- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- SASE and Remote Access
- :
- MacOS EPS Standalone Client (VPN client) Block All...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
MacOS EPS Standalone Client (VPN client) Block All Incoming Traffic
Hi everyone in Checkmates
As an engineer of CheckPoint's Partner, I am always interested in latest CheckPoint Software release, and I always use Endpoint Connect VPN (or known as Endpoint Security Standalone VPN Client) to keep connecting with Lab environment in company's network. I am a MacOS user (current OS Catalina, version 10.15.4), after upgrading the client to E82.50, I find that although no firewall policy loaded, after OS loads cpfw.kext (kernel extension), my Mac starts to block all incoming traffic. In fact, after installing new VPN client, my Mac can receive incoming traffic but never sends out any kind of reply ( for example, ping my Mac will get Overtime error ).
Although this issue can be fixed by unload this kernel extension manually, at the same time the VPN client will stop working. And it is Standalone EPS vpn client, so maybe it is hard to manage the default policy brought by cpfw.kext .
As this kind of client meets the requirements of customers who wants VPN function only, I think this behavior is not appropriate.
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Mac VPN client is intended—and licensed—as a full Endpoint client.
This Desktop Firewall is a mandatory component of this that cannot be removed.
You can configure this firewall either in SmartEndpoint or in SmartConsole.
This Desktop Firewall is a mandatory component of this that cannot be removed.
You can configure this firewall either in SmartEndpoint or in SmartConsole.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
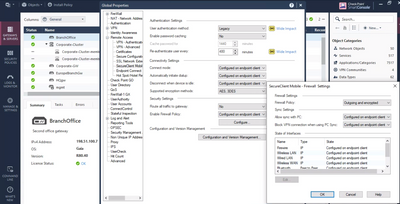
Just to add to this answer, you can configure the state of the Endpoint firewall for all users in Global Properties.
Once the user connects to your gateway, the configuration of this firewall will be updated.
If you want something more granular than what's listed here, you will need to configure a Desktop Firewall policy.
This can be enabled by ticking the "Policy Server" option in your gateway object, then a Desktop Firewall policy can be added to an existing policy package and created as desired.
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Mac VPN client is intended—and licensed—as a full Endpoint client.
This Desktop Firewall is a mandatory component of this that cannot be removed.
You can configure this firewall either in SmartEndpoint or in SmartConsole.
This Desktop Firewall is a mandatory component of this that cannot be removed.
You can configure this firewall either in SmartEndpoint or in SmartConsole.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is not a "solution" - it is a work around that ignores a more general problem. As a consultant, I work with numerous clients. One of my clients needed me to install Checkpoint VPN to work on their network. Unfortunately, after installing the VPN client, my MacBook Pro no longer allows incoming connections... no matter if the VPN is connected. This is problematic for me in needing to work with other clients, and even on my home network. I can understand the VPN client having control over how my computer connects to local networks when connected to the VPN. However, once the VPN client is shut down locally, it should no longer have any control over my local machine's network connectivity. The VPN client is not being used purely by road warriors... and those of us who have machines not owned by the companies that run the VPN servers should not be impacted by the VPN client when we are not connected. Now my only options are to, apparently, ask my client to create a separate security policy in their VPN just for me, or for me to unload a kernel extension when I want to have control of my computer? The UX here is pretty weak.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The other option is to use the SNX client which does not have a desktop firewall component.
You can try to download a version of the client from here and use it against the relevant gateway: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Checkpoint VPN client can be installed from the same installer package in 3 different flavours:
EPS VPN including Desktop Firewall (the version used in the posts above)
Mobile VPN (no Desktop Firewall)
SecuRemote (no Desktop Firewall, no Office mode)
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Only the EPS flavor exists for the Mac.
Check Point Mobile and SecuRemote are not supported on the Mac.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to add to this answer, you can configure the state of the Endpoint firewall for all users in Global Properties.
Once the user connects to your gateway, the configuration of this firewall will be updated.
If you want something more granular than what's listed here, you will need to configure a Desktop Firewall policy.
This can be enabled by ticking the "Policy Server" option in your gateway object, then a Desktop Firewall policy can be added to an existing policy package and created as desired.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We encountered the same problem. The solution in the picture is not working, as it only applies to the mobile client and will not work with the (MacOS) Enpoint Security client
We also tried using the conf/trac_client_1.ttm to change this behavior with no success. While we could set the client to a "firewall off" state and other things, incoming connections were still being dropped.
The only solution that was working was the Desktop Firewall route, which is kind of unsatisfying as we only need it to replicate the behavior of mobile VPN for MacOS clients.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, Any quick way to do it on R81.10?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Believe it's the same procedure in R81.10.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually, I've tried it on 81.10 and it seems to lack the whole "Security Setting" section.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The section is there, but it's missing the Enable Firewall Policy option.
Possible that option is configured somewhere else now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As a workaround for this, I built an Automator action that runs a short shell script to toggle the processes that are blocking the connections. The script was lifted from SuperUser.com, but at least building it into an Automator workflow was my idea. The content of the script (which needs to be directed to stdin) in Automator is:
Click to Expand
#!/bin/bash
#
# The reason of creating this script is that Endpoint Security VPN installs it's own application firewall kext cpfw.kext
# which prevents for example PPTP connections from this computer, which is not appropriate if you need subj connection just
# from time to time
#
# Usage: ./checkpoint.sh
#
# The script checks if Enpoint Security VPN is running. If it is, then it shuts it down, if it is not, it fires it up.
# Or, make an Automator action and paste the script.
# You will need sudo power, of course
#
# To prevent Endpoint Security VPN from starting automatically whenever you restart your Mac, edit this file:
# `/Library/LaunchAgents/com.checkpoint.eps.gui.plist`
# And change the values of `RunAtLoad` and `KeepAlive` to `false`
# [Source](https://superuser.com/questions/885273)
# SERVICE='Endpoint_Security_VPN'
SERVICE='Endpoint_Security_VPN'
if pgrep $SERVICE > /dev/null
then
# $SERVICE is running. Shut it down
sudo launchctl unload /Library/LaunchDaemons/com.checkpoint.epc.service.plist
sudo kextunload /Library/Extensions/cpfw.kext
killall $SERVICE
else
# $SERVICE is not running. Fire it up
sudo launchctl load /Library/LaunchDaemons/com.checkpoint.epc.service.plist
sudo kextload /Library/Extensions/cpfw.kext
open '/Applications/Endpoint Security VPN.app'
fi
Also, to get this to work, you will need to (one time only) manually edit /Library/LaunchAgents/com.checkpoint.eps.gui.plist and /Library/LaunchAgents/com.checkpoint.eps.gui.plist to set the key RunAtLoad to off.
The above will also disable Endpoint Security from bringing up a login dialog after every startup even if that is controlled by a policy. So, from an ethical standpoint, this only be used on a personally-owned computer, I think. However, it will, once again, allow me to smb and vnc in from other computers on my home network.
Ric
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 4 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter