- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Policy Insights and Policy Auditor in Action
19 November @ 5pm CET / 11am ET
Access Control and Threat Prevention Best Practices
Watch HereOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: Preventing users from disconnecting remote acc...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Preventing users from disconnecting remote access VPN client
Hey guys,
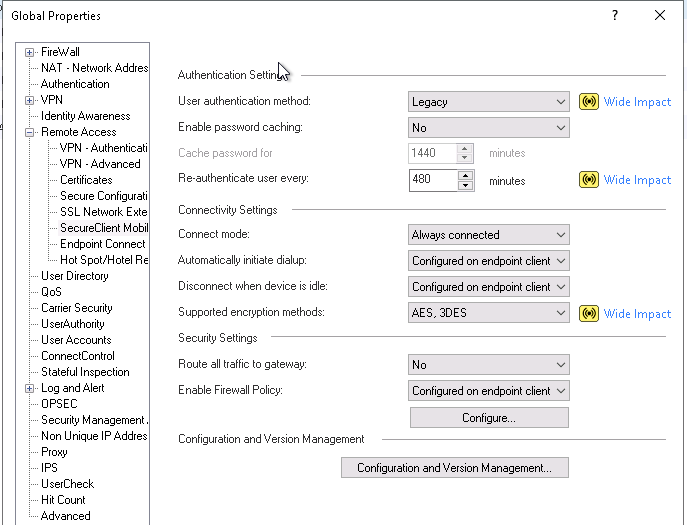
I know this may sound like a silly question, but not sure if its even possible. I know in dashboard, under global properties you can enable always connect for endpoint clients...BUT, is there any way at all, either for endpoint vpn or sandblast, to actually PREVENT people from disconnecting their vpn session once they connect?
I know there is trac_client_1.ttm file on the firewall where certain endpoint stuff can be modified, but I dont think there is anything for this specifically. Also, trac_defaults on client side has some settings too, but not sure this is one of them.
Thoughts? : )
Andy
Best,
Andy
Andy
23 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A possible workaround could be the use of machine certificate RA VPN, connecting automatically before Domain Logon - but you would have to somehow disable the GUI, as the client otherwise is able to disconnect or shutdown the RA client.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hm...thanks Gunter. Not sure if customer would be okay with that, but do you think its complicated to do?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had customers using it as a special HF from local SE and contacted me for the latest version, and since GA, i have never heard any complaint or trouble with this feature. Test it8). And try to figure out how to disable the GUI.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I knew how to do it, would not be posting here, trust me LOL...anyway, let me open TAC case for it.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you can figure out how to disable the GUI, you could leave it with that and Always Connected. I have some experience and would not know how to do it but with an OS hack.Usually, customers want safety for connections first and accept that users disconnect from VPN if they do not use its services. But the idea is valid: all connections from the client go thru company site (and its GW), CP included that a long time ago. But clients can disconnect (to print on their own printer)...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"Always Connected" is a Global Properties setting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A client always can disconnect from VPN or shutdown the client - any way to make this unavailable ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right, thats what this customer is looking for...Personally, I never heard of anyone being able to do so.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey D,
Yes, Im very familiar with that setting, but thats not what Im looking for. Customer wants to PREVENT users from being able to manually disconnect the vpn client themselves.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That plus ATM mode (removing the GUI) would make it a little more difficult for users to disable the VPN (without knowing the CLI command).
You could also create a disconnected desktop policy that blocks most everything when not connected to the VPN, thus nudging people to keep the VPN on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh yes, i forgot ATM mode !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is probably as good as you're going to be able to get. After all, users could just unplug the computer from their network, unplug their Internet connection, or otherwise block the system's ability to talk to the VPN endpoint.
While I'm not sure I understand why anybody would want to prevent users from disconnecting, it sounds like they're trying to solve a human problem with a technological solution. That never works well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Another possible way would be to create script which will do following:
Check every XY seconds/minutes if VPN is established. If not, establish it.
The main question is if such a solution would be possible. Trac.exe info can be used (find string of "Connected"). Maybe cpvn:// command in order to establish VPN in the background.
Just an idea...
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yea...I was thinking maybe modify some local files on client side, but they are more asking if this can be done globally from the fw side, which I am not so sure it can be done...
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Don't believe it's possible to FORCE always on, nor is it a particularly good idea.
In order for things like DHCP or Captive Portal on a public WiFi hotspot to work, you have to allow the device to connect without VPN for a period of time.
My ask back to the client would be: what problem are you trying to solve by forcing always-on VPN?
If it's to prevent access to specific websites (or whatever), there are other solutions to that problem that don't involve an always-on VPN (and add additional protection to boot).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you know ATM mode ? sk133174: Enterprise Endpoint Security Windows Client for ATM
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I heard about it, but reading up from that link, I dont think that would achieve what customer wants.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can use VPN client only, too (sk172325):
E84.60 Standalone Clients
| Platform | Package | Description | Link |
| Windows | E84.60 Remote Access VPN Clients for ATM | Unattended Remote Access VPN clients, managed with CLI and API and do not have a User interface. |
(MSI) |
| E84.60 Remote Access VPN Clients for ATM - Automatic Upgrade file | Unattended Remote Access VPN clients, managed with CLI and API and do not have a User interface for automatic upgrade through the gateway. For SmartDashboard-managed clients only. |
(CAB) |
This documentation is valid for both EPS and RA VPN ATM clients: E80.86 and higher Endpoint Security Client for ATMs Deployment Guide
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I guess something to think about...
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, i have discussed it with local chp gyus and have an answer that you need endpoint protection package with local fw > connected/distonnected status > if you are not connected the FW will not allow any interesting communication so the user will connect to vpn voluntarily..
regards
Petr
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This does not help if you can shutdown the EPS client. ATM would be the way to go...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
Do you have a detailed instruction how to achieve this behavior?
I was looking at Location-based policies, but it is not clear at all how to configure this
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @the_rock ,
If you have machine certificates, enabling the below in the client's trac.default will disable the connect/disconnect button in the GUI and use machine certificate only.
enable_machine_auth true
machine_tunnel_site "SITE_NAME"
machine_tunnel_after_logon true
Admins or service desk still can disconnect from CMD.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Wed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter