- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
Operational Health Monitoring
Help us with the Short-Term Roadmap
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Management
- :
- Re: Where did all my IPS Protections go?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Where did all my IPS Protections go?
IPS in SmartDashboard R7x had its protections organized:
- By type:
- Signatures
- Protocol anomalies
- Application controls
- Engine settings
- By protocol
- Network security
- Application intelligence
- Web intelligence
In SmartConsole R80 and R80.10, I cannot find some of these protections. Did they get deleted?
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
None of the protections got deleted unless the IPS engine has updated some of them as obsolete over time.
One of the concepts for R80 security management and security gateway is the separation between Access Control and Threat Prevention. We realized that those are different needs, and therefore, they are split in the user interface, as well as during policy installation - see What is the roadmap for Threat Prevention Policy management? .
R7x term | R8x term | Icon | R80.10 gateways: Install policy of type | Explanation |
|---|---|---|---|---|
Categorization by protocols | IPS Tags |
| Threat Prevention | The categorization of protections in R80 has changed. Instead of the R77 structure, every IPS protection has tags. Tags can be either for the protocol, the operating system, the application, and more. This gives a more dynamic organization structure. Also, the user can automatically disable or enable the enforcement of protections per tags - see How does R80 assist in saving time handling activation of IPS protections? |
IPS by type: signatures / protocol anomalies | Type: Threat Cloud | | Threat Prevention | Over 7000 different protections which compose the vast majority of IPS Protections. |
IPS by type: signatures / protocol anomalies | Type: Core | | Access Control | 39 "IPS Core" protections. Examples are "LDAP Injection", "Max Ping Size" and more. From technical reasons, they are still installed as part of "Access Control" even with R80.10 gateways. |
IPS by type: Engine Settings | Type: Inspection Settings | | Access Control | About 150 protections were traditionally called "IPS Protections", but in fact they are firewall behaviors. Some of them impact other access control engines. Examples are "non-compliant HTTP", "Aggressive Aging" and more. Searching for these protections in the IPS Protections page gives you a link to open them under Inspection Settings. |
Geo Protection | Geo Policy | | Access Control | Because their behavior is to allow/block access by countries, changes will be enforced by selecting to install "Access Control" policy. |
A reminder of separation by type during policy installation in R80.10:
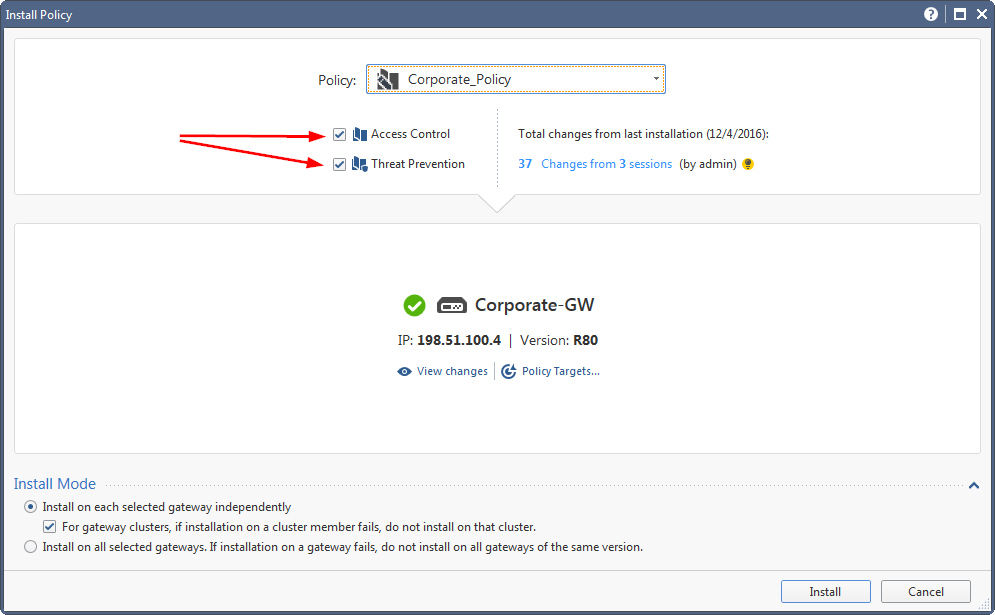
Hope this helps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bob Bent wrote:
Good info. One question: can the 39 "IPS Core" protections be seen in SmartConsole?
thx,
bob
Both of them are found at the IPS Protections page. You can differentiate by their icon and the activation options per profile. You can also filter by their type:
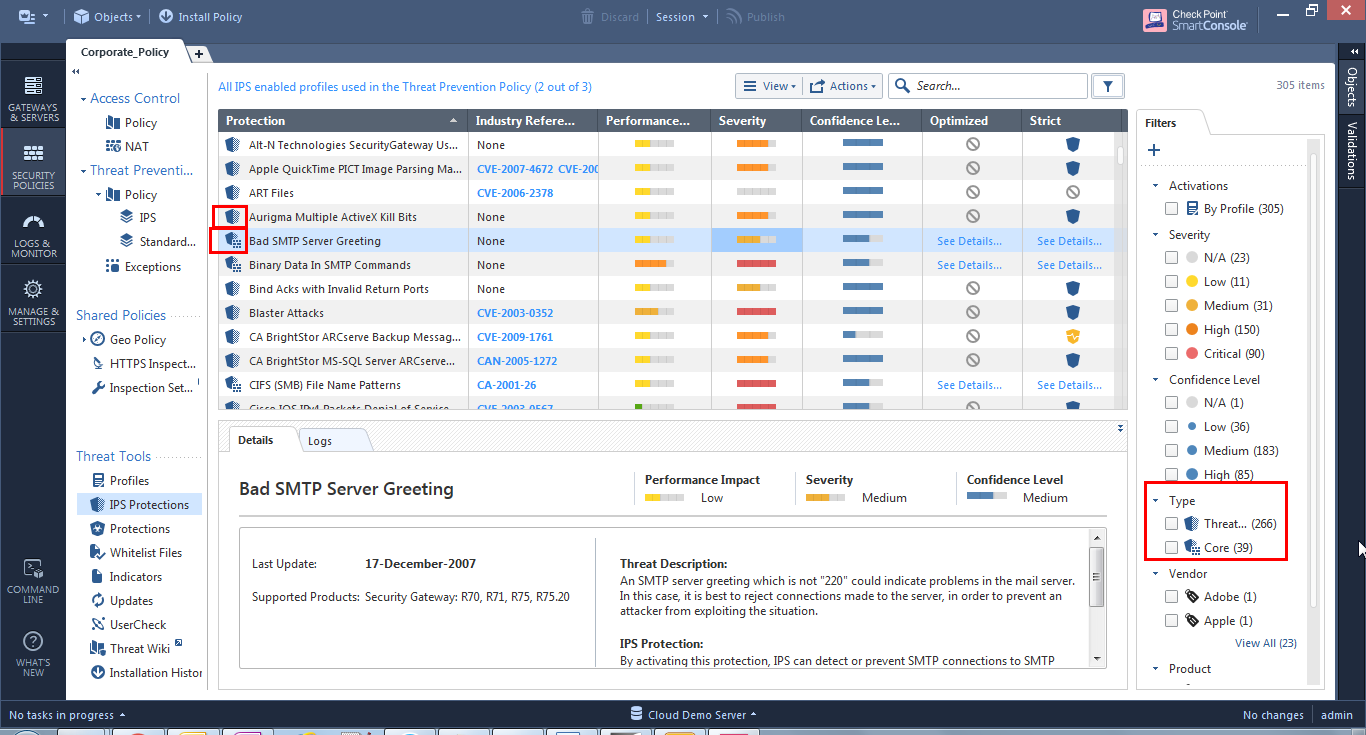
22 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
None of the protections got deleted unless the IPS engine has updated some of them as obsolete over time.
One of the concepts for R80 security management and security gateway is the separation between Access Control and Threat Prevention. We realized that those are different needs, and therefore, they are split in the user interface, as well as during policy installation - see What is the roadmap for Threat Prevention Policy management? .
R7x term | R8x term | Icon | R80.10 gateways: Install policy of type | Explanation |
|---|---|---|---|---|
Categorization by protocols | IPS Tags |
| Threat Prevention | The categorization of protections in R80 has changed. Instead of the R77 structure, every IPS protection has tags. Tags can be either for the protocol, the operating system, the application, and more. This gives a more dynamic organization structure. Also, the user can automatically disable or enable the enforcement of protections per tags - see How does R80 assist in saving time handling activation of IPS protections? |
IPS by type: signatures / protocol anomalies | Type: Threat Cloud | | Threat Prevention | Over 7000 different protections which compose the vast majority of IPS Protections. |
IPS by type: signatures / protocol anomalies | Type: Core | | Access Control | 39 "IPS Core" protections. Examples are "LDAP Injection", "Max Ping Size" and more. From technical reasons, they are still installed as part of "Access Control" even with R80.10 gateways. |
IPS by type: Engine Settings | Type: Inspection Settings | | Access Control | About 150 protections were traditionally called "IPS Protections", but in fact they are firewall behaviors. Some of them impact other access control engines. Examples are "non-compliant HTTP", "Aggressive Aging" and more. Searching for these protections in the IPS Protections page gives you a link to open them under Inspection Settings. |
Geo Protection | Geo Policy | | Access Control | Because their behavior is to allow/block access by countries, changes will be enforced by selecting to install "Access Control" policy. |
A reminder of separation by type during policy installation in R80.10:

Hope this helps
DeletedUser
Not applicable
2017-06-02
09:34 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good info. One question: can the 39 "IPS Core" protections be seen in SmartConsole?
thx,
bob
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bob Bent wrote:
Good info. One question: can the 39 "IPS Core" protections be seen in SmartConsole?
thx,
bob
Both of them are found at the IPS Protections page. You can differentiate by their icon and the activation options per profile. You can also filter by their type:

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it possible to create an exception for the ''IPS Core'' protection ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes on R80.10 its under the Manage and Settings look for the IPS blade there you should have a global exception button
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it possible to create an exception for the Core Protections for specific Source/Destination Addresses like you can with the IPS protections?
IE - I have my scanning servers that I want to bypass the core protections for, but still leave them enabled for everything else.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, if you have an R80.10+ gateway. Go to any one of the 39 Core Protections under IPS Protections, then go to its Exceptions screen. Add a new exception and select "Any" for the Protection Name which will include all 39 Core Protections. Note that you'll need to create two exceptions, one with the Source of the network that you want to exclude, and a second one with a Destination of the network you want to exclude since there is no "Protected Scope" setting available.
Attend my 60-minute "Be your Own TAC: Part Deux" Presentation
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Timothy! I also found the solution here also.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Many thank's
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's a great help Tomer !
I just have need some clarification in terms of licensing.
From what i see in my gw only inspection settings and Geo Policy are visible to be configured without enabling IPS Blade.
I was expecting that every policy installed on Access Control "layer" was not need to be IPS blade enabled, but it seems its not the case.
Can i assume that IPS Blade is only needed to Core Activation and Threat Cloud Protections ?
Another remark, for the documentation guys, that could lead people to some wrong conclusions.
Document "SmartConsole R80.10 Help", under "Understanding Geo Policy", is explicit like this :
Requires a valid IPS contract and a Software Blade license for each Security Gateway that enforces Geo Protection, and for the Security Management Server.
Thanks in advance for your time !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct, Inspection Settings and Geo Policy are part of the Access Control policy and do not require an IPS blade license or even for IPS to be enabled.
Core Activations are a bit more complicated because they are technically part of the Access Control policy, yet are managed from the Threat Prevention policy with a profile. I call this "no man's land" in my IPS Immersion Course. I'm pretty sure Core Activations will still be enforced even without IPS since any changes to Core Activations are made effective by installing the Access Control policy, not the Threat Prevention policy.
I believe the IPS blade is just for the ThreatCloud-based protections.
Attend my 60-minute "Be your Own TAC: Part Deux" Presentation
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm pretty sure Core Activations will still be enforced even without IPS since any changes to Core Activations are made effective by installing the Access Control policy, not the Threat Prevention policy.
Saying that, the only way we can change Core Activations settings is if we create a TP Policy even if we don't enable IPS blade.
Otherwise, i don't see a way do it since its the only way to configure them, afaik... Make sense ?
I wanted to confirm this, and i was trying to filter the different types of "protections" in my logs.... Should i filter by Blade:IPS for all the 4 types ?
Thanks in advance for your time !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For an R80.10+ gateway:
- Inspection Settings are logged under "blade:firewall", but the Protection Type is IPS
- Geo Policy is also logged under "blade:firewall", but the Protection Type is "Geo Policy"
- Core Activations are logged under "blade:ips"
- IPS ThreatCloud Protections are logged under "blade:ips"
Core Activations are managed with a profile, but it is not really part of the TP policy and there is only one Core Activations profile allowed per firewall, kind of like how only one IPS profile could be assigned to a gateway in R77.30 and earlier. Core Activations have definitely been an area that has caused confusion which extends into performance optimization; as a result there is much more coverage of "IPS Basics" in the third edition of my book (including Core Activations) to provide the proper foundation to make tuning decisions. Here are a few excerpts covering Core Activations from the third edition of Max Power 2020:
Click to Expand
Core Activations (39 total) exist in a kind of “no–man’s land” between ThreatCloud Protections and Inspection Settings for technical reasons. They typically enforce protocol standards via a protocol parser. Core Activations are assigned to a firewall using a separate profile, that is NOT applied to a firewall in the TP/IPS policy layers. They have the following attributes:
• Instead of the typical Inactive/Prevent/Detect options for each Core Activation, “See Details...” appears instead
• Exceptions can only be added for a single Core Activation signature at a time, and the main Threat Prevention Global & Custom Exceptions DO NOT apply
• Core Activations ship with the product and are not modified or augmented by updates from the Check Point ThreatCloud
• Under R80+ management, if configuration changes are made to existing Core Activations, they can be made active on the gateway by:
◦ R77.XX gateway: Install the Access Control Policy
◦ R80.10+ gateway: Install the Access Control Policy (NOT Threat Prevention)
• Core Activations have a “shield with firewall” icon to designate their special status and will typically have an “Advanced” screen available where the Activation can be further tuned or adjusted.
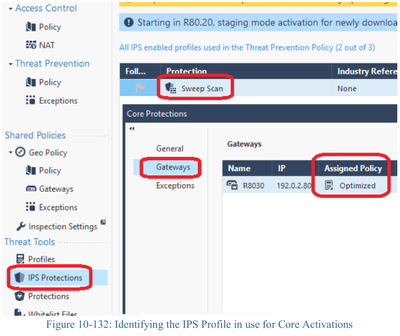
For Core Activations, in the IPS Protections window portion of the Threat Prevention policy, search for the protection “Sweep Scan”, double-click the Sweep Scan protection then select Gateways:

There is one (and only one) profile for the 39 Core Protections assigned here, make a note of it; be aware that this profile name may well be different from the one(s) in your TP policy layer!
Attend my 60-minute "Be your Own TAC: Part Deux" Presentation
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, it is very useful.
One question: in the IPS gateway properties, if we select "Detect only" as Activation Mode, it applies to Threat Cloud Type only or to all IPS Type (Threat Cloud, Core and Inspection Settings)?
Thanks!
Stefano
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to stop port scan "attack" using the IPS Core protection Host port Scan protection? The only available action for this protection is Accept or Inactive.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Accept means that the core protection is activated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Where i can find signature by protocol type like TCP flooding, Sync defender, TCP sequence verify etc. I did not find it in R80.20 IPS console.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Those protections are now part of the Access Control policy (not Threat Prevention) under Inspection Settings. See this thread:
https://community.checkpoint.com/t5/Policy-Management/R80-Inspection-settings/m-p/50787
Attend my 60-minute "Be your Own TAC: Part Deux" Presentation
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Tim.
I found it under inspection setting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Tomer,
Any idea if you can search for IPS protections by name in R80.x? I tried adding a filter, but dont see an option for that...I know in R77.x you could definitely do so 🙂
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nice😎
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
👍
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEAThu 13 Feb 2025 @ 02:00 PM (EST)
Navigating the Cyber Frontier: A Check Point Executive Briefing - AmericasFri 14 Feb 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 33: CPX 2025 terugblik!Tue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASThu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEAThu 13 Feb 2025 @ 02:00 PM (EST)
Navigating the Cyber Frontier: A Check Point Executive Briefing - AmericasFri 14 Feb 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 33: CPX 2025 terugblik!Tue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter







