find your answers at last !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, this is all information I already knew before asking here. My questions - that I have been asking since the original post - are still unanswered.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right there is no such thing as "Check Point Mobile" for Mac, only Windows.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PhoneBoy , yes, please can you check which license would be used first in this situation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
MAB licenses should get used first in this situation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah thanks for persisting on this.
Am I right in thinking that this only works because both license types provides access to the OM address space and that is what is being checked here?
I ask as, whilst knowing it will work it good, it would be nice to know *why* it works. As mentioned in previous posts, I think it is the presence of OM availability that is being checked, not necessarily where that availability came from. But it would be nice to get some confirmation on that.
Thanks,
Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suppose the other - perhaps more relevant question is this: If I have an existing deployment of Endpoint Security VPN *with* desktop policy enabled, and I want to then add 200 Mobile for Windows clients, do the two co-exist?
For example, I'm using Endpoint Security VPN with desktop firewall for key users and so use the desktop policy to assert access control on their device (as they connect to sensitive parts of the network), but for my general users using Mobile for Windows clients, I don't need a desktop firewall as they only have access to a small part of the internal network.
When a client connects, is the gateway 'clever' enough to work out how to validate licensing for each client type?
Thanks,
Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The question is: what is terminating the client VPNs?
If its Mobile Access Blade (i.e. this is enabled), then those licenses should apply first.
If it's IPSEC VPN only (MAB disabled), then the answer is...less clear, it turns out.
Ideally, it would always use the correct license depending on the client that is connecting.
However, I want to have someone test this to confirm.
If its Mobile Access Blade (i.e. this is enabled), then those licenses should apply first.
If it's IPSEC VPN only (MAB disabled), then the answer is...less clear, it turns out.
Ideally, it would always use the correct license depending on the client that is connecting.
However, I want to have someone test this to confirm.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The answer is... both aspects can terminate the VPN. The IPsec VPN + Pol Srv *and* the MAB blades are enabled and a desktop policy defined. Reason being Endpoint Security VPN has always been deployed for a small number of tech support staff, but want a solution in places for the wider population for general use - and situation like we have now - where they need a lot of people to work from home.
The idea of using MAB and Mobile for Windows for the "general population" has come from the more cost effective licensing and the MAB + Mobile for Windows client giving them exactly what they need for the user population.
If this can be tested/verified that'll be great.
Thanks,
Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Phoneboy,
any tips to verify and manage license used seats?
i'm struggling into a customer with CPVP-VSC-5-NGX+<N> license, using Endpoint client, no desktop policy and no policy server, so i cannot understand who and how many "seats" are used... i suspect that that "seats" are working in per-concurrent session manner
just to add confusion, into https://support.checkpoint.com/results/sk/sk84560, it declares that As a user connects, they are given an Office Mode IP valid for 30 days.. i cannot see this behavoir and i cannot understand what it means in relation to licensing...
adding @Dave_Hoggan it seems he fighted a lot with this...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I recall, those SKUs are old "Secure Client" licenses.
These should use Endpoint Security VPN (not full Harmony Endpoint).
In any case, the tool here can help with this: https://community.checkpoint.com/t5/Scripts/Easy-Mobile-User-License-Tool-Replaces-quot-dtps-lic-quo...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you remember if they work per-cuncurrent sessions?
Watching to logon logs i think so, also because it seems there is no way to check available licenses in case per-seats approach is used (no smartendpoint emabled)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
They are per-seat licenses (30 days, similar to Harmony Endpoint).
The tool I liked above should should counts of licenses (what you have versus what is in use).
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter