Hi community,
last week I accidently stopped a critical R80.40 mdm environment.
Why accidently? I wanted the see if there are possible options or switches I can use with the command "mdsstop".
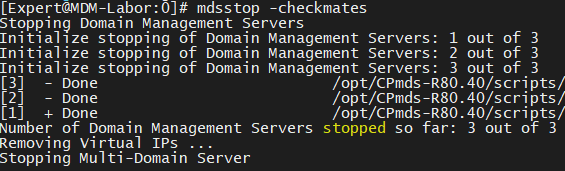
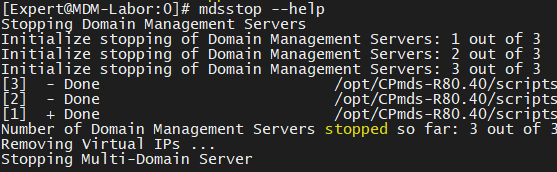
So I tryed: "mdsstop --help"
This is what I normally do when looking for help context under linux.
The problem:
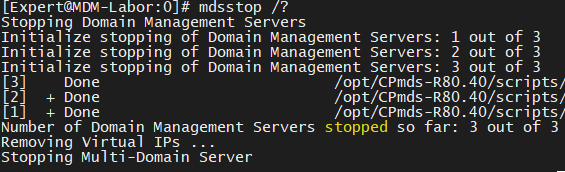
mdsstop does not have the options "--help" and "/?", but it does not respond like it does for example cpinfo: "invalid option".
It just executed the command without any flags which means "mdsstop" so my mdm went down...
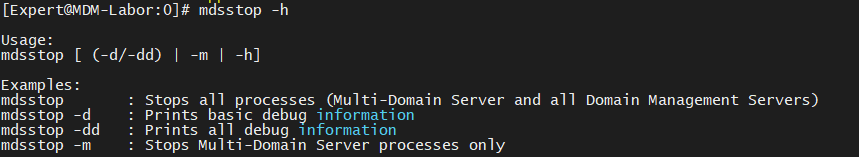
BTW: The correct option to see the help is "-h". It's the same with mdsstat and mdsstart.
I opened a service request to find out if this is expected behavior.
Check Point answered that this is not a linux command, so I can not expect same options.
If I want to know possible options I should have a look in the admin guide and if needed anyways I should open an RFE.
I would say ignoring invalid options is not a good implementation of options.
Minimum should be a feedback of "invalid option" without executing the command.
Optimum would be "invalid option" without executing the command and showing possible options.
For A+ "--help", "-h" and "/?" should show help context, invalid options should respond with "invalid option" followed by a list of possible options.
So how do you guys think about the options of mdsstop/mdsstart/mdsstat?
Is it worth opening an RFE?
Thanks for your opinion.
Cheers
Sven