- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Watch NowCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: How to setup machine certificate authenticatio...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to setup machine certificate authentication?
Hello community!
I want to undestand how correctly enable machine certificate for separete VPN access for AD domain machines and AD users.
If I right about this, that for enable this feature I should:
- Get root cert and intermediate cert in my CA, added this certs to checkpoint environment (according sk149253) for ability generate CSR request for each future machine cert (and this I have a question, after I get cert, generated from CSR, where it is should putted in user machine? For example in windows machine, in certmgr -> "trusted root cert authorities" or other place?);
- In VPN Gateway activate feature "VPN Clients" -> "Authentication" -> select checkbox "Send Machine Certificate";
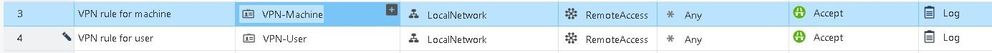
- Finally create rule with AccessRole (of couse, before it, activate Identity awareness for required AD server) in RuleBase as follow:
Please clarify or correct my suggestions about machine certificate option for VPN.
21 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sk121173: Machine Certificate Installation on Security Gateway for Authentication to VPN Clients
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
In my case I would like to be able to find some more detailed documentation or a course where I explain how to configure MAchine Certificat. If you found any documentation that explains better how to activate it, I would appreciate it if you shared it
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for sharing that link, but I can't find all the necessary information is there. For example, nowhere does it explain where and how the certificate is configured on the client side. It also doesn't explain how the client couldn't take the certificate and install it on another computer. This documentation does not help me much, if you have any other information to share I would appreciate it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am not quite sure what you are talking about - the 3rd paragraph reads:
Machine certificate authentication works with the Endpoint Client only. For more details on how to configure this feature on the client side, see Machine Authentication in the E80.72 and Higher Remote Access Clients Administration Guide.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
First of all thank you for your quick response. In the documentation that invites me to follow, there is the configuration of the Endpoint Client and the parameters to set to use a certificate. But I can't find anywhere where it explains:
1- Where to install the certificate on the user's computer.
2-Which certificate to install on the user side
I only find the process of creating and installing the certificate on the gateway, but no documentation explains how to work with this certificate on the client's computer. I hope I have been a little clearer in my doubts
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Generally speaking, machine authentication certificates are done through Microsoft AD or similar. Group policy can be configured related to auto-enrollment from the Microsoft CA, and enforced through their mechanisms. The machine certificates are stored in the certlm console page (On most Windows computers, just begin typing certificate in and you should see Manage Computer Certificates) which is part of the CAPI store.
If you are manually installing a 3rd party certificate for machine cert, then you will need to make sure you have a way to let your DC know about the machine certificates, as access is generally defined by OU for machine-auth.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi JC_S
The manual points to sk149253 as the first step which has instructions to add 3rd party ipsec certificate. I have had many customers querying this. I have been advising them that only steps 1-14 are relevant and to use only the internal CA tied to their Domain.
Are you saying that I was incorrect and that it is possible to use a third party PKI for this afterall?
If so is there any instruction on how to make AD aware of the 3rd party so that client presented certs will allow authentication against the domain?
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I would like to know if you found the answer to your questions. I also need to know where the certificate is installed on the client side.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all, I'm still straggling myself....in case anyone can provide more detailed info, any help will be much appreciated 🙂
Cheers!
Helen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
The cert should be placed in the cert-store for local-machine for use with machine-only tunnels.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
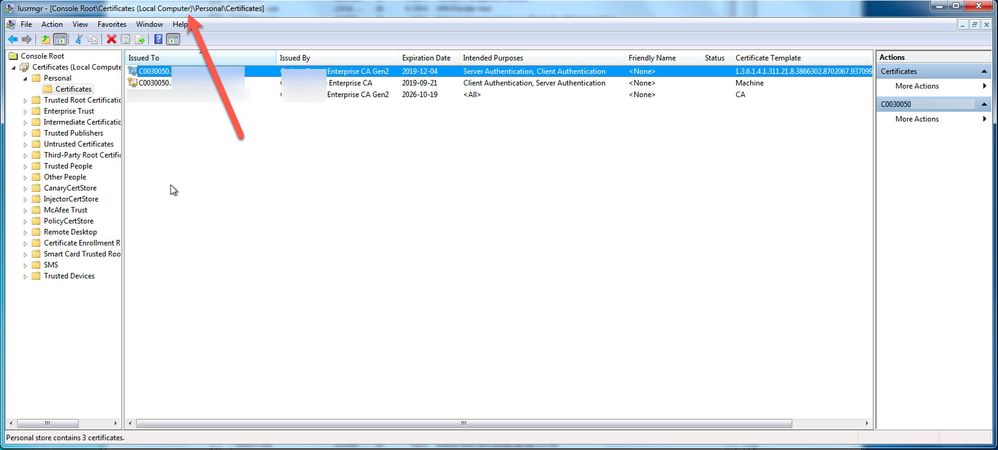
For us we have the client certificate in Personal, the CA is in Trusted Root, and the Sub-CA is in "Intermediate Certification". These last two correspond to the Root, and Sub-CA server objects created in SmartConsole respectively. Certs are deployed via Group Policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In our case we need to carry out a laboratory to later implement it in a client.
We have some doubts because the procedure does not explain in detail. In the case of having a third-party certificate, we are clear about where to add it to the SMS and where to add it to the user's PC, but we have doubts about where to add it in ADDS. And how is the communication generated in the authentication.
Does the PC validate against the SMS certificate and if they are congruent, does it accept the start of the communication, or does the PC validate against the SMS and the SMS against the AD and then return to the PC?
Thank you so much
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The certificate is validated as part of the authentication process per the configured third party certificate authority you're using (per it's CRL/OSCP).
Assuming the certificate is valid and matches a known branch, the user is authenticated on the Check Point gateway.
Groups are looked up via LDAP via Active Directory for users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much for the reply.
Therefore, it is not necessary that the certificate shared by the PC and the Checkpoint Gateway/Cluster is also included in the ADDS. The client wants to log in via VPN with a certificate without entering a password.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It needs to be a certificate that can be validated by the configure third-party certificate authority.
If you want to log in without a password using a certificate, the certificate will need to be stored in the OS-specific certificate store.
Otherwise, if you're using just a .p12 file, the file will need to be protected with a password (but this can be cached by the client).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you so much
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We set it up with the AD integrated CA and enrollment based on AD group membership, that works great.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Steffen,
Do you have any idea if we integrate with SAML using identity_provider. I just wonder how the machine_authentication working flow in this scenario.
Regards,
Sambath
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sambath - unfortunately not
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesTue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesTue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter