- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Spoofed traffic on port tcp/8211 from standby clus...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Spoofed traffic on port tcp/8211 from standby cluster member on Fresh 80.30 Lab setup in VMWare
Hi All,
I'm lab'ing up a 80.30 environment in VMWare with two CPs. I started with cluster config in HA mode.
I have a successful green cluster up as reported in UI and CLI (show cluster state/ show cluster members interfaces all). My VIP is responding as well, even when one shuts down.
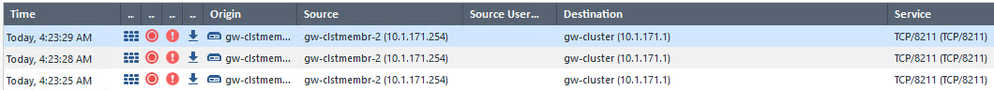
However I notice these in my system logs and I'm confused:
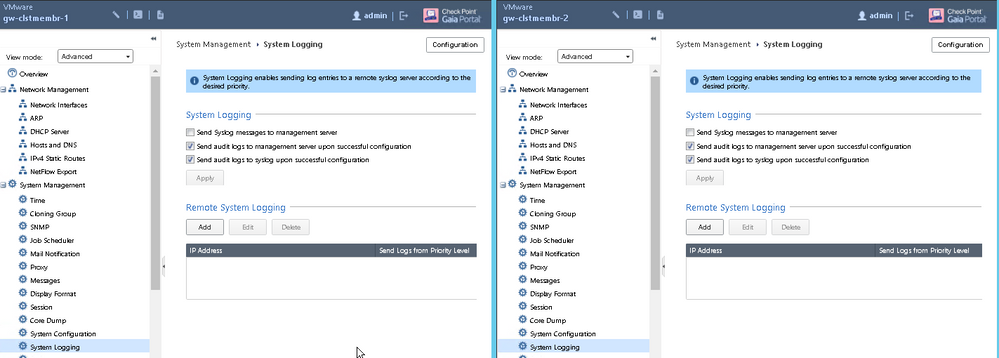
(In this screenshot, gw-clstmembr-2 is my STANDBY)
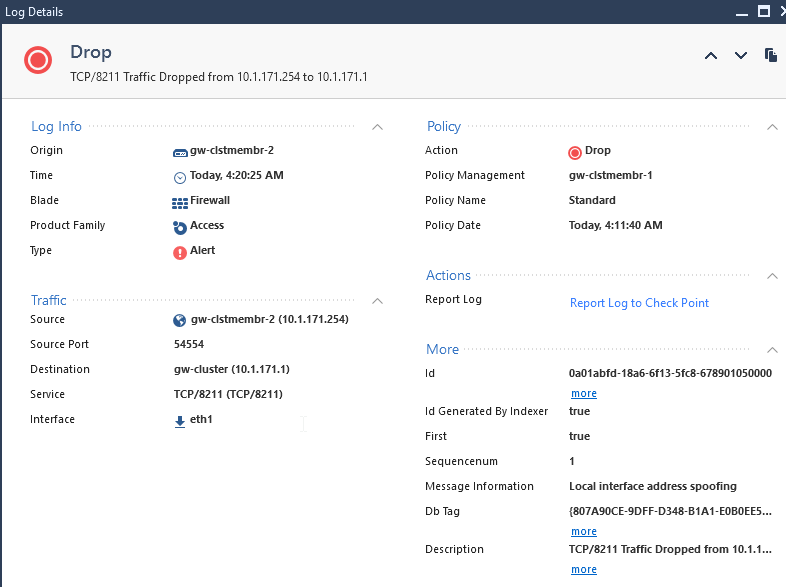
The description says "Local Address spoofing"
The interface in question has Anti-Spoofing disabled.
There is also a rule allowing traffic from 10.1.171.0/24 to "gw-cluster" / Service ANY.
The "spoofing" element made me think this is connection tracking traffic however:
1) this is NOT the Sync interface. This is a cluster only interface. Another interface is handling sync.
2) Further google-fu showed tcp/8211 is "Connections between R80 Multi-Domain Security Management Server and Log Server"
... and I'm still confused. Is it trying to send log traffic? Why is it spoofed?
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Note: the "origin" in that first screenshot is the standby cluster member which lead me to:
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
"SmartView Tracker shows drop logs "Address spoofing" from Standby cluster member for traffic that is directed to the Standby member from the MAC address of the Active member."
However, I do not have VMAC enabled (it would require promiscious mode on my vmware vswitch).
Nor is this traffic directed at the standby, its directed at the VIP.
I'm further confused.
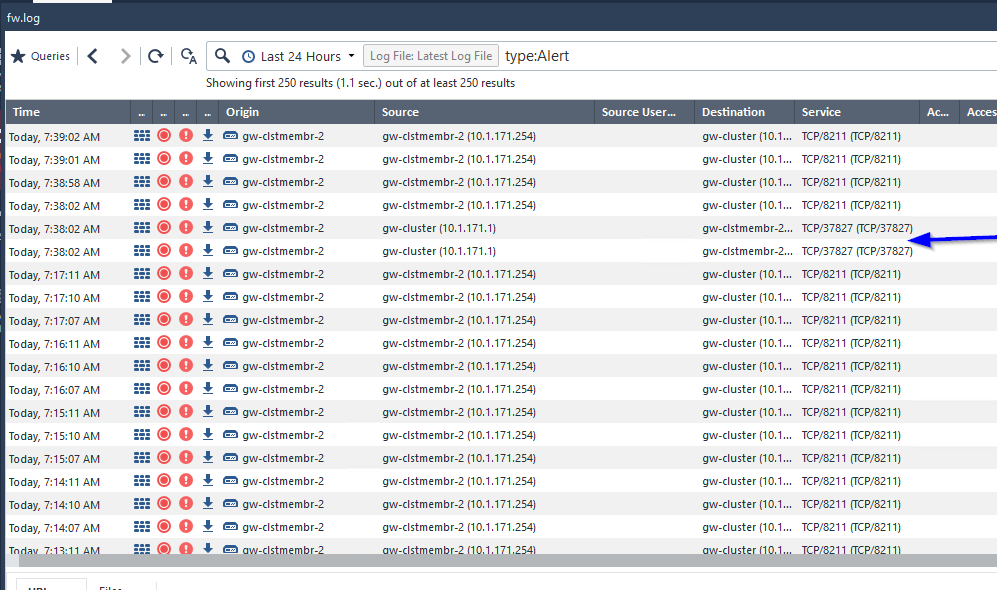
Also, admist these blocks I sometimes get these:
Functionally, everything seems to work with the exception of an error message when viewing logs (Yellow bar stating log server is disconnected) but ONLY if I enable log indexing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
on which interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
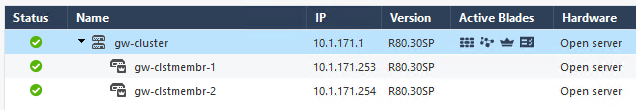
eth0 is my WAN interface
eth1 is my MGMT interface - FW1: 10.1.171.253 / FW2: 10.1.171.254 / VIP: 10.1.171.1
eth2 is my SYNC interface
eth1 is seeing this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Something is not okay with your VM networks, or log server config. the traffic is about logs FW sends to MGMT log server. It is a mystery to me why the cluster member is sending logs to cluster VIP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
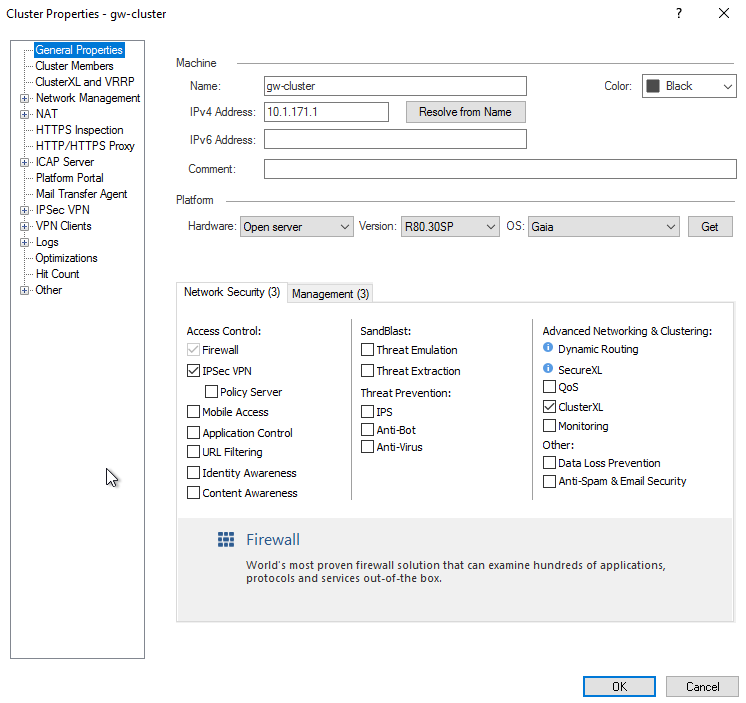
Let me post some what I think might be relevant screenshots:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Another question. Did you install Full HA by any chance? This port should not be used on just GW cluster, AFAIK...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't believe so. Don't think I've come across the term (until you posted and I only see one mention of "full ha" in the guide). I installed from Check_Point_R80.30_T200_Security_Gateway.iso
I followed the ClusterXL Failover Mode guide for HA Mode:
https://dl3.checkpoint.com/paid/48/4808360334cfd91e38eb192da36ea686/CP_R80.30_ClusterXL_AdminGuide.p...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
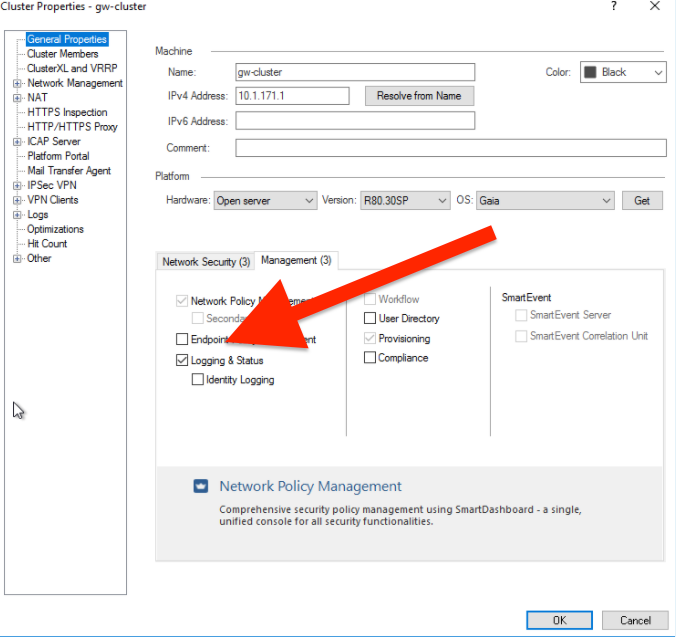
OK, I see your error. Remove this check box and reinstall policy
You defined the cluster itself as a log server with it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Will go do so now. Thank you for your quick follow up this morning.
Could you ELI5 to a CP Noob?
I assumed I need this to even be able to view logs (I'm now assuming this isn't the case after your suggestion).
Is having a log server on the same box as the Gateway/FW [that's participating in ClusterXL] not supported?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
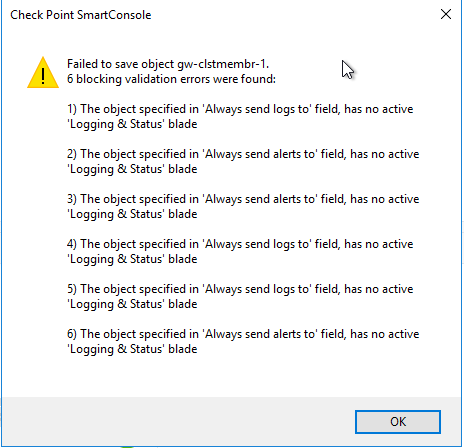
Receiving this mesage when I click "OK" to close down the gateway/cluster properties box to uncheck that.
Not finding where to clear this yet...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Attempted to follow this: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
"$FWWDIR/conf/masters file on Security Gateway is overwritten during each policy installation"
In hopes of manually removing what seems to be auto configuration? But every policy install still results in it being overwritten. Applied the action in sk102712 to the cluster object and both gateway objects in GDBEdit.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
3 posts in the moderation queue. This is the 4th. Sorry about that.
I made a mistake in following the last sk, though I required to do some more hard digging to be able to uncheck the box you speak of. I went into DBGEdit for the cluster object + the 2 gateways and cleared out send_alerts_to/send_logs_to. Only after that I was able to uncheck it.
.... and now I have no logs. While I await the moderation queue, I flipped my assumption and am now trying to back in the Security_Mgmt.iso on a 3rd VM, into the existing cluster.
A little saddened with this as otherwise I have working HA, routing, NAT'ing, etc.
Is it really not an option to have local logging only on the ACTIVE? I get the lack of "central logging" in that scenario, but still...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I almost had it but I royally messed things up and then accidentally rm-rf one of the members *conf folders. Even when I had a single router left though, I couldn't back in a mgmt gateway into an existing cluster.
I used the Python script to save my prototype objects/rules. Blew everything out. Started with the mgmt server first. It all worked out - and even took the Python script restore before I got to applying the latest JumboFix in CSUS.
ALMOST worth the exercise...
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 13 | |
| 13 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter