- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- SR Wizard failure in R80.20 SmartConsole with conn...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
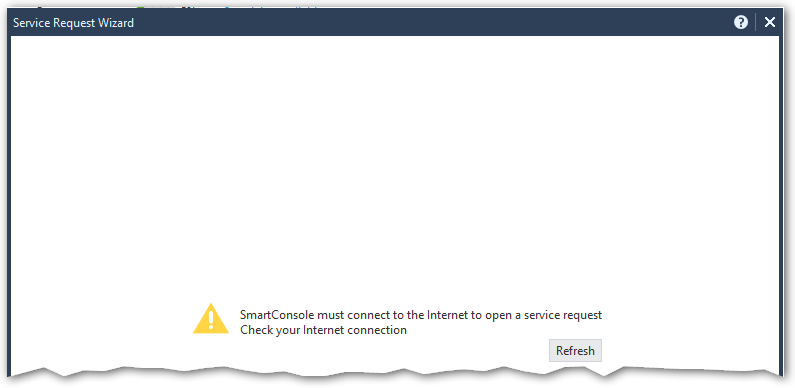
SR Wizard failure in R80.20 SmartConsole with connectivity to the Internet present
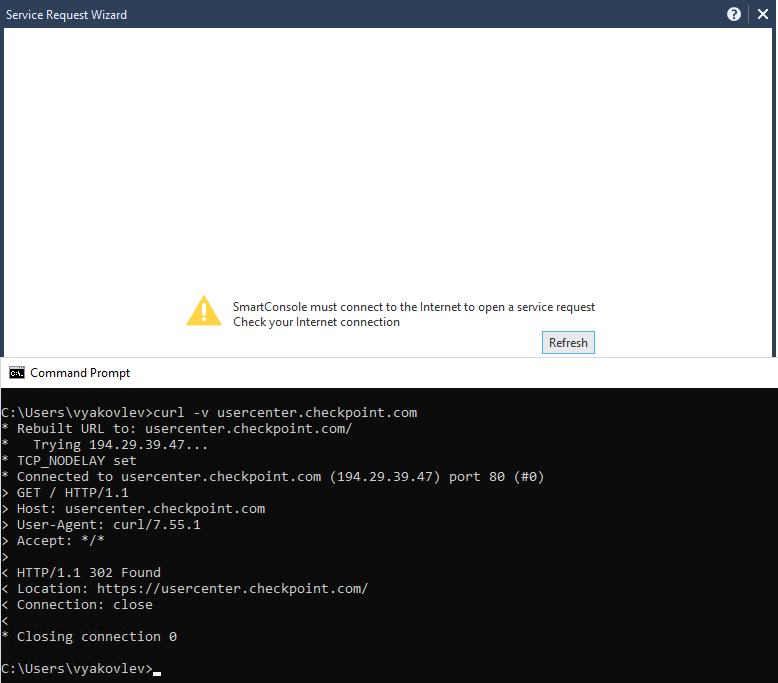
C:\Users\vyakovlev>curl -v -k https://usercenter.checkpoint.com/usercenter/services/ProductCoverageService
* Trying 194.29.39.47...
* TCP_NODELAY set
* Connected to usercenter.checkpoint.com (194.29.39.47) port 443 (#0)
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 1/3)
* schannel: disabled server certificate revocation checks
* schannel: verifyhost setting prevents Schannel from comparing the supplied target name with the subject names in server certificates.
* schannel: sending initial handshake data: sending 181 bytes...
* schannel: sent initial handshake data: sent 181 bytes
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 2/3)
* schannel: failed to receive handshake, need more data
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 2/3)
* schannel: encrypted data got 4096
* schannel: encrypted data buffer: offset 4096 length 4096
* schannel: received incomplete message, need more data
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 2/3)
* schannel: encrypted data got 767
* schannel: encrypted data buffer: offset 4863 length 5120
* schannel: sending next handshake data: sending 318 bytes...
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 2/3)
* schannel: encrypted data got 51
* schannel: encrypted data buffer: offset 51 length 5120
* schannel: SSL/TLS handshake complete
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 3/3)
* schannel: stored credential handle in session cache
> GET /usercenter/services/ProductCoverageService HTTP/1.1
> Host: usercenter.checkpoint.com
> User-Agent: curl/7.55.1
> Accept: */*
>
* schannel: client wants to read 102400 bytes
* schannel: encdata_buffer resized 103424
* schannel: encrypted data buffer: offset 0 length 103424
* schannel: encrypted data got 605
* schannel: encrypted data buffer: offset 605 length 103424
* schannel: decrypted data length: 401
* schannel: decrypted data added: 401
* schannel: decrypted data cached: offset 401 length 102400
* schannel: encrypted data length: 175
* schannel: encrypted data cached: offset 175 length 103424
* schannel: decrypted data length: 146
* schannel: decrypted data added: 146
* schannel: decrypted data cached: offset 547 length 102400
* schannel: encrypted data buffer: offset 0 length 103424
* schannel: decrypted data buffer: offset 547 length 102400
* schannel: schannel_recv cleanup
* schannel: decrypted data returned 547
* schannel: decrypted data buffer: offset 0 length 102400
< HTTP/1.1 200 OK
< Date: Wed, 21 Nov 2018 22:29:06 GMT
< Server: Apache
< Strict-Transport-Security: max-age=63072000; includeSubDomains
< Access-Control-Allow-Credentials: true
< set-cookie: UCSSID-47873-Usercenter-Group-PRD=BGPEKIMAFAAA;Domain=usercenter.checkpoint.com;Expires=Thu, 22-Nov-2018 01:15:45 GMT;Path=/usercenter;Secure;HttpOnly
< Content-Length: 146
< Content-Type: text/html; charset=utf-8
<
<h1>ProductCoverageService</h1>
<p>Hi there, this is an AXIS service!</p>
<i>Perhaps there will be a form for invoking the service here...</i>
* Connection #0 to host usercenter.checkpoint.com left intact
C:\Users\vyakovlev>
Any Ideas?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Last time it was caused by the outage on CP side.
There is also an issue with auto-upload to SR if the resultant file is larger than 25MB, I think.
In later case, you'll have to do it via SFTP.
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wikipedia says this regarding 302 Found status code:
Expecting https connection, instead of http ?
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Needless to say, the SmartConsole does have the ability to connect via HTTPS. The output of curl is there to simply illustrate that the resolution and the Internet access are present.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Even though thecurl show a https url in the text, it does not mean it is using https, you need to tell curl to use: https://usercenter.checkpoint.com
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
C:\Users\vyakovlev>curl -v -k https://usercenter.checkpoint.com/usercenter/services/ProductCoverageService
* Trying 194.29.39.47...
* TCP_NODELAY set
* Connected to usercenter.checkpoint.com (194.29.39.47) port 443 (#0)
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 1/3)
* schannel: disabled server certificate revocation checks
* schannel: verifyhost setting prevents Schannel from comparing the supplied target name with the subject names in server certificates.
* schannel: sending initial handshake data: sending 181 bytes...
* schannel: sent initial handshake data: sent 181 bytes
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 2/3)
* schannel: failed to receive handshake, need more data
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 2/3)
* schannel: encrypted data got 4096
* schannel: encrypted data buffer: offset 4096 length 4096
* schannel: received incomplete message, need more data
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 2/3)
* schannel: encrypted data got 767
* schannel: encrypted data buffer: offset 4863 length 5120
* schannel: sending next handshake data: sending 318 bytes...
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 2/3)
* schannel: encrypted data got 51
* schannel: encrypted data buffer: offset 51 length 5120
* schannel: SSL/TLS handshake complete
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 3/3)
* schannel: stored credential handle in session cache
> GET /usercenter/services/ProductCoverageService HTTP/1.1
> Host: usercenter.checkpoint.com
> User-Agent: curl/7.55.1
> Accept: */*
>
* schannel: client wants to read 102400 bytes
* schannel: encdata_buffer resized 103424
* schannel: encrypted data buffer: offset 0 length 103424
* schannel: encrypted data got 605
* schannel: encrypted data buffer: offset 605 length 103424
* schannel: decrypted data length: 401
* schannel: decrypted data added: 401
* schannel: decrypted data cached: offset 401 length 102400
* schannel: encrypted data length: 175
* schannel: encrypted data cached: offset 175 length 103424
* schannel: decrypted data length: 146
* schannel: decrypted data added: 146
* schannel: decrypted data cached: offset 547 length 102400
* schannel: encrypted data buffer: offset 0 length 103424
* schannel: decrypted data buffer: offset 547 length 102400
* schannel: schannel_recv cleanup
* schannel: decrypted data returned 547
* schannel: decrypted data buffer: offset 0 length 102400
< HTTP/1.1 200 OK
< Date: Wed, 21 Nov 2018 22:29:06 GMT
< Server: Apache
< Strict-Transport-Security: max-age=63072000; includeSubDomains
< Access-Control-Allow-Credentials: true
< set-cookie: UCSSID-47873-Usercenter-Group-PRD=BGPEKIMAFAAA;Domain=usercenter.checkpoint.com;Expires=Thu, 22-Nov-2018 01:15:45 GMT;Path=/usercenter;Secure;HttpOnly
< Content-Length: 146
< Content-Type: text/html; charset=utf-8
<
<h1>ProductCoverageService</h1>
<p>Hi there, this is an AXIS service!</p>
<i>Perhaps there will be a form for invoking the service here...</i>
* Connection #0 to host usercenter.checkpoint.com left intact
C:\Users\vyakovlev>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.20 MDS:
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We've had a few random issues with UserCenter over the last couple days--this could very well be related.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It still is an issue today.
I will be out of circulation for a week, but will have to open an SR o get to the bottom of this when i am back.
It looks really bad when I am trying to showcase the ease of use and streamlined support operations in R80.20 and run into something like this.
I'd appreciate it if you could forward this to a team handling this:

Running CPINFO from the problematic component itself works fine:
[Expert@MACPEVENT:0]# cpinfo
This is Check Point CPinfo Build 914000190 for GAIA
Checking for updates...
Updating...
Verifying CK...
Your version of CPinfo is already up-to-date, no update is required
Please provide an SR number or enter 's' to skip: s
CPinfo Creation...
Local host is not a Gateway5%
Collecting information...: 100%
Starting migrate export verification stage...
Migrate export verification stage succeeded.
Starting migrate export.
This process can take a few minutes or hours (depending on size of export) and will stop the machine.
Please wait until done. For additional options please view CPInfo's usage.
Migrate export succeeded.
Compressing output file...
Compressing output file - done
Uploading...
Initiating connection to User Center: Done.
Generating list of files to be uploaded: Done.
Sending list of files to server: Done.
Uploading MACPEVENT_22_11_2018_11_45_migrate_export_out.tgz
Uploading: 100% (61/61 MB), Done.
Uploading MACPEVENT_22_11_2018_11_45.info.tar.gz
Uploading: 100% (61/61 MB), Done.
Migrate export file created locally - MACPEVENT_22_11_2018_11_45_migrate_export_out.tgz
Done
[Expert@MACPEVENT:0]#
From SmartConsole PC:
C:\Users\vyakovlev> curl -v -k https://usercenter.checkpoint.com/usercenter/services/ProductCoverageService
* Trying 194.29.39.47...
* TCP_NODELAY set
* Connected to usercenter.checkpoint.com (194.29.39.47) port 443 (#0)
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 1/3)
* schannel: disabled server certificate revocation checks
* schannel: verifyhost setting prevents Schannel from comparing the supplied target name with the subject names in server certificates.
* schannel: sending initial handshake data: sending 181 bytes...
* schannel: sent initial handshake data: sent 181 bytes
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 2/3)
* schannel: failed to receive handshake, need more data
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 2/3)
* schannel: encrypted data got 4096
* schannel: encrypted data buffer: offset 4096 length 4096
* schannel: received incomplete message, need more data
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 2/3)
* schannel: encrypted data got 767
* schannel: encrypted data buffer: offset 4863 length 5120
* schannel: sending next handshake data: sending 318 bytes...
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 2/3)
* schannel: encrypted data got 51
* schannel: encrypted data buffer: offset 51 length 5120
* schannel: SSL/TLS handshake complete
* schannel: SSL/TLS connection with usercenter.checkpoint.com port 443 (step 3/3)
* schannel: stored credential handle in session cache
> GET /usercenter/services/ProductCoverageService HTTP/1.1
> Host: usercenter.checkpoint.com
> User-Agent: curl/7.55.1
> Accept: */*
>
* schannel: client wants to read 102400 bytes
* schannel: encdata_buffer resized 103424
* schannel: encrypted data buffer: offset 0 length 103424
* schannel: encrypted data got 605
* schannel: encrypted data buffer: offset 605 length 103424
* schannel: decrypted data length: 401
* schannel: decrypted data added: 401
* schannel: decrypted data cached: offset 401 length 102400
* schannel: encrypted data length: 175
* schannel: encrypted data cached: offset 175 length 103424
* schannel: decrypted data length: 146
* schannel: decrypted data added: 146
* schannel: decrypted data cached: offset 547 length 102400
* schannel: encrypted data buffer: offset 0 length 103424
* schannel: decrypted data buffer: offset 547 length 102400
* schannel: schannel_recv cleanup
* schannel: decrypted data returned 547
* schannel: decrypted data buffer: offset 0 length 102400
< HTTP/1.1 200 OK
< Date: Thu, 22 Nov 2018 16:28:04 GMT
< Server: Apache
< Strict-Transport-Security: max-age=63072000; includeSubDomains
< Access-Control-Allow-Credentials: true
< set-cookie: UCSSID-47873-Usercenter-Group-PRD=BGPEKIMAFAAA;Domain=usercenter.checkpoint.com;Expires=Thu, 22-Nov-2018 19:14:44 GMT;Path=/usercenter;Secure;HttpOnly
< Content-Length: 146
< Content-Type: text/html; charset=utf-8
<
<h1>ProductCoverageService</h1>
<p>Hi there, this is an AXIS service!</p>
<i>Perhaps there will be a form for invoking the service here...</i>
* Connection #0 to host usercenter.checkpoint.com left intact
C:\Users\vyakovlev>
From Cluster Members:
[Expert@MACP01:0]# curl -v -k https://usercenter.checkpoint.com/usercenter/services/ProductCoverageService
bash: curl: command not found
[Expert@MACP01:0]# curl_cli -v -k https://usercenter.checkpoint.com/usercenter/services/ProductCoverageService
* Trying 194.29.39.47...
* Connected to usercenter.checkpoint.com (194.29.39.47) port 443 (#0)
* ALPN, offering http/1.1
* Cipher selection: HIGH:!RC4:!LOW:!EXP:!aNULL:!SSLv2:!MD5:!aECDH:!EDH
* *** Current date is: Thu Nov 22 11:23:59 2018
* TLSv1.2 (OUT), TLS header, Certificate Status (22):
* TLSv1.2 (OUT), TLS handshake, Client hello (1):
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:23:59 2018
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:23:59 2018
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:23:59 2018
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:23:59 2018
* TLSv1.2 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS handshake, Server finished (14):
* TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
* TLSv1.2 (OUT), TLS change cipher, Client hello (1):
* TLSv1.2 (OUT), TLS handshake, Finished (20):
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:23:59 2018
* TLSv1.2 (IN), TLS change cipher, Client hello (1):
* TLSv1.2 (IN), TLS handshake, Finished (20):
* SSL connection using TLSv1.2 / AES128-GCM-SHA256
* ALPN, server did not agree to a protocol
* servercert: Activated
* servercert: CRL validation was disabled
* Server certificate:
* subject: OU=Domain Control Validated; CN=*.checkpoint.com
* start date: Dec 24 13:34:00 2017 GMT
* expire date: Dec 24 13:34:00 2018 GMT
* issuer: C=US; ST=Arizona; L=Scottsdale; O=GoDaddy.com, Inc.; OU=http://certs.godaddy.com/repository/; CN=Go Daddy Secure Certificate Authority - G2
* SSL certificate verify result: self signed certificate in certificate chain (19), continuing anyway.
* servercert: Finished
< HTTP/1.1 200 OK
< Date: Thu, 22 Nov 2018 16:23:59 GMT
< Server: Apache
< Strict-Transport-Security: max-age=63072000; includeSubDomains
< Access-Control-Allow-Credentials: true
< set-cookie: UCSSID-47873-Usercenter-Group-PRD=AMPEKIMAFAAA;Domain=usercenter.checkpoint.com;Expires=Thu, 22-Nov-2018 19:10:39 GMT;Path=/usercenter;Secure;HttpOnly
< Content-Length: 146
< Content-Type: text/html; charset=utf-8
<
<h1>ProductCoverageService</h1>
<p>Hi there, this is an AXIS service!</p>
<i>Perhaps there will be a form for invoking the service here...</i>
* Connection #0 to host usercenter.checkpoint.com left intact
[Expert@MACP01:0]#
[Expert@MACP02:0]# curl_cli -v -k https://usercenter.checkpoint.com/usercenter/services/ProductCoverageService
* Trying 194.29.39.47...
* Connected to usercenter.checkpoint.com (194.29.39.47) port 443 (#0)
* ALPN, offering http/1.1
* Cipher selection: HIGH:!RC4:!LOW:!EXP:!aNULL:!SSLv2:!MD5:!aECDH:!EDH
* *** Current date is: Thu Nov 22 11:25:09 2018
* TLSv1.2 (OUT), TLS header, Certificate Status (22):
* TLSv1.2 (OUT), TLS handshake, Client hello (1):
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:25:09 2018
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:25:09 2018
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:25:09 2018
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:25:09 2018
* TLSv1.2 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS handshake, Server finished (14):
* TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
* TLSv1.2 (OUT), TLS change cipher, Client hello (1):
* TLSv1.2 (OUT), TLS handshake, Finished (20):
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:25:09 2018
* TLSv1.2 (IN), TLS change cipher, Client hello (1):
* TLSv1.2 (IN), TLS handshake, Finished (20):
* SSL connection using TLSv1.2 / AES128-GCM-SHA256
* ALPN, server did not agree to a protocol
* servercert: Activated
* servercert: CRL validation was disabled
* Server certificate:
* subject: OU=Domain Control Validated; CN=*.checkpoint.com
* start date: Dec 24 13:34:00 2017 GMT
* expire date: Dec 24 13:34:00 2018 GMT
* issuer: C=US; ST=Arizona; L=Scottsdale; O=GoDaddy.com, Inc.; OU=http://certs.godaddy.com/repository/; CN=Go Daddy Secure Certificate Authority - G2
* SSL certificate verify result: self signed certificate in certificate chain (19), continuing anyway.
* servercert: Finished
< HTTP/1.1 200 OK
< Date: Thu, 22 Nov 2018 16:25:09 GMT
< Server: Apache
< Strict-Transport-Security: max-age=63072000; includeSubDomains
< Access-Control-Allow-Credentials: true
< set-cookie: UCSSID-47873-Usercenter-Group-PRD=ANPEKIMAFAAA;Domain=usercenter.checkpoint.com;Expires=Thu, 22-Nov-2018 19:11:49 GMT;Path=/usercenter;Secure;HttpOnly
< Content-Length: 146
< Content-Type: text/html; charset=utf-8
<
<h1>ProductCoverageService</h1>
<p>Hi there, this is an AXIS service!</p>
<i>Perhaps there will be a form for invoking the service here...</i>
* Connection #0 to host usercenter.checkpoint.com left intact
[Expert@MACP02:0]#
From Management Server:
[Expert@MACPMGMT:0]# curl_cli -v -k https://usercenter.checkpoint.com/usercenter/services/ProductCoverageService
* Trying 194.29.39.47...
* Connected to usercenter.checkpoint.com (194.29.39.47) port 443 (#0)
* ALPN, offering http/1.1
* Cipher selection: HIGH:!RC4:!LOW:!EXP:!aNULL:!SSLv2:!MD5:!aECDH:!EDH
* *** Current date is: Thu Nov 22 11:25:59 2018
* TLSv1.2 (OUT), TLS header, Certificate Status (22):
* TLSv1.2 (OUT), TLS handshake, Client hello (1):
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:26:00 2018
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:26:00 2018
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:26:00 2018
* TLSv1.2 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS handshake, Server finished (14):
* TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
* TLSv1.2 (OUT), TLS change cipher, Client hello (1):
* TLSv1.2 (OUT), TLS handshake, Finished (20):
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:26:00 2018
* TLSv1.2 (IN), TLS change cipher, Client hello (1):
* TLSv1.2 (IN), TLS handshake, Finished (20):
* SSL connection using TLSv1.2 / AES128-GCM-SHA256
* ALPN, server did not agree to a protocol
* servercert: Activated
* servercert: CRL validation was disabled
* Server certificate:
* subject: OU=Domain Control Validated; CN=*.checkpoint.com
* start date: Dec 24 13:34:00 2017 GMT
* expire date: Dec 24 13:34:00 2018 GMT
* issuer: C=US; ST=Arizona; L=Scottsdale; O=GoDaddy.com, Inc.; OU=http://certs.godaddy.com/repository/; CN=Go Daddy Secure Certificate Authority - G2
* SSL certificate verify result: self signed certificate in certificate chain (19), continuing anyway.
* servercert: Finished
< HTTP/1.1 200 OK
< Date: Thu, 22 Nov 2018 16:26:00 GMT
< Server: Apache
< Strict-Transport-Security: max-age=63072000; includeSubDomains
< Access-Control-Allow-Credentials: true
< set-cookie: UCSSID-47873-Usercenter-Group-PRD=AMPEKIMAFAAA;Domain=usercenter.checkpoint.com;Expires=Thu, 22-Nov-2018 19:12:39 GMT;Path=/usercenter;Secure;HttpOnly
< Content-Length: 146
< Content-Type: text/html; charset=utf-8
<
<h1>ProductCoverageService</h1>
<p>Hi there, this is an AXIS service!</p>
<i>Perhaps there will be a form for invoking the service here...</i>
* Connection #0 to host usercenter.checkpoint.com left intact
[Expert@MACPMGMT:0]#
From SmartEvent:
[Expert@MACPEVENT:0]# curl_cli -v -k https://usercenter.checkpoint.com/usercenter/services/ProductCoverageService
* Trying 194.29.39.47...
* Connected to usercenter.checkpoint.com (194.29.39.47) port 443 (#0)
* ALPN, offering http/1.1
* Cipher selection: HIGH:!RC4:!LOW:!EXP:!aNULL:!SSLv2:!MD5:!aECDH:!EDH
* *** Current date is: Thu Nov 22 11:27:12 2018
* TLSv1.2 (OUT), TLS header, Certificate Status (22):
* TLSv1.2 (OUT), TLS handshake, Client hello (1):
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:27:12 2018
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:27:12 2018
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:27:12 2018
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:27:12 2018
* TLSv1.2 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS handshake, Server finished (14):
* TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
* TLSv1.2 (OUT), TLS change cipher, Client hello (1):
* TLSv1.2 (OUT), TLS handshake, Finished (20):
* err is -1, detail is 2
* *** Current date is: Thu Nov 22 11:27:12 2018
* TLSv1.2 (IN), TLS change cipher, Client hello (1):
* TLSv1.2 (IN), TLS handshake, Finished (20):
* SSL connection using TLSv1.2 / AES128-GCM-SHA256
* ALPN, server did not agree to a protocol
* servercert: Activated
* servercert: CRL validation was disabled
* Server certificate:
* subject: OU=Domain Control Validated; CN=*.checkpoint.com
* start date: Dec 24 13:34:00 2017 GMT
* expire date: Dec 24 13:34:00 2018 GMT
* issuer: C=US; ST=Arizona; L=Scottsdale; O=GoDaddy.com, Inc.; OU=http://certs.godaddy.com/repository/; CN=Go Daddy Secure Certificate Authority - G2
* SSL certificate verify result: self signed certificate in certificate chain (19), continuing anyway.
* servercert: Finished
< HTTP/1.1 200 OK
< Date: Thu, 22 Nov 2018 16:27:12 GMT
< Server: Apache
< Strict-Transport-Security: max-age=63072000; includeSubDomains
< Access-Control-Allow-Credentials: true
< set-cookie: UCSSID-47873-Usercenter-Group-PRD=BGPEKIMAFAAA;Domain=usercenter.checkpoint.com;Expires=Thu, 22-Nov-2018 19:13:51 GMT;Path=/usercenter;Secure;HttpOnly
< Content-Length: 146
< Content-Type: text/html; charset=utf-8
<
<h1>ProductCoverageService</h1>
<p>Hi there, this is an AXIS service!</p>
<i>Perhaps there will be a form for invoking the service here...</i>
* Connection #0 to host usercenter.checkpoint.com left intact
[Expert@MACPEVENT:0]#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have the same issue and same test results. (Also on R80.20 management)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just found this; before I try it - wanted to see if you guys are still seeing this issue. I know we just migrated to a whole new support backend
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Last time it was caused by the outage on CP side.
There is also an issue with auto-upload to SR if the resultant file is larger than 25MB, I think.
In later case, you'll have to do it via SFTP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Vladimir! Appreciate the quick response. Still a cool feature, as long as we aren't sending up cpcaps. 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think it could probably be further improved by automating SFTP upload option.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 15 | |
| 11 | |
| 7 | |
| 6 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 3 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


