- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Introduction to Lakera:
Securing the AI Frontier!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Trusted CA updates
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Trusted CA updates
We have started evaluating "HTTPS lite" option as our legacy explicit proxy solution replacement and I stumbled across a challenge of flaky Trusted CA updates process.
I'm referring to these two SKs:
sk132812 - How to force an update to the HTTPS Trusted Root CA list
I have couple of questions.
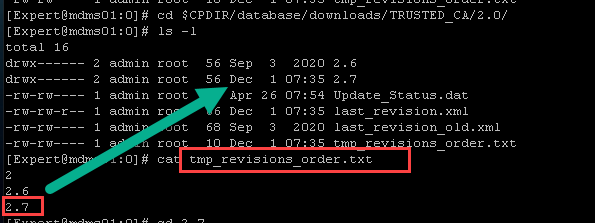
Q1: where I could find info about latest available Trusted CA update? When it was released and the version itself. By some reverse engineering of two SKs above I can see that our management thinks that the latest version is 2.7 released 1st Dec 2020:
I'm not entirely sure if indeed it is the latest version as bunch of trusted Microsoft CAs are missing.
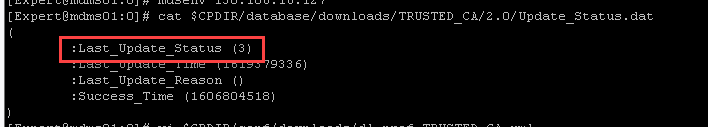
Q2: how can we interpret update status codes? "3" does not sound good to me as normally "0" or "1" would be success:
Q3: could Checkpoint publish "offline" version of updateFile.zip file in an SK for manual download in case automated way does not work. I.e. - we did not get any notification that there was a new version available until I manually fetched updateFile.zip file from management and loaded it manually using SmartDashboard
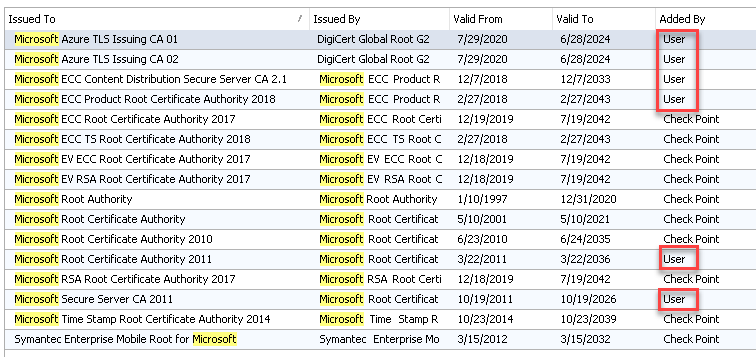
Q4: Bunch of well known CAs are still missing, see MS example below where we had to add them manually:
Just wondering if it would be smart to create some sort of collaboration so we as customers could provide feedback on "missing" CA so they get incorporated into official bundles faster? I just want to avoid constant manual chasing of trusted CAs from logs when sites cannot be categorised because root CA is not known to Checkpoint
Any other thoughts and suggestions are welcome if you have found a better way! I.e. using CCADB
- Tags:
- kz
25 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Q1 - In SmartDashboard, under HTTPSi, in advanced, you should see if a new update is available.
Q2 - AFAIK, the codes are not about mistakes. If you suspect that you did not get the lates update, please check with TAC
Q3 & Q4 - Best to take with TAC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Q1 - that's the problem Val - SmartDashboard did not show that 🙂 Even though it was downloaded and available on the disk after digging into it with CLI. Hence my rant about "flaky-ness"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Then you most probably installed the lates one already. Once again, please take it with TAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
NP, will take up with our SE. Just wondered if there was a general knowledge out there about the topic 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have the same problem and our partner told us they never saw this working for any of their customers.
We opened a TAC case and the outcome (from T3) was:
"I have consulted with our colleagues at R&D, they have informed that they are aware of this issue and are currently working on a fix. Once it is completed it will then be integrated in the Main Jumbo."
That was mid of March. Not seen something related on Jumbo Release Notes yet, so I guess its still unfixed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I'm the developer that prepared the fix.
I'd like to verify that the problem you see is indeed the one I've fixed.
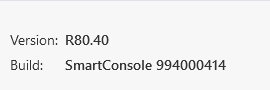
Can you please specify the exact version/build of SmartConsole (from SmartConsole's "About") dialog?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here we go:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
Do you use portable mode or did you installed the Smart Console?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
BTW, could you confirm that ver 2.7 is the latest for Trusted CAs? 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, it is
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm sorry, I'm not familiar with that aspect of the feature.
I'll try to get feature owner to answer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A few of the CAs are missing on my system as well but not all of them. The Azure CAs are missing for example. In the path I also see version 2.7 on my system.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As far as I know the Azure certificates are not missing in 2.7, you can try to install it. Did you install it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes indeed i did install 2.7 maually.
But - couple of days after manual CA addition. So that could be reason why they still show as "user" defined
That's why it would be nice to have an SK that would list the contents of update 2.7 and any new ones 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do I install the version manually? Last Update Time says: 1619516783 (today) and I don't have a pop-up in SmartDashboard. Do I have to change the value in the SK to force it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
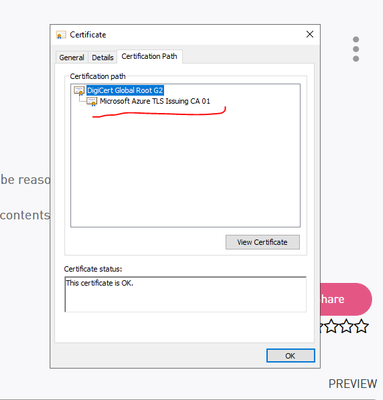
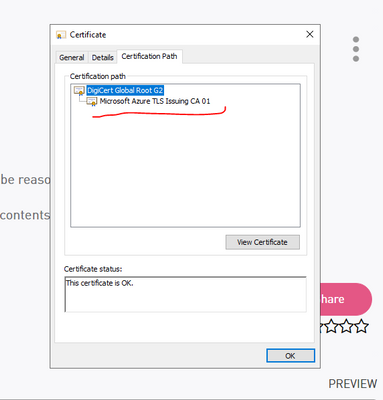
you don't need to have: Microsoft Azure TLS Issuing CA 01
you have its parent see image,
if you suspect you have missing certificate, download it, go to its properties and look if you have a parent in its chain,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I downloaded it from MDS/CMA to laptop:
and then used SmartDashboard to import:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
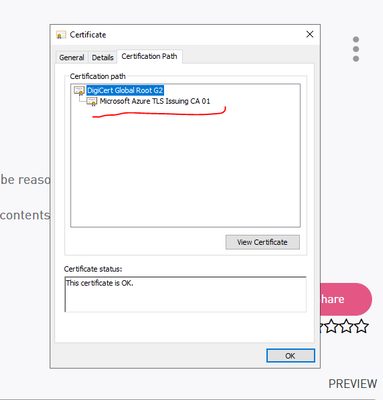
Good, you have the latest bundle, the certificate that are missing should not be there, you have its parents as shown in image.
You cannot have all the certificates in the world... so you have only the ones in the "top" to confirm all the rest.
A quick question do you use portable smart console or did you install it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SmartConsole is installed, not portable.
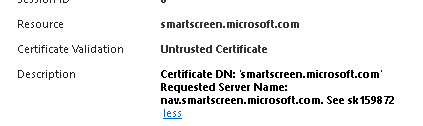
If that cert was missing we were getting "Detect" logs that site could not be categorised as cert was not trusted, for example
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That may happen before installing the last bundle,
Once you have "DigitCert Global root G2" the 'parent' in the image you don't have to install any of its descendants, this is how it works (https://knowledge.digicert.com/solution/SO16297.html#:~:text=What%20is%20a%20Certificate%20Chain,and....).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK, let me remove my manual intermediate certs and I'll let you know! 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are running "HTTPS lite" and it looks like our trusted CA list has not been updated.
My understanding is that version 2.8 is now the latest trusted CA list. How do I know which version is currently running?
I am not able to find the TRUSTED_CA directory in "$CPDIR/database/downloads/" as shown in the beginning of this post:
[Expert@mds01:0]# cd $CPDIR/database/downloads/
[Expert@mds01:0]# ls -l
total 0
drwx------ 3 admin config 23 Feb 12 2021 ADDITIONAL_HARDWARE
drwx------ 3 admin root 17 Feb 12 2021 CA_BUNDLE
drwx------ 3 admin config 20 Feb 12 2021 REPORTS_UPDATE
drwx------ 3 admin config 23 Feb 12 2021 SLIM_FW_TYPES
[Expert@mds01:0]#
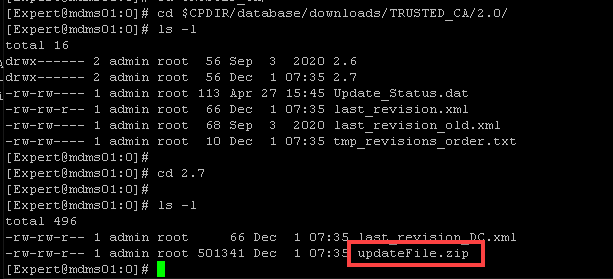
I am however able to find updateFile.zip in the following locations:
[Expert@mds01:0]# find / -name updateFile.zip
/var/opt/CPmds-R80.40/customers/fwman1/CPsuite-R80.40/fw1/conf/SMC_Files/trusted_ca/updateFile.zip
/var/opt/CPmds-R80.40/customers/fwman1/CPshrd-R80.40/database/downloads/TRUSTED_CA/2.0/2.7/updateFile.zip
/var/opt/CPmds-R80.40/customers/fwman1/CPshrd-R80.40/database/downloads/TRUSTED_CA/2.0/2.8/updateFile.zip
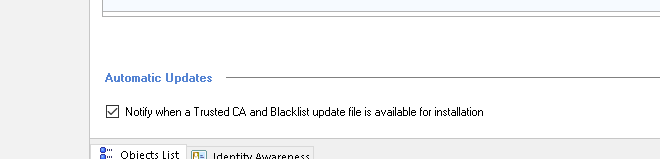
I have never been informed about any updates in the GUI though the checkbox in SmartDashboard is checked.
Do you see any risks of manually updating the trusted CA list to 2.8?
Our MDS is running R80.40, take 91 and the security gateways R80.20, take 190.
Thanks for your help!
Best regards,
Harry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Latest CA's currently are valid from January 15th, 2021 in v2.8.
On an MDS you would have to change into the specific mdsenv first and then go to the relevant TRUSTED_CA directory. The SmartConsole notification about available updates doesn't sometimes work for me as well. I don't see any risk of updating manually through SmartConsole to 2.8 as SmartConsole does various checks before it's actually importing the CA's. As always you should do recent updates of your MDS in case anything goes wrong.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your help @Danny I updated the trusted CA list manually, pushed the policies and now it seems to be working properly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
FYI, there is a new mechanism available in R81.10 as well as prior R8x jumbos that will update the trusted CA list automatically if configured.
See: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 32 | |
| 17 | |
| 6 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 |
Upcoming Events
Wed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesWed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter