- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Violation Errors: The object name must not con...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Violation Errors: The object name must not contain whitespace characters at the beginning or the end
Hi All,
At a customer we successfully upgraded from R81.10 to R81.20 Take 26 via a migration. Creating an export package, re-install the server and import the package. We used the latest deployment agent and the latest R81.20 migration tools.
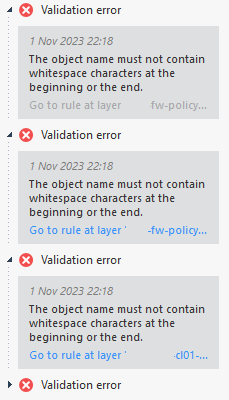
After the upgrade we noticed 6 violations in SmartConsole with the following message:
"The object name must not contain whitespace characters at the beginning or the end" with a link to a rule in the policy.
When going to this rule, we noticed some Rule Names and Comments had a carriage return, so we fixed this. But the 6 violations remain. We performed several steps trying to solve the issue.
1. Leave the Rule Names and Comment blank.
2. Copy the rule below the original and remove the original rule.
3. Create a new rule with the same objects as the original one and remove the original rule.
4. Checked sk153833 and sk161294.
I would like to mention, we use the latest version of R81.20 SmartConcole and keyboard is set to English.
But all this did not help. At some actions the violations change to grayed out, but still 6 violations.
We can not find anything wrong within the rule.
Anyone seen this before? Is there a way to solve this, or do we need to involve TAC?
Regards,
Martijn
Labels
- Labels:
-
SmartConsole
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please open a ticket with TAC and send me the number (tfridman@checkpoint.com) or post it here. I will ensure that it receives high priority. TAC will also be able to provide you with a script to remove these validations.
18 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Martijn,
Would you mind please share a screenshot? Be free to blur out any sensitive info. I never had this sort of problem in the lab or when upgrading customers from R81.20 to R81.20.
Kind regards,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The errors point you to the specific rules, right? The next thing I would try is copying the rule's UUID and showing it on the command line like this:
mgmt_cli -f json -r true show object details-level full uid "<rule UUID>"
For example:
[Expert@TestSC]# mgmt_cli -f json -r true show object details-level full uid "2b922948-da96-4c9d-a654-063e0183f9ae"
{
"object" : {
"uid" : "2b922948-da96-4c9d-a654-063e0183f9ae",
"name" : "Cleanup rule",
"type" : "access-rule",
"domain" : {
"uid" : "41e821a0-3720-11e3-aa6e-0800200c9fde",
"name" : "SMC User",
"domain-type" : "domain"
},
"track" : {
"type" : {
"uid" : "29e53e3d-23bf-48fe-b6b1-d59bd88036f9",
"name" : "None",
"type" : "Track",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
},
"color" : "none",
"meta-info" : {
"validation-state" : "ok",
"last-modify-time" : {
"posix" : 1668642045721,
"iso-8601" : "2022-11-16T23:40+0000"
},
"last-modifier" : "System",
"creation-time" : {
"posix" : 1668642045721,
"iso-8601" : "2022-11-16T23:40+0000"
},
"creator" : "System"
},
"tags" : [ ],
"icon" : "General/globalsNone",
"comments" : "No tracking.",
"customFields" : null
},
"per-session" : false,
"per-connection" : false,
"accounting" : false,
"enable-firewall-session" : false,
"alert" : "none"
},
"layer" : "38271c2f-ab44-4e25-9aa4-e219cb6e12cf",
"source" : [ {
"uid" : "97aeb369-9aea-11d5-bd16-0090272ccb30",
"name" : "Any",
"type" : "CpmiAnyObject",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
},
"comments" : "",
"color" : "black",
"icon" : "General/globalsAny",
"tags" : [ ],
"meta-info" : {
"lock" : "unlocked",
"validation-state" : "ok",
"last-modify-time" : {
"posix" : 1668642023237,
"iso-8601" : "2022-11-16T23:40+0000"
},
"last-modifier" : "System",
"creation-time" : {
"posix" : 1668642023237,
"iso-8601" : "2022-11-16T23:40+0000"
},
"creator" : "System"
},
"read-only" : true,
"available-actions" : {
"edit" : "false",
"delete" : "false",
"clone" : "true"
}
} ],
"source-negate" : false,
"destination" : [ {
"uid" : "97aeb369-9aea-11d5-bd16-0090272ccb30",
"name" : "Any",
"type" : "CpmiAnyObject",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
},
"comments" : "",
"color" : "black",
"icon" : "General/globalsAny",
"tags" : [ ],
"meta-info" : {
"lock" : "unlocked",
"validation-state" : "ok",
"last-modify-time" : {
"posix" : 1668642023237,
"iso-8601" : "2022-11-16T23:40+0000"
},
"last-modifier" : "System",
"creation-time" : {
"posix" : 1668642023237,
"iso-8601" : "2022-11-16T23:40+0000"
},
"creator" : "System"
},
"read-only" : true,
"available-actions" : {
"edit" : "false",
"delete" : "false",
"clone" : "true"
}
} ],
"destination-negate" : false,
"service" : [ {
"uid" : "97aeb369-9aea-11d5-bd16-0090272ccb30",
"name" : "Any",
"type" : "CpmiAnyObject",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
},
"comments" : "",
"color" : "black",
"icon" : "General/globalsAny",
"tags" : [ ],
"meta-info" : {
"lock" : "unlocked",
"validation-state" : "ok",
"last-modify-time" : {
"posix" : 1668642023237,
"iso-8601" : "2022-11-16T23:40+0000"
},
"last-modifier" : "System",
"creation-time" : {
"posix" : 1668642023237,
"iso-8601" : "2022-11-16T23:40+0000"
},
"creator" : "System"
},
"read-only" : true,
"available-actions" : {
"edit" : "false",
"delete" : "false",
"clone" : "true"
}
} ],
"service-negate" : false,
"service-resource" : "",
"vpn" : [ {
"uid" : "97aeb369-9aea-11d5-bd16-0090272ccb30",
"name" : "Any",
"type" : "CpmiAnyObject",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
},
"comments" : "",
"color" : "black",
"icon" : "General/globalsAny",
"tags" : [ ],
"meta-info" : {
"lock" : "unlocked",
"validation-state" : "ok",
"last-modify-time" : {
"posix" : 1668642023237,
"iso-8601" : "2022-11-16T23:40+0000"
},
"last-modifier" : "System",
"creation-time" : {
"posix" : 1668642023237,
"iso-8601" : "2022-11-16T23:40+0000"
},
"creator" : "System"
},
"read-only" : true,
"available-actions" : {
"edit" : "false",
"delete" : "false",
"clone" : "true"
}
} ],
"action" : {
"uid" : "6c488338-8eec-4103-ad21-cd461ac2c473",
"name" : "Drop",
"type" : "RulebaseAction",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
},
"color" : "none",
"meta-info" : {
"validation-state" : "ok",
"last-modify-time" : {
"posix" : 1668642046034,
"iso-8601" : "2022-11-16T23:40+0000"
},
"last-modifier" : "System",
"creation-time" : {
"posix" : 1668642046034,
"iso-8601" : "2022-11-16T23:40+0000"
},
"creator" : "System"
},
"tags" : [ ],
"icon" : "Actions/actionsDrop",
"comments" : "Drop",
"display-name" : "Drop",
"customFields" : null
},
"action-settings" : { },
"content" : [ {
"uid" : "97aeb369-9aea-11d5-bd16-0090272ccb30",
"name" : "Any",
"type" : "CpmiAnyObject",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
},
"comments" : "",
"color" : "black",
"icon" : "General/globalsAny",
"tags" : [ ],
"meta-info" : {
"lock" : "unlocked",
"validation-state" : "ok",
"last-modify-time" : {
"posix" : 1668642023237,
"iso-8601" : "2022-11-16T23:40+0000"
},
"last-modifier" : "System",
"creation-time" : {
"posix" : 1668642023237,
"iso-8601" : "2022-11-16T23:40+0000"
},
"creator" : "System"
},
"read-only" : true,
"available-actions" : {
"edit" : "false",
"delete" : "false",
"clone" : "true"
}
} ],
"content-negate" : false,
"content-direction" : "any",
"time" : [ {
"uid" : "97aeb369-9aea-11d5-bd16-0090272ccb30",
"name" : "Any",
"type" : "CpmiAnyObject",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
},
"comments" : "",
"color" : "black",
"icon" : "General/globalsAny",
"tags" : [ ],
"meta-info" : {
"lock" : "unlocked",
"validation-state" : "ok",
"last-modify-time" : {
"posix" : 1668642023237,
"iso-8601" : "2022-11-16T23:40+0000"
},
"last-modifier" : "System",
"creation-time" : {
"posix" : 1668642023237,
"iso-8601" : "2022-11-16T23:40+0000"
},
"creator" : "System"
},
"read-only" : true,
"available-actions" : {
"edit" : "false",
"delete" : "false",
"clone" : "true"
}
} ],
"custom-fields" : {
"field-1" : "",
"field-2" : "",
"field-3" : ""
},
"meta-info" : {
"lock" : "unlocked",
"validation-state" : "ok",
"last-modify-time" : {
"posix" : 1668649434218,
"iso-8601" : "2022-11-17T01:43+0000"
},
"last-modifier" : "System",
"creation-time" : {
"posix" : 1668649434218,
"iso-8601" : "2022-11-17T01:43+0000"
},
"creator" : "System"
},
"comments" : "",
"enabled" : true,
"install-on" : [ {
"uid" : "6c488338-8eec-4103-ad21-cd461ac2c476",
"name" : "Policy Targets",
"type" : "Global",
"domain" : {
"uid" : "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name" : "Check Point Data",
"domain-type" : "data domain"
},
"color" : "none",
"meta-info" : {
"validation-state" : "ok",
"last-modify-time" : {
"posix" : 1668642045629,
"iso-8601" : "2022-11-16T23:40+0000"
},
"last-modifier" : "System",
"creation-time" : {
"posix" : 1668642045629,
"iso-8601" : "2022-11-16T23:40+0000"
},
"creator" : "System"
},
"tags" : [ ],
"icon" : "General/globalsAny",
"comments" : "The policy target gateways",
"customFields" : null
} ],
"available-actions" : {
"edit" : "true",
"delete" : "false",
"clone" : "not_supported"
},
"tags" : [ ]
}
}Are there any spaces at the start or end of any of the strings?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had this issue at a few customers, not all. It was generally solved by deleting the reported rules, publishing, and recreating them manually then publish again. That might be a variation of the sequence you already tried but I remember it was solved quite quickly by doing so.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Was about to suggest the same. Just do not forget to make a note/screenshot of affected rules once deleted and published 😄 Or you can also try revert the changes from revision after all 6 rules are deleted.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Alex,
We tried to remove the rule, publish and then create the rule again. It did not help. The Validation Error is still there, but now the link in the error is greyed out. That makes sense because the rule ID is not there anymore.
I think a TAC case the is only way to solve this.
Martijn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May you share the results of the TAC case? Did you solve the issue?
I am running in the same issue with two customer ufter upgrading to R81.20 Take 41. So, in the case it is a bug, it is not fixed with Take 41.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've run into this during every single one of my upgrades into R81.20 and a TAC case is required, as they have to manually remove the violating object from postgres. Not something you can figure out yourself, and I don't think customers trying to manually hack things in postgres is supported. Wish they would release some kind of tool to let customers deal with this...
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree with @Timothy_Hall . I had to do the same few times, TAC case was needed.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please open a ticket with TAC and send me the number (tfridman@checkpoint.com) or post it here. I will ensure that it receives high priority. TAC will also be able to provide you with a script to remove these validations.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello team,
yes i have encountered the same ...
mostly i delete all texts from the affected firewall rules, publish and write the text new into the name and rulebase comments.
since there is a link in the error which let you jump to the affected rule.
mostly thats the way to go.
but i have seen one validation error that doesnt go away, since there is no link to jump to the rule any more.
this go to rule is grayed out ... strange.
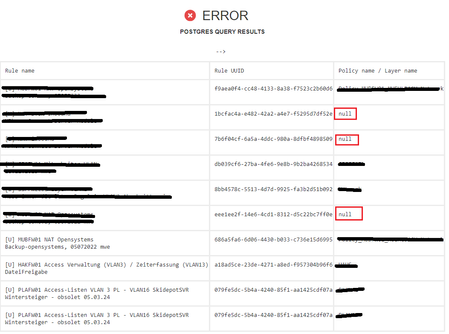
so i use the cpm_doctor script to find any White Space errors.
but regarding those rules with policy "NULL" i need to search with the posted command ..
mgmt_cli -f json -r true show object details-level full uid "2b922948-da96-4c9d-a654-063e0183f9ae"
best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, I've spoken to R&D owners and they will publish an SK with a solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
AFAIK the solution is a script, deleteValidationIncidents.sh - so this will be available for download in the future SK ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did they publish a sk in the meantime?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The script deleteValidationIncidents.sh is currently not available in any SK, so you still have to open TAC SR# for it...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same here when upgrading from 81.10 to 81.20,
Used the:
mgmt_cli -f json -r true show object details-level full uid "UID"
Found that the rule name had a "\n" in it's name:
"object" : {
"name" : "Desk to Allowed \nSites",
"type" : "access-rule",
Removed it and immediately the Violation error disappeared
Hope it helps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good to know!
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 15 | |
| 7 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter