- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Machine Certificate Authentication with SAML (Azur...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Machine Certificate Authentication with SAML (Azure) is not working
Hi All,
Trying to figure out why the configuration of the machine certificate authentication is not working....this one seems quite difficult.
SAML is working fine but adding cert auth for machines gives an error "Internal error; connection failed. More details may be available in the logs".
I have placed respectively the Root CA that is in the local machine space as a Trusted CA and the same for the intermediate CA as Subordinate CA. Also have the signed certificate for the machine in the Personal Certificates. Saw some KB in regards to the subject name which was empty before, changed that to use the CN instead, but still no luck at all.
We have a distributed environment with SMS on R81 and a cluster on R80.40 and the Endpoint Security on E87.00
Has anyone faced something similar and were you able to fix this?
Regards.
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the precise process you used to add machine certificate authentication?
Screenshots (with sensitive details redacted) would be exceptionally helpful here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
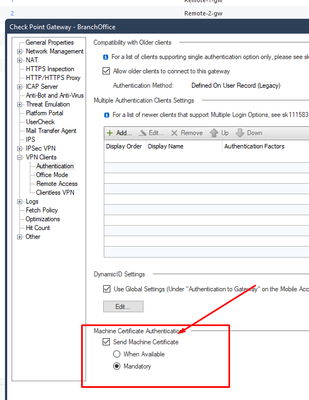
I was using the approach described on the documentation and everything is running fine without machine cert auth:
Thinking as a more secure way trying to narrow down the access roles to the specific OU containing the machines as well.
Checked also this one :
sk170140
Some logs from the trac.log:
[ 5520 6368][8 Jun 0:19:17][RaisCertManager] SetFriendlyNameOnToken: __start__ 0:19:17.241
[ 5520 6368][8 Jun 0:19:17][RaisCertManager] GenerateFriendlyNameWithSerial: __start__ 0:19:17.241
[ 5520 6368][8 Jun 0:19:17][RaisCertManager] RaisCertManager::_GenerateFriendlyNameWithSerial: ERROR!! subject or serial is empty, return empty string
[ 5520 6368][8 Jun 0:19:17][RaisCertManager] GenerateFriendlyNameWithSerial: __end__ 0:19:17.241. Total time - 0 milliseconds
[ 5520 6368][8 Jun 0:19:17][RaisCertManager] SetFriendlyNameOnToken: __end__ 0:19:17.241. Total time - 0 milliseconds
[ 5520 6368][8 Jun 0:19:17][] fwCAPIProvider_imp::GetToken: Machine certificate, index 1.
[ 5520 6368][8 Jun 0:19:17][] fwCAPIToken::fwCAPIToken: enter (1) start (03331588, imp: 01E0A9F8)
[ 5520 6368][8 Jun 0:19:17][] fwCAPIToken_imp::Init2(PCCERT_CONTEXT TheCert): enter... machineCtx is 1
[ 5520 6368][8 Jun 0:19:17][] MyprintCertName:fwCAPIToken_imp::Init2(PCCERT_CONTEXT TheCert) enter...
[ 5520 6368][8 Jun 0:19:17][] MyprintCertName:fwCAPIToken_imp::Init2(PCCERT_CONTEXT TheCert) cert name is: CN=test.contoso.local
[ 5520 6368][8 Jun 1:15:36][Rais_CAPICERT] Rais_CAPICERT::capi_cert_sign: Failed to sign Buffer
[ 5520 6368][8 Jun 1:15:36][] fwPubKey::SetMachineCtx: enter.. about to set to 0
[ 5520 6368][8 Jun 1:15:36][] fwWinPubKey_imp::SetMachineCtx: about to set machine contex to 0.
[ 5520 6368][8 Jun 1:15:36][Rais_CAPICERT] capi_cert_sign: __end__ 1:15:36.930. Total time - 5 milliseconds
[ 5520 6368][8 Jun 1:15:36][Rais_CAPICERT] CAPICert::Sign: __end__ 1:15:36.930. Total time - 5 milliseconds
[ 5520 6368][8 Jun 1:15:36][Rais_CAPICERT] Rais_CAPICERT::CAPICert::Machine_Sign: done.
[ 5520 6368][8 Jun 1:15:36][IKE] create_MM5(hybrid authentication): Failed to sign hash with the machine's certificate (-996)
[ 5520 6368][8 Jun 1:15:36][rais] [DEBUG] [RaisMessages::CreateMessageSet(s)] message: (msg_obj
:format (1.0)
:id (ClipsMessagesInternalError)
:def_msg ("Internal error; connection failed. More details may be available in the logs")
:arguments ()
)
[ 5520 6368][8 Jun 1:15:36][TR_FLOW_STEP] TR_FLOW_STEP::TrConnEngineConnectStep::operation_failed: Cb arrived
[ 5520 6368][8 Jun 1:15:36][FLOW] TrConnEngineConnectStep::operation_failed: user message set: (msg_obj
:format (1.0)
:id (ClipsMessagesInternalError)
:def_msg ("Internal error; connection failed. More details may be available in the logs")
:arguments ()
I am having hard time to understand why it is not working while I have the whole chain of certificates enrolled and on the relevant local machine relevant areas, have used the same PKI certificates in this case, just created a new one on the Personal Certificates on local machines since the subject was missing and we edited an existing template on the CA server in order to create a new request having the possibility to fill in the "Subject" filed there.
Not sure what important task I might have missed to mention here, please let me know if more needs to be described by me.
Thank you and best regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I was able to find on this community some other situation describing somehow what I am facing:
R81 - New VPN users unable to establish VPN via SHA256
After configuring phase 1 with SHA1 I still see issue when machine certification authentication is on "mandatory".
I get an error mentioning the Subordinate CA while I think the actual issue is with the ROOT CA on Trusted CA, because the real certificate is expiring in 2050 - while the one imported on SMS is expiring on 2038. This is really new to me, so I checked the ICA which is expiring as well on the same month on 2038 (maybe that is just a coincidence). Anyhow I thought to ask if someone might know or faced this before.
Thank you in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
According to the product documentation, you can only use Machine Certificates with a Microsoft AD server.
For Azure AD, you would configure the Machine Certification there as one of the authentication methods.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I missed to mention that I have already configured LDAP Account Unit and Identity Awareness gathering information by using identity collectors which connects to the ADs.
SAML is a second profile, if I use the first one which is based on RADIUS (NPS servers, same one used to host the identity collector agents) the connection works but not with machine certification. SAML works too, but not if I select any of the option related to the Machine Certificate Authentication.
Except of having a certificate with a subject value not empty, and of course importing Root CA and Subordinate CA in the SMS in order to check the local machine certificate, is there any other specific parameter / setting which we need to take care for making this work?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe the Machine Certificate setting applies to all profiles and SAML cannot be combined with other authentication methods (including Machine Certificate).
I think this will require a TAC case to more deeply investigate: https://help.checkpoint.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
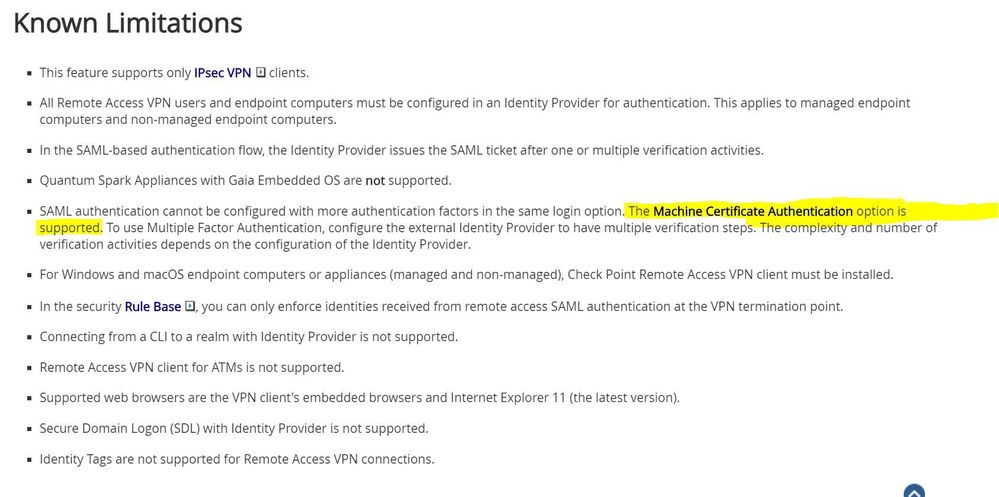
I understand that if Machine Certificate Authentication will be used, will impact all realms configured but based on checkpoint documentation, it seems that is supported:
Unless I understand this in a wrong way 😅
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good to know it's supported.
Still seems like the IdP would be a better place to configure this.
However, since it is supported to use a Machine Certificate to bring up a Machine Tunnel before authenticating with a user via SAML, it makes sense these features would work together.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Just thought to comment here as an update after I was able to solve this. It was a matter of internal communication from the firewall to the specific server where the certificate was pointing to in order to be checked against the CRL (communication towards that server on port 80 - http ). After that I can use the machine certification authentication as a factor with both SAML or Radius Servers (using Azure MFA as a second authentication factor except credentials).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Sky,
Thanks for sharing the very good tips. I am gathering the information, and would like to test out this solution as well. Is there any changes, or attribute needs to modify at Azure side to implement the Machine Authentication? It would be great if you could share the issue/challenging during the implementation.
Regards,
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter