- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Inline Layers vs Ordered Layers - Who's more e...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Inline Layers vs Ordered Layers - Who's more efficient
Hi,
Recent discussion here at the office, what is more efficient in regards to Layers. Is it better to more rules within a single layer, or use ordered layers to achieve the same goal.
@Tomer_Sole do you have anything to add?
16 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would assume that this largely depends on the production environment, type and amount of traffic and used blades...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't know that it makes much of a difference performance-wise.
What would be the reason for using multiple ordered layers?
What would be the reason for using multiple ordered layers?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To simplify and make huge policies more readable?
When large policies are setup more like zone based policies you can build a policy that is a lot simpler to look at when you can drill down into the layers where specific DMZ's are completely taken care of, in and outbound.
When large policies are setup more like zone based policies you can build a policy that is a lot simpler to look at when you can drill down into the layers where specific DMZ's are completely taken care of, in and outbound.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I could see inline layers being used to create zone-based policies.
Not sure how that would work with ordered layers.
Not sure how that would work with ordered layers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Daemon,
We currently have an inline layer with two rules at the end of it currently serving as a catch all. My plan was to either include within the layer which is accepted then have a final clean up rule with Deny all of other traffic, or make the catch all go to another and within there I then govern access.
Make sense?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Keep in mind if you use Ordered Layers, the traffic must hit an Accept rule in EACH ordered layer.
For the use case you describe, I'm not seeing where Ordered Layers makes sense.
For the use case you describe, I'm not seeing where Ordered Layers makes sense.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see to have been confused with descriptions, see my later comment. A layer within a layer is still an inline layer, that I wasn't aware of.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Inline layers are the beauty of R80.x, one of the many new features why it's better than previous versions. With ordered layers there is not much change to the earlier behavior in R77.x where you had separate firewall and application control policies.
With inline layers you can simplify complex unified policies by segmenting them into separate sub-policies. Use security zones in parent rules.
So, to answer your question inline layers are much more efficient way of creating policies. By efficiency I don't mean only the CPU power, but the simplified way building your security policies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is a layer within an Inline layer classed as an Inline layer still?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, an inline layer within an inline layer is also an inline layer.
(Say that 3 times fast)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah, that's where I'm getting confused then.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is my understanding that once traffic matches an inline layer, you will never leave that inline layer. You will either match a rule in the layer, or be dropped / accepted by the Cleanup rule at the bottom of the inline layer. However, you can match a generic inline layer (eg. All traffic to the Internet) and then match another (more specific) inline layer that is inside of the generic one (eg. Authenticated users to the Internet). However, the same rules apply. You cannot leave the inline layer -- you must match a rule in that layer, or get dropped/accepted by the Cleanup rule at the bottom of the layer.
I hope that helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I guess that I misunderstood the meaning of ordered layers.
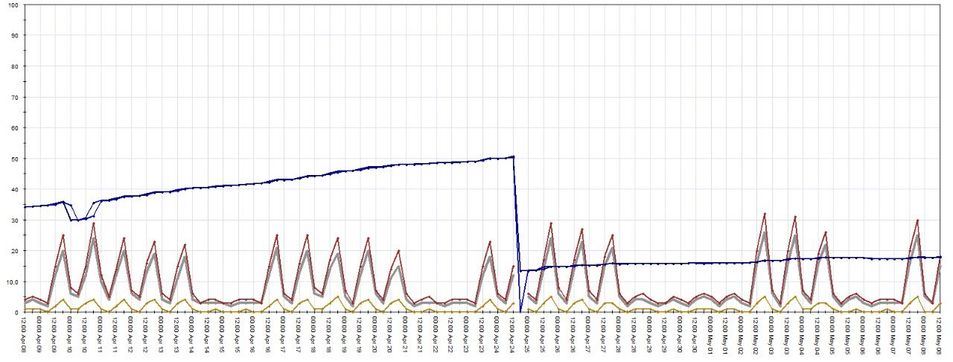
The performance impact is huge, the following graphic is from a customer where we migrated ordered layers from Access and Application control to Inline layers with Access + Application control.
Active blades: IPS, AV, AB, URLF, AppCtrl, HTTPS Inspection / Distributed deployment - Cluster of x2 5600 appliances with R80.10
Blue is memory usage, I guess that you can clearly see the before/after.
____________
https://www.linkedin.com/in/federicomeiners/
https://www.linkedin.com/in/federicomeiners/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That looks like a memory leak being reset at time of reboot 😀
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed but it isn't 🤣 I can assure you that memory consumption has lowered like 50% average.
____________
https://www.linkedin.com/in/federicomeiners/
https://www.linkedin.com/in/federicomeiners/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The reduction in memory usage shown on the graph was due to a reboot, not ordered vs. inline layers. Notice the small gap in the graph lines just before the big drop, that was while the system was rebooting and until the first set of graph data was written. This drop in memory usage is typical after a reboot since the longer a system is up, the more memory is utilized for buffering/caching of disk operations (up to a certain point that will not adversely impact the system of course). A reboot starts the memory used for buffering/caching back at a low value and it slowly grows again.
As stated in my Max Power book, I don't see a huge difference in ordered vs. inline layers as far as rulebase lookup overhead on the firewall in the F2F path (R80.10 and earlier) or the F2V path (R80.20+). It is on my to-do list to take a closer look at this in near future and try to quantify the difference a bit more. Inline layers can most definitely be easier to manage than ordered layers, and consume less of an administrator's time trying to find and modify rules in day-to-day operations.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 16 | |
| 7 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter