- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: How to restrict the MS Active Directory Authen...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
How to restrict the MS Active Directory Authentication for remote access VPN to specific AD Groups
Hello everyone,
we are using AD users for remote access VPN. We have defined some Access Roles for serveral AD Groups, but, we have observed every AD user can log in via VPN client (end point sercurity), regardless the user has a security policy associated or not. If the user is not included in a security policy, of course, they are not able to access to some where, but, they still can do the log in successfully on the VPN client.
So, somehow, we would like to allow the AD authentication for remote access VPN just for those users belonging to the Access Roles or for some specific AD Groups.
How could we do this configuration?
Thanks for your help.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
you're right, thanks for clarification 😀
With this configuration anyone can login via VPN client, regardless the configured access rules.
With this configuration the login via vpn client is failing if the user is not member of the shown group. This is to restrict the generally access to the remote access vpn.
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Fzahinos,
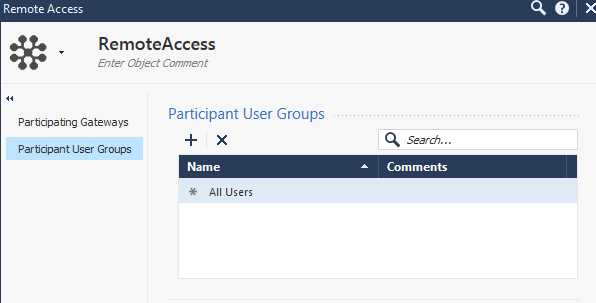
on the RemoteAccess community you can restrict the access to VPN via local or LDAP user group. Remove the normally shown „all users“ and add your own ldap group. Every user not being member of this group will be not allowed to connect.
Wolfgang
on the RemoteAccess community you can restrict the access to VPN via local or LDAP user group. Remove the normally shown „all users“ and add your own ldap group. Every user not being member of this group will be not allowed to connect.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Wolfgang.
I have a doubt about this solution. In case an user is included in two LDAP or Users Local Groups, shoud I define the two LDAP Groups as Participant User Groups?
BR,
Fzahinos.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Fzahinos,
if the user is in more then one Group, one Group is enough to allow the remote Access.
We are using normal rules with access_roles as source for allowing the specific access to Destination and services inside the Network.
With the group on the remote access community we're allowing the generally access to VPN. For this we created a new group in ActiveDirectory and reference them there. Now we can regulate which users can generally connect via remote access, regardless the access_roles.
Wolfgang
if the user is in more then one Group, one Group is enough to allow the remote Access.
We are using normal rules with access_roles as source for allowing the specific access to Destination and services inside the Network.
With the group on the remote access community we're allowing the generally access to VPN. For this we created a new group in ActiveDirectory and reference them there. Now we can regulate which users can generally connect via remote access, regardless the access_roles.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
but in case you use access role on rules than you need to create ldap group to filter on the remote access community, bit annoying
Fabio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes you are right, it's little bit confusing.
But you can add only local or ldap groups to the remote access community, it would be better with a normal access role but that's how it works. Maybe one day Check Point will allow access roles with all configurations, but at the moment some things can be done only with ldap-groups
We added there only one ldap-group named "remote_access_allow_general". This is configured in two minutes and then you can forget about ldap-groups 😉
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
what do you mean exaclty with "remote_access_allow_general"? anyway if you have different access role group you will need the matching one the remote access community, if not any user anyway will log in (even after without have access to resources)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
He means the LDAP group is specified only on first implementation and every VPN user is added to this group through AD.
Later on this group doesn't need to be changed configuration-wise in Check Point and only access roles need to be configured/modified to allow specific access on rules.
Later on this group doesn't need to be changed configuration-wise in Check Point and only access roles need to be configured/modified to allow specific access on rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
you're right, thanks for clarification 😀
With this configuration anyone can login via VPN client, regardless the configured access rules.
With this configuration the login via vpn client is failing if the user is not member of the shown group. This is to restrict the generally access to the remote access vpn.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok got it what you mean!
Thank you
Fabio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Does this works with nested groups?
Thanks
Does this works with nested groups?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure, you have to try.
Following Mobile Access and Endpoint clients LDAP nested groups are not enforced correctly
it's not supported. But I think this article is meaning the access rules itself and not the group for the remote access community.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I'm unable to either add custom ldap group or delete the default All Users group user Participant Users Group. Am i missing something?
Thanks
Raj
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
me too
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You also need to create a new LDAP Group in the objects. Not a User Access Group.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
just updating the thread that the issue raised by @PointOfChecking , solved.
In order for VPN to work as an identity source you must enable "Remote Access" checkbox under Identity Awareness properties.
it is also documented in Identity Awareness Admin Guide.
Thanks,
Ilya
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter