- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Suspicious activity monitoring
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Suspicious activity monitoring
1. Where does the Suspicious Activity Monitoring Module comes in to picture in the packet flow diagram of Gaia R80.30?
2. How is the packet analysed & blocked based on the SAM Rules?
3. How will the gateways get updated to block the suspicious packet, once the SAM rules are specified in the Smart Console ?
Please explain.. 🙂
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Based on my experience the enforcement of SAM rules is very early in the F2F path, right around the antispoofing and Geo Policy checks and long before any policy layer lookups commence.
SAM rules can specify the typical "5-tuple" matching criteria such as src IP, dst IP, src port (I think), dst port and IP protocol. SAM rules long predate APCL, IA, and many other newer features so SAM rules cannot leverage identities or applications.
The update on the gateway when a SAM rule is applied is immediate via service 18183 (FW1_sam). The whole SAM rule thing (fw sam) is a holdover from the Intrusion Detection System (IDS) days, where an IDS was not inline and could not actively block threats. However through a process called "Intruder Shunning", the IDS could contact the firewall and tell it to block all traffic from an attacking IP address for a certain length of time. The various user interfaces into adding Suspicious Activity Rules is just performing Intruder Shunning manually.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your reply..
Is there a diagram or any 'fw ctl chain' output representing the enforcement of SAM rules and anti-spoofing?
Because i am not able to find any anti-spoofing or SAM rules in the R80.x Security Gateway Architecture (Logical Packet Flow) diagram mentioned in the below links :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is in the slow path / FW Policy. SAM rules are enforced on top of everything else.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Referring to R80.20 and newer, there are 3 closely related, but different mechanisms that are often referred to as “SAM” or “fw samp”:
- Suspicious Activity Monitor V1 (aka Suspicious Activity Monitoring Server): this is configured in SmartConsole or via “fw sam” command line and is enforced by the firewall blade. See sections 1 thru 6 of sk112061 for more details.
- Suspicious Activity Monitor V2 (aka SAM Policy Editor): this is configured via the command line (“fw sam_policy”) and is also enforced by the firewall blade. See section 7 of sk112061.
- DOS/Rate limiting: this is configured via the “fw samp” command line. This is enforced in SecureXL, which is more efficient since it is earlier in the packet flow. See sk112454 for details.
Also, be aware of “fwaccel dos rate blacklist” which can block specific IP addresses more efficiently than any of the above mechanisms.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
> Suspicious Activity Monitor V2 (aka SAM Policy Editor): this is configured via the command line (“fw sam_policy”) and is also enforced by the firewall blade. See section 7 of sk112061.
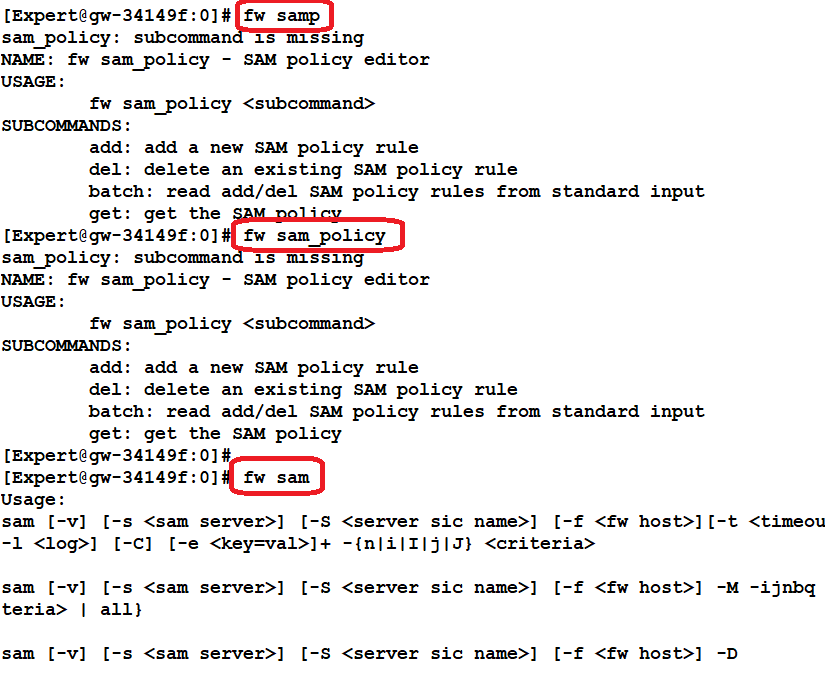
I do not believe this statement is correct, fw samp and fw sam_policy appear to be the same thing and enforced by SecureXL, not the firewall blade. Please see the screenshot below which was taken on R80.30 Gaia 3.10 JHFA Take 111:
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
fw samp and fw sam_policy are indeed interchangeable. However, fw_samp is intended to be used for DOS/Rate limiting and fw sam_policy is intended to be used for SAMv2. Notice the different help text output for the "add" command:
[Expert@edale-b1:0]# fw samp add
add: subcommand is missing
NAME: fw samp add - add a new DOS/Rate Limiting policy rule
USAGE:
fw samp add [-t <timeout>] {[-a <d|n|b>]} [-l <r |a>] [-n <name>] [-c <comment>] [-o <originator>] quota <quota limits>
OPTIONS:
-t: expiration timeout (seconds)
-a: action: either d/rop, n/otify, or b/ypass
-l: log: either r/egular or a/lert
-n: name
-c: comment
-o: originator
[Expert@edale-b1:0]# fw sam_policy add
add: subcommand is missing
NAME: fw sam_policy add - add a new SAM policy rule
USAGE:
fw sam_policy add [-u] [-f <target>] [-t <timeout>] {[-a <d|r|n|b|q|i>]} [-l <r |a>] [-n <name>] [-c <comment>] [-o <originator>] ip <ip filter arguments>
The similarities in the command lines for SAM versus DOS/Rate limiting are unfortunate. This will be addressed starting with R80.40
Regarding SecureXL versus FW enforcement:
"fw samp ... quota" rules are DOS/Rate limiting rules and are enforced in SecureXL
"fw sam_policy ... ip" rules are SamV2 rules and are enforced in FW
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Eric_Dale exactly right.
@Timothy_Hall enforcing early drops in SXL is rather risky, so it is limited for very specific functions, such as drop templates, where original drop decision is made by FW anyway.
SAM blocking rules are still in fw/UP kernel modules
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Eric_Dale please clarify what kernel and code version you ran commands fw samp add and fw sam_policy add to get that usage output, on R80.30 Jumbo HFA Take 111 kernel versions 2.6.18 and 3.10 I am not seeing the same as what you posted. I see what I posted earlier and the two commands are exactly the same thing as far as I can tell. I get that "ip" is F2F path and "quota" is SXL path, but I don't understand where those usage statements you posted are coming from.
I'm suspecting you ran those commands on R80.40? Or perhaps a scalable platform?
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I tested with R80.20 + JHF T118. It looks like that help text is in R80.20 and R80.40, but missed R80.30. I'll see that it gets into R80.30 jumbo.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 13 | |
| 13 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter