- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- StandAlone Gateway Remote Access VPN Site not crea...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
StandAlone Gateway Remote Access VPN Site not created
Hello All,
I am trying to configure a RemoteAccess VPN on a standalone gateway, But something fundamental is going wrong.
Is there something specific you need to do for configuring Remote Access VPN on a Standalone gateway?
I have a Checkpoint 3000 series on R80.40 straight out of the box. When I configure the RemoteAccess VPN and try and connect with the SecureRemote client. I always end up with the error "Failed to create the new site. Site is not responding"
I have been through the community looking for tips. I have been through sk128652: Troubleshooting "site is not responding" Issues
- Sceanrio 1 - Done
- Scenario 6 - Already done, reset to factory defaults
- Scenario 7 - Done
- Scenario 8 - Done / Checked
- Scenario 9 - Already on R80.40
Checking in the trac.log as was suggested I see "Failed to connect - AuthError_t==3"
[ 7668 20200][3 May 13:53:23][cpwssl] cpWinSSL_fwasync_end_handler: 0x32E4048 ended
[ 7668 20200][3 May 13:53:23][cpwssl] cpWinSSL_fwasync_connected: SSL failure: not initialized.
[ 7668 20200][3 May 13:53:23][cpwssl] cpWinSSL_fwasync_close: closing - conn - 0x32e4048
[ 7668 20200][3 May 13:53:23][] fwasync_close: close(2492): Unknown Winsock error (10038)
[ 7668 20200][3 May 13:53:23][talkssl] talkssl::end_handler: ending connection
[ 7668 20200][3 May 13:53:23][talkhttps] ATalkHttps::ssl_failure_cb: SSL ended. err=1
[ 7668 20200][3 May 13:53:23][talkhttps] ResetRcvBuffer: data 00000000 size 0 free_buffer=1.
[ 7668 20200][3 May 13:53:23][TalkCCC] talkccc::EndEv: got disconnected with AuthError_t==3.
[ 7668 20200][3 May 13:53:23][TalkCCC] talkccc::EndEv: connection status 1
[ 7668 20200][3 May 13:53:23][TalkCCC] talkccc::EndEv: Failed to connect - AuthError_t==3
[ 7668 20200][3 May 13:53:23][TalkCCC] talkccc::EndEv: event callback is registered. Notifying it
[ 7668 20200][3 May 13:53:23][TR_FLOW_STEP] TR_FLOW_STEP::TrSiteCreationStep::AuthFailureEv: entering...
[ 7668 20200][3 May 13:53:23][String] String::String::Translate: String with id 28 has been translated to string: Site is not responding
[ 7668 20200][3 May 13:53:23][TR_FLOW_STEP] TR_FLOW_STEP::TrSiteCreationStep::Notify: Failed to receive hello reply
[ 7668 20200][3 May 13:53:23][auth_server] AAuthServer::Stop Stopping Authentication
[ 7668 20200][3 May 13:53:23][talkhttps] ATalkHttps::CloseConn: Close SSL conn: 0 State 0x6 Reason: Termination.
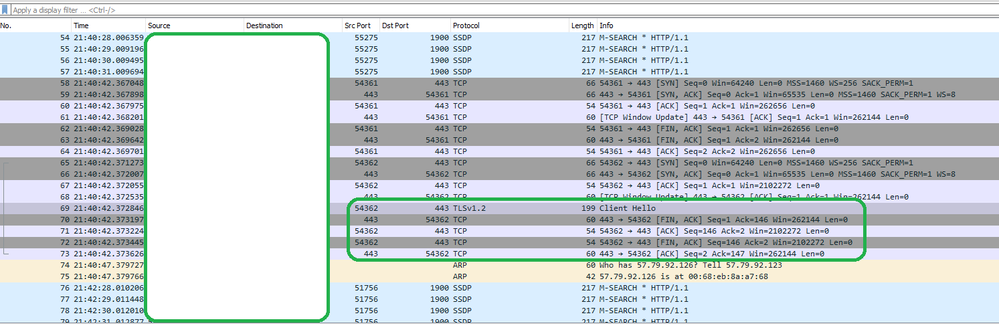
It was suggested this indicates a problem with the a certificate authentication. This makes sense as the only traffic I am seeing on the firewall is TCP/443.
What is also interesting is the message in the trac.log: [TR_FLOW_STEP] TR_FLOW_STEP::TrSiteCreationStep::Notify: Failed to receive hello reply.
A wireshark trace on the client PC is that there is a Hello, sent from the client, but immediately after that the Security gateway sends a FIN ACK packet.
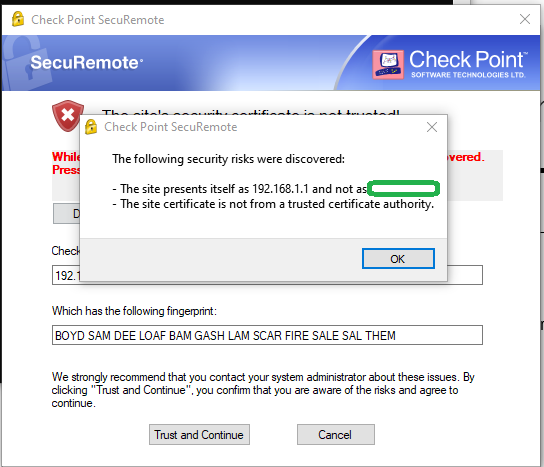
When the SecureRemote client connects there is a certificate warning:
This is showing the certificate with the IP 192.168.1.1, which was the original management IP when the firewall was taken out of the box, but is not the current management IP after running the first time wizard. In the gateway object under VPN, this certificate does not mathc what is show as the defaultCert in the Certficate repository.
The vpnd.elg does not provide much information:
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_trap_handler_multik: called dlen 104, type 2
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] CptlUrlf::HandleTrap: _len 104 _instance =1
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] CptlUrlf::HandleTrap: not urlf ssl trap.
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_urlf_trap_cb: it is not ssl urlf trap.
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_trap_handler_multik: called from kernel instance 1.
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_handle_msg_multik: called. msg=HS_NEW
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_handle_msg_multik: kernel_instance: 1
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_hs_new_handler: client_conn_id: 0x0000000000000002
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_hs_new_handler: server_conn_id: 0x0000000000000000
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_ChannelTable::startNewChannel: kernel_instance = 1, client_params_id = 0, server_params_id = 0, disable_http2 = 0
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_ChannelTable::startNewChannel: invalid args
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_hs_new_handler: startNewChannel failed
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_ChannelTable::getErrorString: channel was deleted: 0x0000000000000002
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_call_rl_end_psl: called, is_psl: 0
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_call_rl_end_psl: connID: : 0x0000000000000002
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_send_ioctl_multik
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_send_ioctl_multik: called with conn_id: 0x00000002
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_send_ioctl_multik: will call instance: 1
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_send_ioctl_multik: fwioctl_multik succeeded
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_ChannelTable::getErrorString: channel was deleted: 0x0000000000000000
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_call_rl_end_psl: called, is_psl: 0
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_call_rl_end_psl: connID: : 0x0000000000000000
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_send_ioctl_multik
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_send_ioctl_multik: called with conn_id: 0x00000000
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_send_ioctl_multik: will call instance: 1
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_send_ioctl_multik: fwioctl_multik succeeded
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] getRenegParams: lookup for key : <IP removed, 54565, IP removed, 443, 6>
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] getRenegParams: Params not found
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] storeRenegParams: storing key : <IP removed, 54565, IP removed, 443, 6>
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] storeRenegParams: added.
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_handle_msg_multik: done. msg=HS_NEW
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_trap_handler_multik: trap processing took 0.000808 seconds.
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_trap_handler_multik: called dlen 244, type 2
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] CptlUrlf::HandleTrap: _len 244 _instance =1
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] CptlUrlf::HandleTrap: not urlf ssl trap.
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_urlf_trap_cb: it is not ssl urlf trap.
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_trap_handler_multik: called from kernel instance 1.
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_handle_msg_multik: called. msg=HS_EVENT_HANDLER
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_handle_msg_multik: kernel_instance: 1
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_handle_msg_multik: conn_id: 0x0000000000000002
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_ChannelTable::handleMsg: kernel instance: 1
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_ChannelTable::handleMsg: channel conn_id: 0x0000000000000002
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_ChannelTable::handleMsg: channel could not be found: 0x0000000000000002
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_handle_msg_multik: handleMsg rc=-999
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_ChannelTable::getErrorString: channel was deleted: 0x0000000000000002
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_call_rl_end_psl: called, is_psl: 0
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_call_rl_end_psl: connID: : 0x0000000000000002
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_send_ioctl_multik
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_send_ioctl_multik: called with conn_id: 0x00000002
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_send_ioctl_multik: will call instance: 1
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_send_ioctl_multik: fwioctl_multik succeeded
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_ChannelTable::shutDown1Side: called. kernel instance: 1
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_ChannelTable::shutDown1Side: conn_id: 0x0000000000000002
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] removeChannel: not found, conn_id: 0x0000000000000002
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptls_handle_msg_multik: done. msg=HS_EVENT_HANDLER
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32][CPTLS] cptlsd_trap_handler_multik: trap processing took 0.000435 seconds.
[vpnd 10134 4081866688]@JTIMSLABCP01[3 May 21:46:32] kmsg_read_local: 2 kmsgs handled
Nothing appears in the FW logs except the HTTPS connection, which are accepted. THer eis not indication of any blocked or dropped.
Many thanks,
Michael
5 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello All,
I have tested this using VMs on my laptop and RAS VPN functions without issues in all the tested configurations (cluster + Dedicated mgmt, Gateway + dedicated mgmt, and standalone gateway). Only on the physical gateway it is not working. The only difference I can see it that when deploying the VMs, I go thorugh the set-up configuration on the console to set the management IP, disk space etc, before doing the First Time Wizard. On the physical Gateway go straight from the rest to factory defaults to running the first-time wizard.
Regards,
Michael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is definitely a cert issue here. Try recreating a VPN certificate. Also, are you using IPsec VPN or Mobile Access blade?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I am using the IPsec Blade.
I have already tried renewing the VPN certificate using process in Scenario 1 from the sk128652: Troubleshooting "site is not responding" Issues:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The solution is about renewing CA certificate, actually, not just the VPN certificate.
That said, I would suggest opening a TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the clarification between internal CA and VPN cert. I will check.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter