- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Delivering reserved IP in the ipassignment file to...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Delivering reserved IP in the ipassignment file to other users
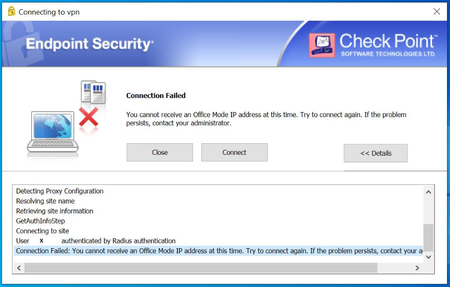
Hello everyone,
I'm having problems with the ipassignment file.
I created the IP reservation for some users, but other users are receiving the reserved IP, and when users with reserved IPs will connect, it gives an error message saying that it was not possible to obtain an IP address.
Does anyone have any ideas how to solve this problem or where to see ipassignment logs?
Thank you in advance.
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The configuration was correct according to sk33422.
I had reserved random IPs, and according to my support team I was instructed to reserve IPs at the beginning or end of the range, and replace the gategay address with *.
My setup looks like this and apparently it's working right now.
################################
### Gateway Type IP Address User Name ###
################################
* addr 172.16.0.254 user1
* addr 172.16.0.253 user2
* addr 172.16.0.252 user3
* addr 172.16.0.251 user4
* addr 172.16.0.250 user5
* addr 172.16.0.249 user6
Thank you all
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We continue to have the same problem.
According to sk116603 reserved ips cannot be in the range delivered in office mode.
We created a new range for reserved ips and now we have no more problems.
Thank you all
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Print a sample of your ipassignment.conf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
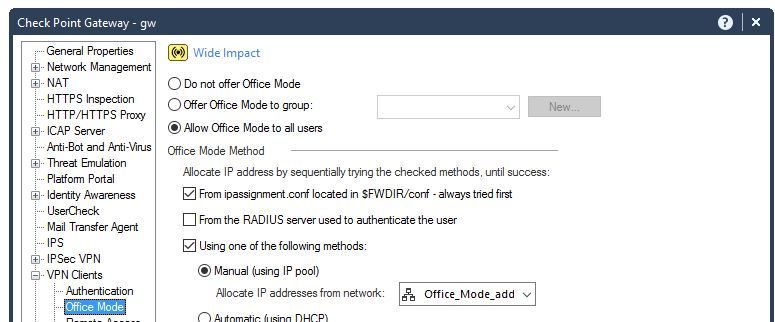
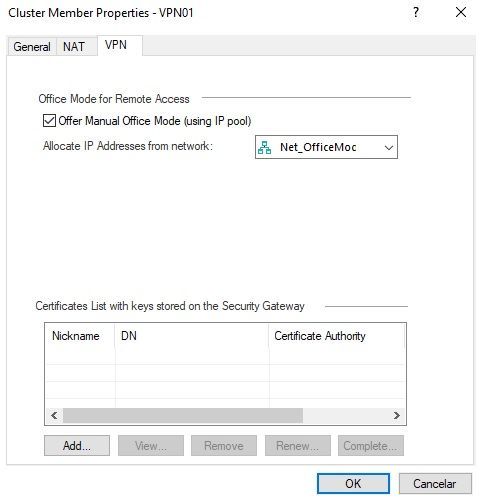
If you have carefully follower configuration examples in Remote Access VPN Administration Guide R80.20 p.58ff, logs will be helpfull:
In clients VPN Options > Advanced Tab, enable Logs. Replicate the issue on the client successfully noting the exact time and click on Collect Logs. Wait a while and the compressed logs will be shown. Disable logging and review the logs in trac.log e.g. using search for GW IP. Full debugs are found here: sk95486: How to debug Endpoint Client connection issues
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you assign a given user an IP address make sure it is impossible for any other user to be assigned this address.
This means making sure that IP is NOT in the general pool of users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The configuration was correct according to sk33422.
I had reserved random IPs, and according to my support team I was instructed to reserve IPs at the beginning or end of the range, and replace the gategay address with *.
My setup looks like this and apparently it's working right now.
################################
### Gateway Type IP Address User Name ###
################################
* addr 172.16.0.254 user1
* addr 172.16.0.253 user2
* addr 172.16.0.252 user3
* addr 172.16.0.251 user4
* addr 172.16.0.250 user5
* addr 172.16.0.249 user6
Thank you all
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is your config?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are doing radius authentication. Have you check the office mode with a local user on the firewall before switching to radius? If not, does it work with a local user?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I haven't tested it with a local user, only via radius.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We continue to have the same problem.
According to sk116603 reserved ips cannot be in the range delivered in office mode.
We created a new range for reserved ips and now we have no more problems.
Thank you all
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
we tried and its worked..thnks for ur post
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Had same issue, but creating a new pool for a handful of users with reserved IP was not an option for us, What I ended up doing is using the group and range command to ensure users whose ip we dont care about are picked from the range(ex. 192.168.0.1-192.168.0.200) and the reserved IP's are set per user starting from back 254..253... and so on.
# Miami range 100.107.105.110-100.107.105.119/24 Finance
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter