*************************************************
The easiest way to configure L2TP over IPSEC in Linux is to use the Network Manager with the L2TP gnome Plugin as described here. Use at least Network Manager L2TP Plugin Version 1.7.2, otherwise you can't configure IKE Lifetime (8h) and SA Lifetime (1h) which is very important for a stable connection.
*************************************************
This guide show every step how L2TP over IPSEC works in Linux. There are three binaries involved: libreswan, xl2tpd and ppp. At the end you should be able to connect to your Check Point Firewall using the L2TP Pre-shared Key and Username + Password.
Check Point
Before you begin, please make sure you have a working Remote Access environment with Office Mode using one of the Check Point Endpoint Clients (Windows / MacOS). For Authentication use username and password.
In R80.x, when the L2TP Client is behind a NAT device, the connection won't work, see sk145895. Without this hotfix the L2TP connection won't be establish.
My Setup:
R80.30 Standalone with Jumbo Take 76 and Hotfix: fw1_wrapper_HOTFIX_R80_30_T71_JHF_470_MAIN_GA_FULL.tgz
Requirements Check Point:
1)
- Global Properties - Remote Access - VPN - Authentication - Support Authentication - Support Legacy Authentication for SC
- Global Properties - Remote Access - VPN - Authentication - Support Authentication - Support L2TP with Pre-Shared Key
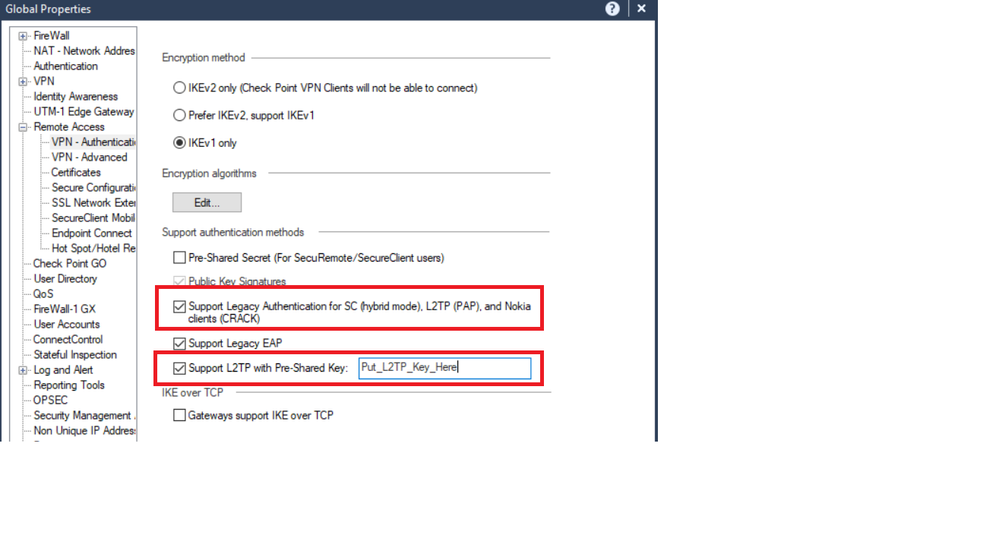
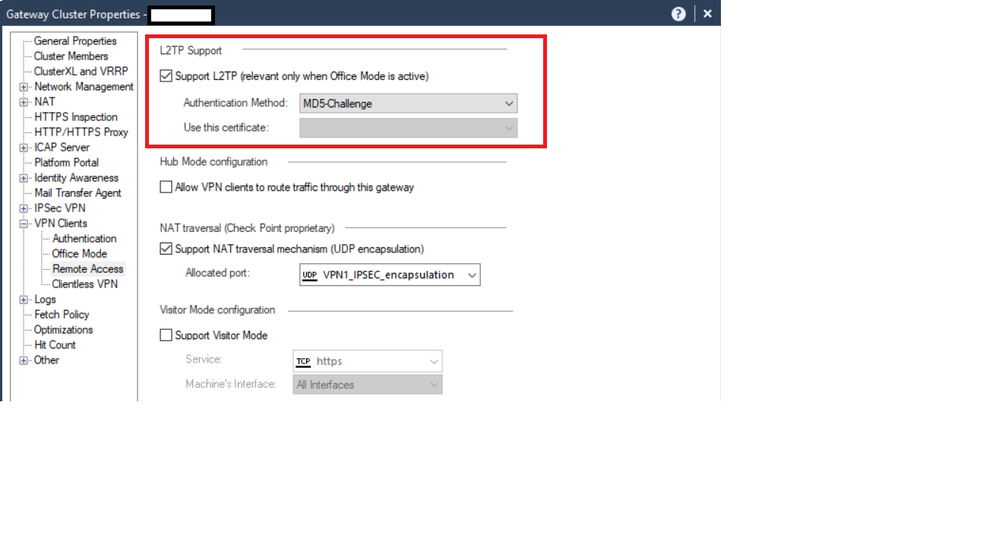
2)
- Gateway Object - Properties - VPN Clients - Remote Access - Support L2TP
Linux
This guide is based on Linux Mint 19.2 which uses Libreswan 3.23 and xl2tpd 1.3.10.
The L2TP over IPSEC connections depends on libreswan, xl2tpd, ppp and changing the routes manually.
1) libreswan
Is used to establish the IPSEC connection, the transport layer. Install the latest binary by running:
# sudo apt install libreswan
2) xl2tpd
Is used to handle the L2TP authentication with PPP. Install the latest binary by running:
# sudo apt install xl2tpd
3) ppp
Is used for User authentication (Username + Password). Install the latest binary by running:
# sudo apt install ppp # usually pre-installed
4) Routes
After the L2TP over IPSEC connection was established, routing have to be changed manually.
Libreswan Configuration
Libreswan uses files located in /etc/ipsec.d and the main configuration file /etc/ipsec.conf.
1)
Edit the main configuration file /etc/ipsec.conf and add only the logging option. Leave the rest like it is.
config setup
# Normally, pluto logs via syslog. If you want to log to a file,
# specify below or to disable logging, eg for embedded systems, use
# the file name /dev/null
# Note: SElinux policies might prevent pluto writing to a log file at
# an unusual location.
logfile=/var/log/pluto.log
2) Create a new file called "ra.conf" and "ra.secrets" in /etc/ipsec.d/
#sudo touch /etc/ipsec.d/ra.conf
#sudo touch /etc/ipsec.d/ra.secrets
3) edit the /etc/ipsec.d/ra.conf file
# sudo vi /etc/ipsec.d/ra.conf
conn Company-IPSEC
auto=add
type=transport # IPSEC transport layer
authby=secret
keyingtries=0
left=%defaultroute # Client IP Address or use the Defaultroute Interface
right=46.89.4.xxx # put here your Gateway IP Address
rightid=192.168.0.1 # Check Point responds with the Main IP Address from the FW Object
rightprotoport=udp/l2tp # Use L2TP
pfs=no # no PFS is IKE Phase 2
ike=aes256-sha1;modp1024 # IKE Phase 1; AES256, SHA1, DH Group2
phase2alg=aes128-sha1 # IKE Phase 2; AES128, SHA1
salifetime=1h # A Lifetime 1h for IKE Phase P2
ikelifetime=8h # IKE Lifetime 8h for IKE Phase P1
ikev2=no # do not use IKEv2
In this example the libreswan connection name is: Company-IPSEC
4) edit the /etc/ipsec.d/ra.secrets file
Put in the Pre-Shared Secret from SmartConsole.
Global Properties - Remote Access - VPN - Authentication - Support Authentication - Support L2TP with Pre-Shared Key
# sudo vi /etc/ipsec.d/ra.secrets
: PSK "L2TP-Pre-Shared Key"
XL2TPD Configuration
The xl2tpd configuration file is located in /etc/xl2tpd.
1) edit the main configuration file /etc/xl2tpd/xl2tpd.conf
# sudo vi /etc/xl2tpd/xl2tpd.conf
[global]
access control = yes
port = 1701
;
[lac Company-L2TP]
lns = 46.89.4.xxx ; put here your Gateway IP Address
pppoptfile = /etc/ppp/options.l2tpd.client ; File for User Authentication
autodial = yes
tunnel rws = 8
tx bps = 100000000
rx bps = 100000000
In this example the L2TP connection name is: "Company-L2TP".
PPP Configuration
The configuration files are stored under /etc/ppp/
1) create the file /etc/ppp/options.l2tpd.client
# sudo vi /etc/ppp/options.l2tpd.client
nodetach
#show-password # enable for debugging
#debug # enable for debugging
usepeerdns
noipdefault
nodefaultroute
noauth
noccp
refuse-eap # no EAP
refuse-chap # no CHAP
refuse-mschap # no MSCHAP
refuse-mschap-v2 # no MSCHAPv2
lcp-echo-failure 0
lcp-echo-interval 0
mru 1400
mtu 1400
user macbook # Username - Check Point User
password PUTUSERPASSWORD # Password - Check Point User
Check Point supports only PAP for PPP Authentication. I checked the iPhone L2TP debugs in vpnd.elg and also the Windows L2TP over IPSEC guide uses only PAP.
Initiate the Connection
It is very important to start the L2TP over IPSEC connection with all the mentioned commands above. First we need to start libreswan and the xl2tpd. The we bring up the VPN connection.
# systemctl start libreswan
# systemctl start xl2tpd
# sudo ipsec auto --up Company-IPSEC
# sudo echo "c Company-L2TP" |sudo tee /var/run/xl2tpd/l2tp-control
If everything works well, it should look like this:
Libreswan:
002 "Company-IPSEC" #1: initiating Main Mode
104 "Company-IPSEC" #1: STATE_MAIN_I1: initiate
106 "Company-IPSEC" #1: STATE_MAIN_I2: sent MI2, expecting MR2
108 "Company-IPSEC" #1: STATE_MAIN_I3: sent MI3, expecting MR3
002 "Company-IPSEC" #1: Peer ID is ID_IPV4_ADDR: '192.168.0.1'
004 "Company-IPSEC" #1: STATE_MAIN_I4: ISAKMP SA established {auth=PRESHARED_KEY cipher=aes_256 integ=sha group=MODP1024}
002 "Company-IPSEC" #2: initiating Quick Mode PSK+ENCRYPT+UP+IKEV1_ALLOW+SAREF_TRACK+IKE_FRAG_ALLOW+ESN_NO {using isakmp#1 msgid:4e756e62 proposal=AES_CBC_128-HMAC_SHA1_96 pfsgroup=no-pfs}
117 "Company-IPSEC" #2: STATE_QUICK_I1: initiate
003 "Company-IPSEC" #2: our client peer returned protocol id does not match my proposal - us0 vs them: 17
003 "Company-IPSEC" #2: Allowing questionable proposal anyway [ALLOW_MICROSOFT_BAD_PROPOSAL]
004 "Company-IPSEC" #2: STATE_QUICK_I2: sent QI2, IPsec SA established transport mode {ESP/NAT=>0xb8685cf2 <0x3dcf0898 xfrm=AES_CBC_128-HMAC_SHA1_96 NATOA=none NATD=46.89.4.xxx:4500 DPD=passive}
xl2tpd:
soren@mint-laptop:~/Desktop$ systemctl restart xl2tpd
soren@mint-laptop:~/Desktop$ sudo echo "c Comapny-L2TP" |sudo tee /var/run/xl2tpd/l2tp-control
c Comapny-L2TP
Interface ppp0 was created:
ppp0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1400
inet 192.168.1.38 netmask 255.255.255.255 destination 192.168.0.1
ppp txqueuelen 3 (Point-to-Point Protocol)
RX packets 4 bytes 52 (52.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 64 (64.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Disconnect the Connection
The followings commands are used to terminate the L2TP VPN connection.
# sudo echo "d Company-L2TP" |sudo tee /var/run/xl2tpd/l2tp-control
# sudo ipsec auto --down Company-IPSEC
# systemctl stop libreswan
# systemctl stop xl2tpd
*for troubleshooting use "restart" instead of "stop".
Routing
After the VPN connection is established, the traffic won't be routed through the VPN Tunnel.
1) Example Route table using an iPhone Hotspot
soren@mint-laptop:~/Desktop$ netstat -rn
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
0.0.0.0 172.20.10.1 0.0.0.0 UG 0 0 0 ens33
169.254.0.0 0.0.0.0 255.255.0.0 U 0 0 0 ens33
172.20.10.0 0.0.0.0 255.255.255.240 U 0 0 0 ens33
192.168.0.1 0.0.0.0 255.255.255.255 UH 0 0 0 ppp0
2) Route Only the Encryption Domain
First try to route only your Encryption Domain through the VPN Tunnel, for example 192.168.0.0/24. The next hop is the IP Address of the ppp0 Interface, in this example 192.168.1.38
# sudo ip route add 192.168.0.0/24 via 192.168.1.38 dev ppp0
Routing Table:
soren@mint-laptop:~/Desktop$ netstat -rn
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
0.0.0.0 172.20.10.1 0.0.0.0 UG 0 0 0 ens33
169.254.0.0 0.0.0.0 255.255.0.0 U 0 0 0 ens33
172.20.10.0 0.0.0.0 255.255.255.240 U 0 0 0 ens33
192.168.0.0 192.168.1.38 255.255.255.0 UG 0 0 0 ppp0
192.168.0.1 0.0.0.0 255.255.255.255 UH 0 0 0 ppp0
Try to reach any host in the Encryption Domain
Troubleshooting
For troubleshooting and configuration changes always restart both services!
# systemctl restart ipsec
# systemctl restart xl2tpd
Logfiles are in /var/log/pluto.log (libreswan) and /var/log/syslog (xl2tpd)
Scripts
It is very useful to use a script to do all the mentioned steps above. The mentioned script is from the Arch Wiki. This script starts libreswan, xl2tpd and changes the routing to route all traffic through the tunnel.
#!/bin/bash
if [ $# != 1 ] ; then
echo "Usage: (sudo) sh $0 {start|stop}"
exit 1;
fi
VPN_ADDR=46.89.4.xxx # put here your Firewall IP
IFACE=ens33 # LAN /Wifi Interface
function getIP(){
ip addr show $1 | grep "inet " | awk '{print $2}' | sed 's:/.*::'
}
function getGateWay(){
route -n | grep -m 1 "^0\.0\.0\.0" | awk '{print $2}'
}
function getVPNGateWay(){
route -n | grep -m 1 "$VPN_ADDR" | awk '{print $2}'
}
GW_ADDR=$(getGateWay)
function start(){
systemctl restart ipsec
sleep 1 #delay to ensure that IPsec is started before overlaying L2TP
systemctl restart xl2tpd
ipsec auto --up Company-IPSEC
sleep 1
echo "c Company-L2TP" | sudo tee /var/run/xl2tpd/l2tp-control
sleep 4 #delay again to make that the PPP connection is up.
route add $VPN_ADDR gw $GW_ADDR $IFACE
route add default gw $(getIP ppp0)
route delete default gw $GW_ADDR
}
function stop(){
ipsec auto --down Company-IPSEC
echo "d Company-L2TP" | sudo tee /var/run/xl2tpd/l2tp-control
VPN_GW=$(getVPNGateWay)
route delete $VPN_ADDR gw $VPN_GW $IFACE
route add default gw $VPN_GW
}
$1
exit 0
Save the script under the name vpn.sh and use it like this:
# sudo ./vpn.sh start
# sudo ./vpn.sh stop
If any error comes up running the script, run "# sudo ./vpn stop" to change the routing back to normal.




