Can any one here guide me on how to get a better score when I scan my firewall with the SSL Server Test (Powered by Qualys SSL Labs) ?
Is there a quick guide on how to enable forward secrecy, disable tls v1.0, 1.1 and weak ciphers etc. ?

 Best regards Keld Norman
Best regards Keld Norman
Thanks for the anwsers so far - I have collected them all - testet and gotten better scores - here is what i did:
#######################################################################
# HOW TO GET BETTER GRADES IN THE SSLLABS.COM SSL TEST #
#######################################################################
To get from the B to A I did the following:
Alter the portal to only support TLS 1.2
In my 80.10 SmartConsole:
Global Properties -> AdvancedConfiguration -> Portal Properties: Altered minimum version to TLS 1.2
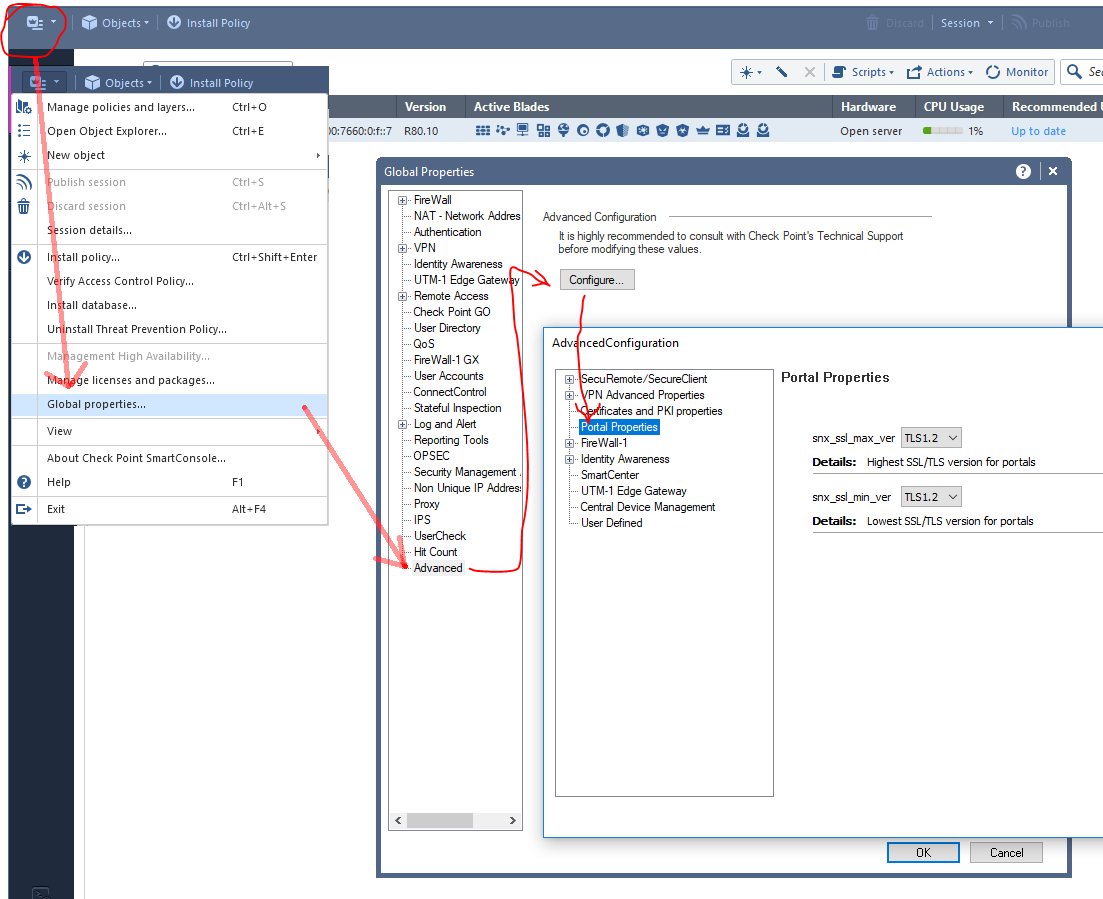
NB: Thanks to Claus Kjær for reminding me of this GUI way of doing things - I were trying to do achieve this by altering conf files with vim in expert shell..
Now to enable perfect forward support:
REF: Specific HTTPS sites that use ECDHE ciphers are not accessible when HTTPS Inspection is enabled (sk110883)
| A note about the above sk110883 |
|---|
ECDHE is quite widely used and recommend. It works with elliptical keys and provides forward secrecy. It's used for the key exchange. ECDSA is not widely used though, but it does also use elliptical keys. It it used for authentication |
I logged on to the firewall via secure shell (I have a standalone installation with the manager and firewall running in a VM) and in expert mode pasted the following 3 lines in:
[Expert@firewall:0]#
ckp_regedit -a SOFTWARE//CheckPoint//FW1 CPTLS_ACCEPT_ECDHE 1
ckp_regedit -a SOFTWARE//CheckPoint//FW1 CPTLS_PROPOSE_ECDHE 1
ckp_regedit -a SOFTWARE//CheckPoint//FW1 CPTLS_EC_P384 1
Then a reboot or just a cpstop/start is needed:
[Expert@firewall:0]# nohup $(cpstop ; cpstart) &
Now the grade went from B to A :
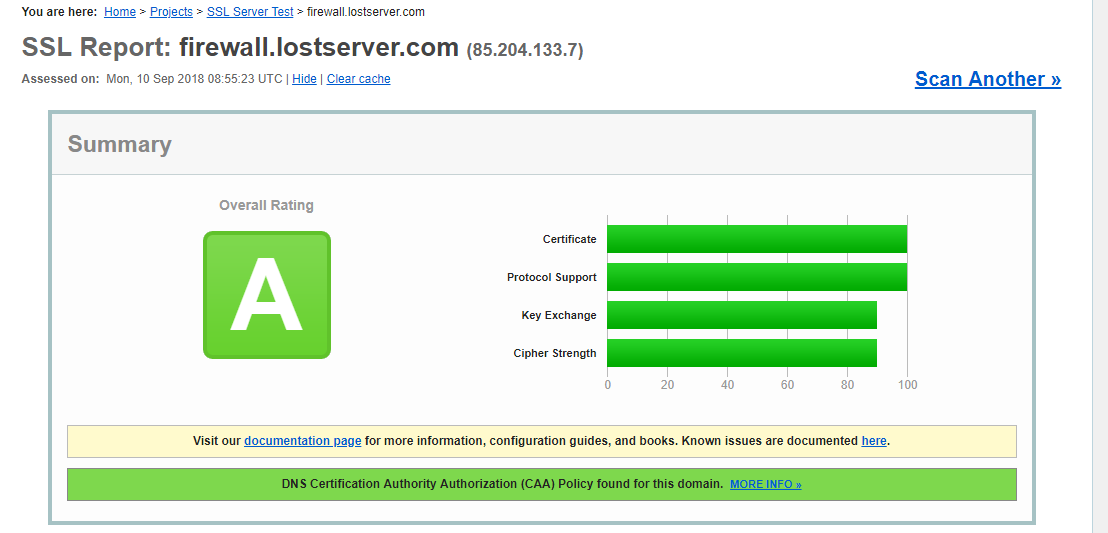
Now to look at the suggested link from Dameon Welch Abernathy ![Employee Employee]()

Remove the weak ciphers related to TLS 1.2
(ref: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...)
So basically I just need to alter this in the file: /web/templates/httpd-ssl.conf.templ
ALTER: SSLCipherSuite HIGH:!RC4:!LOW:!EXP:!aNULL:!SSLv2:!MD5
TO SSLCipherSuite ECDH:!aNULL:!ECDSA:!aECDH:!eNULL:!MD5:!SHA1
Again secure shell to the system - and in export mode paste the lines in purple below:
# Backup the file you want to alter first
[Expert@firewall:0]#
cp /web/templates/httpd-ssl.conf.templ /web/templates/httpd-ssl.conf.templ.backup
# Oneliner to replace the old line with the new using the SED util.
sed -i 's/SSLCipherSuite HIGH:!RC4:!LOW:!EXP:!aNULL:!SSLv2:!MD5/SSLCipherSuite ECDH:!aNULL:!ECDSA:!aECDH:!eNULL:!MD5:!SHA1/' /web/templates/httpd-ssl.conf.templ
# Test if the line was altered:
grep -i ^SSLCipherSuite /web/templates/httpd-ssl.conf.templ
( it should return: SSLCipherSuite ECDH:!aNULL:!ECDSA:!aECDH:!eNULL:!MD5:!SHA1)
Then reboot the firewall..
[Expert@firewall:0]# reboot
The Qualys SSL scan still only shows an A - I still have some weak ciphers 😕
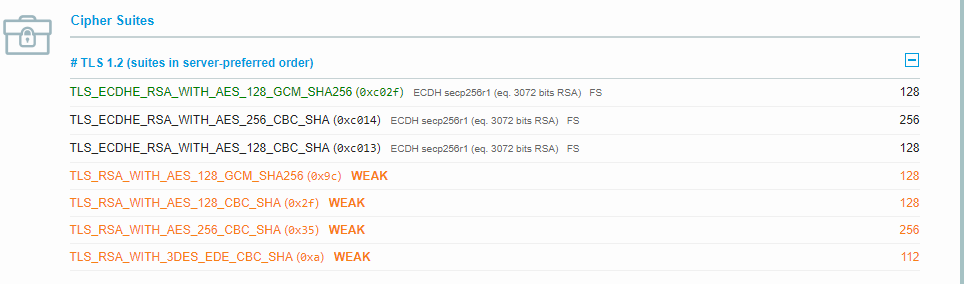
To be continued..



