Introducing Our Quantum Management Spotlight: Discover Useful Features You May Not Be Using Yet
Welcome to a new ongoing series where we shine a light on the most powerful, valuable, and sometimes less familiar features in Check Point SmartConsole.
Every few weeks, we’ll highlight key capabilities to help you get the most out of your Security Management deployment - including current tools you may not be using or upcoming features to watch for.
Have feedback or feature requests? We want to hear from you - write to us at: QuantumMgmt-Feedback@checkpoint.com
This Month’s Spotlight: 3 Features You Should Start Using Today
Get ready to boost your security operations with tools designed to save time, reduce risk, and make your life easier. These are features that don’t just work – they allow the admin to work smarter.
1. Network Feed - Real-Time, Dynamic lists at Your Fingertips
Network Feed is a flexible and powerful way to integrate dynamic data into your security policy - whether it’s threat intel from external sources or custom IP/domain lists maintained by your own team.
What it is:
- A network object that fetches dynamic data (IPs, IP ranges, domains) from an external or internal HTTP/HTTPS server.
- The data is automatically retrieved and enforced by the Security Gateway - no policy installation required.
Use cases:
- External Threat Intelligence: Instantly block malicious IPs or domains from trusted threat intel feeds (e.g., CERT advisories, commercial feeds).
- Internal IP/Domain Management: Maintain your own list of IPs or domains in a simple flat file or JSON - no need to create hundreds of host/network objects.
- Geo-blocking and dynamic allowlists: Dynamically allow partner infrastructure or block specific regions with a single object.
- Emergency Response: Instantly update protection during a live incident by modifying a central file.
Why you’ll love it:
- Fully Automated - Set it and forget it. No hands-on maintenance required.
- Super Scalable - Handle hundreds of feeds and tens of thousands of indicators.
- Extremely Flexible - Works across multiple rule bases (Access Control, HTTPS Inspection, NAT).
Supported formats: Flat text lists (e.g., .txt) or JSON (with optional jq queries for filtering).Requirements & Notes:
- Feeds must be accessible over HTTP/HTTPS.
- Each feed object supports up to 50,000 entries (IPs, CIDRs, ranges, FQDNs, wildcard domains).
- Feeds can be hosted externally or internally, on a web server, SharePoint, GitHub, etc.
Learn how to configure a Network Feed (Admin Guide)

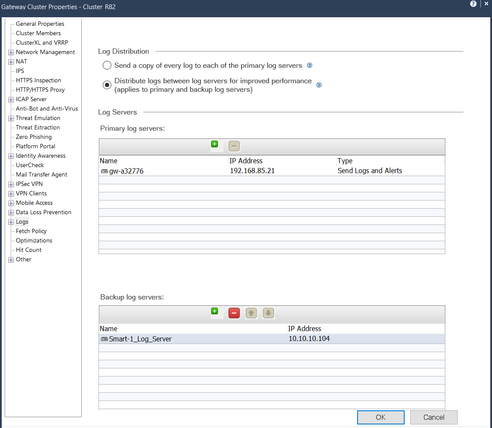
2. Dynamic Log Distribution - Scalable Logging for High-Performance Environments
As your network grows, so does your log volume. Dynamic Log Distribution is designed to scale with you - ensuring that logging traffic is efficiently balanced across multiple log servers without manual tuning.
What it is:
- A configuration option that enables Security Gateways to intelligently distribute logs across multiple log servers.
- Ensures consistent performance by automatically spreading the logging load.
Use cases:
- High-throughput environments that generate large volumes of logs.
- Multi-site deployments with regional log servers.
- Load-sensitive networks where logging spikes can impact performance.
Why you’ll love it:
- Improves Scalability - Automatically balances logs across your infrastructure.
- Optimized Performance - Reduces bottlenecks and traffic spikes to individual log servers.
- Centralized Configuration- Easily define log distribution in SmartConsole without needing advanced scripting or external tools.
How to enable it:
- Open SmartConsole and go to the Security Gateway / Cluster object.
- Go to "Logs" > "Log Distribution".
- Enable "Distribute logs between log servers for improved performance".
- Select primary and backup log servers.
- Publish changes and install policy.
Learn how to configure Dynamic Log Distribution (Logging Admin Guide)
3. SmartWorkflow - Built-In Change Control with Approval Cycles
Take the guesswork and risk out of policy changes. SmartWorkflow adds structure and security to your admin team's operations.
What it is:
- A built-in change management framework that ensures reviewal and approval of every session before it’s published.
- Allows you to define who submits changes and who approves them, enabling true separation of duties.
- Supports approval cycles, detailed comments, and the “4-eyes” principle to meet governance standards.
Use cases:
- Enforcing change control in regulated industries (e.g., finance, healthcare, government).
- Increasing transparency and oversight in multi-admin environments.
- Preventing unauthorized, incomplete, or accidental policy changes.
Why you’ll love it:
- Pre-Publish Approval - No changes are published until an authorized approver explicitly reviews and approves the session.
- Approve or Reject with Feedback - Approvers can:
- Approve and publish the session.
- Reject the changes, add comments, and allow the submitter to amend and resubmit.
- Clear Change History - View a complete audit trail of who changed what, when, and why.
- Buit-In Collaboration - Enable peer review with version tacking and team comments.
- Smart Notifications - Automatically generate email reports after each publish or install.
Learn how to configure SmartWorkflow (Admin Guide)


Ready to Try These Out?
All these features are already part of your Quantum Security Management - no additional licenses required! So why wait?
👉 Smarter log routing? Done.
👉 Dynamic threat intelligence? Ready.
👉 Built-in policy approval? Absolutely.
Let’s turn powerful features into real-world results.
Let us know what you think or suggest the next feature to spotlight: QuantumMgmt-Feedback@checkpoint.com
Stay tuned - more exciting features are just around the corner!






