Depends on how often you do Access Policy installation on your firewalls 🙂
Example:
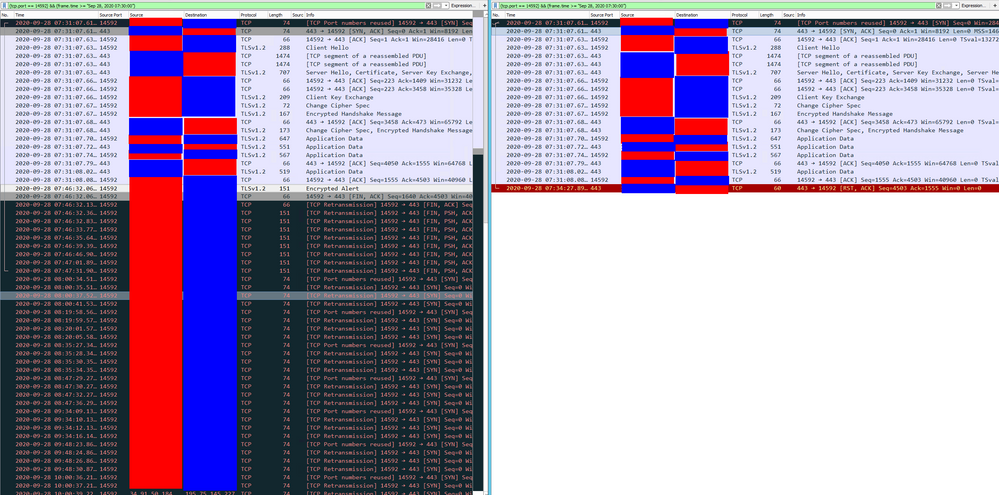
00:00 Clients opens connection to server: SYN
00:00 External firewall allows packet and creates connection table entry.
00:00 Internal firewall allows packet and creates connection table entry.
00:00 Server answers connection attempt: SYN-ACK. Packet traverses over both firewalls back to client.
00:00 Client confirms connection: ACK. Packet traverses over both firewalls back to server. Connection is fully established on all four devices (client, external firewall, internal firewall, server).
00:xx Free packet flow over this connection.
00:10 Traffic stops (client and server do not have anything to transfer at the moment, do not use keep-alives and keep connection open).
00:15 You do an access policy install on your external firewall (it is not important what you have changed). External firewalls connection persistence is set to Rematch Connections. All current entries of the connection table are copied to a separate table and deleted from the normal connection table.
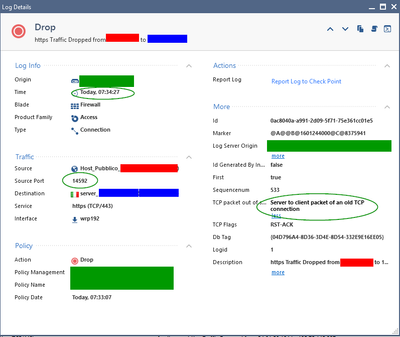
00:20 After 10 minute connection idle time, your server is closing the connection from its end (because server has configured 10 minute idle timer in this example): RST.
00:20 Internal firewall is forwarding this packet and removing its connection table entry.
00:20 External firewall is receiving this server to client packet and evaluates it agains its normal connection table: no match, because state table entry was moved to separate table. It then evaluates it against rule base: no match, because its a server to client packet and your rule is client to server (and tcp flag is not SYN). External firewall drops this packet. It never reaches the client.
00:25 Client wants to send data again over the connection, because it thinks it is still established. PSH-ACK
00:25 External firewall is receiving this client packet and evaluates it agains its normal connection table: no match, because state table entry was moved to separate table. It then evaluates it against rule base: match! It then searches the separate connection table for a former connection prior to policy install: match! It then copies the connection entry back to normal connection table, resets the connection idle timer and forwards the packet.
00:25 Internal firewall is receiving this client packet and evaluates it agains its normal connection table: no match. It then evaluates it against rule base: match! It then searches the separate connection table for a former connection prio policy install: No match, because there was no access policy install here in between and connection table entry was deleted normally at 00:20. The clients PSH-ACK packet never reaches the server. Internal firewall is silently dropping this packet. At this moment, client and external firewall are thinking the connection is still established, while internal firewall and server see this connection as closed.
00:26 Client is retransmitting its PSH-ACK packet, because it did not get an answer. Repeated.