- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Inconsistent behavior in SmartConsole | Not sh...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Inconsistent behavior in SmartConsole | Not showing last matched rule number & name in logs
-- Edit --
As noted by @Paul_Warnagiris [ here ], there is now (at least) a workaround. 🤮
-- Original --
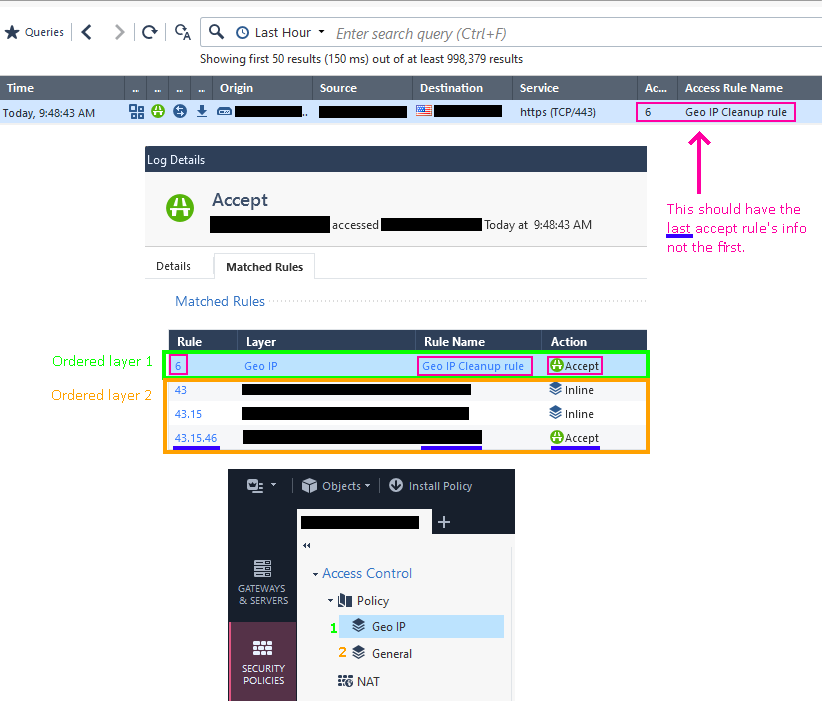
It would be nice if could set the log view to show the last matching rule number and name all the time. For some reason there's a difference for allowed and blocked traffic. If allowed, it will show the first matching rule in the logs view, if blocked, it shows the last matching rule.
This became very annoying after implementing layered policies, specifically for Geo IP filtering as discussed here. Now, the "Access Rule Number" and "Access Rule Name" column in the logs shows "Geo IP" for all Allowed traffic and the block rule number & name for all blocked traffic.
This makes the two columns in the log view practically worthless, so I'm a little suspect that there's already a fix out there, but I'm not finding anything.
Example:
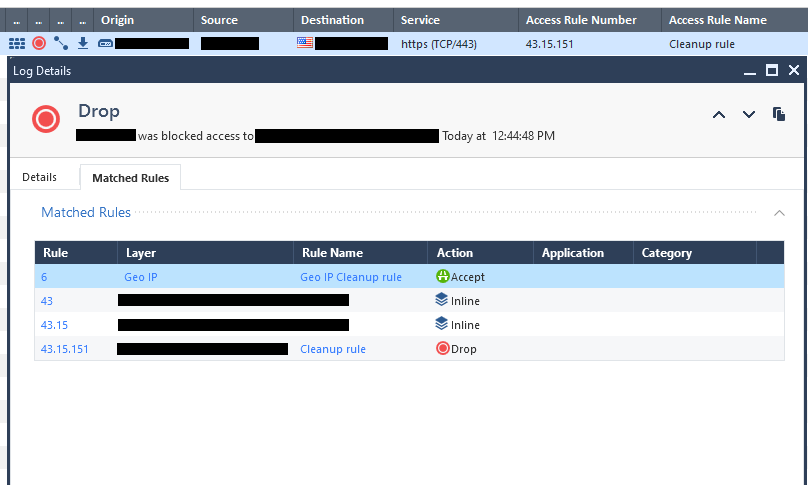
What's stranger yet, is it does the exact opposite for Drops which is even inconsistent with the above and is the correct way it should display.
It is also this way in Web SmartConsole.
- Tags:
- smartconsole
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Happy Days! Happy Days! There is finally a work around for this. Its a little crazy if you ask me, but it works just fine so its not crazy. R81.20 JHF79 or higher or R82. From this admin guide right here. https://sc1.checkpoint.com/documents/R82/WebAdminGuides/EN/CP_R82_LoggingAndMonitoring_AdminGuide/CP....
To exclude logs generated by rules in a specific a layer from the SmartConsole Logs view:
1. In SmartConsole, From the left navigation panel, click Security Policies.
2. Go to Access Control > Policy, right-click the Policy Layer whose logs you want to
exclude and click Edit Policy.
3. In the window that opens, go to the applicable layer, right-click the drop-down menu, and
select Edit Layer.
4. Add a downward arrow ↓ to the layer's name. You can add the downward arrow in two
ways:
n Copy it from here: ↓
OrHaha...copy a down arrow and put it in the layer name. Bookmark this page. I'm 100% sure this will come in handy. Thank you to all that have worked on this. You have no idea how much trouble it saves (not to mention clicks).
44 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for this feedback.
We'll try to look internally to better understand why there is a difference in behavior.
BTW, do you think that it makes sense for all customers and all cases to always show the last matching rule? (assuming that this remains a "single value" field)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, it makes sense for all customers and all cases to show the last matching rule. I think any other way changes the purpose of the log view, which is to see why a packet was allowed or blocked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
5mo later.... The "Access Rule Number" and "Access Rule Name" are default columns in almost every log view and they're completely worthless. Why is this not fixed? Am I the only one that does GEO IP Protection in the recommended way?
Here's what I see:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I dont see why you would say its worthless this way...I never have any issues showing the right rule, regardless if its ordered or inline layer. Unless Im not understanding something, it behaves exactly the way its designed.
When you say it would be nice to show last matched rule, well, the rule thats hit is technically "last matched rule", isnt it? Because, in this case, or any case for that matter, implicit clean up rule will be last rule in network layer, so the only logical option is to hit rule that blocks specific countries.
Again, sorry if Im not connecting the dots here, but thats the way I look at it.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@the_rock wrote:the rule thats hit is technically "last matched rule", isnt it?"
💯! So why is it showing the first matched rule? Going off the original post, I should see "17.45.23" for the "Access Rule Number" and "Group A Service" for the "Access Rule Name". Instead I'm seeing "6" and "Geo IP Cleanup".
My guess as to the reason you're not seeing it, is because you don't have multiple access control policies like you would if you did GEO IP in the new / recommended way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, maybe we are using different wording here :-). Regardless...just so theres no confusion, can you send screenshots of those rules you are referring to? That would clear some things.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, it looks like this in SmartConsole:
Access Control
- Policy
- Geo IP
- Rule: 6 | "Geo IP Cleanup" | Accept
- General
- Rule 17 | "GroupARules" | Inline
- Rule 17.45 | "GroupAServices" | Inline
- Rule 17.45.23 | "Group A Service" | Accept
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would still like to see it, if possible (blur out any sensitive info), but to me, if it hits rule 6, then I cant see what else is there to be hit. So, if that geo rule is hit, then it will be first AND last matched rule. Anyway, sorry mate, not trying to be difficult, but thats the way I look at this. But, if you could attach what it looks like in your rulebase, it may prove me wrong. So far, just going based on what you wrote here.
The only possible way it would hit more than 1 rule if traffic is allowed is if you have multiple ORDERED layers.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@the_rock wrote:is if you have multiple ORDERED layers.
You must not have clicked the link in the original post.
Fist sentence says "use ordered layers". 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Alright, I admit when Im wrong :). Anywho, regardless, I would STILL like to see what rules look like, that would help for sure. So, if you can attach a screenshot(s), would be awesome. I will say though, no idea if that post is indeed an official CP recommendation for geo policy, but I never do it like that. I always create geo rules way on top of network layer and it seems to work the best that way. I personally dont see sense in creating ordered layer just for geo block/allow, but again, thats just me.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@the_rock wrote:I always create geo rules way on top of network layer
Sure, but there's severe limitations to that which don't work for us.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like what exactly? Please elaborate...
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think you can answer that with "Why did Check Point create ordered layers?"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry mate, but I strongly disagree there. I am pretty positive that reason why CP created ordered layers was NOT with geo stuff in mind : - )). Maybe someone from R&D will confirm or deny that. Either way, I cant really answer your inquiry any further, unless I see what those rules you mentioned look like.
Have an amazing weekend!!
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can we please see a full example of one of those log entries?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Updated original post with example screenshot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just noticed that Drops display correctly and added another reference picture to the original post. That is very inconsistent behavior.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Still happening. I can't believe people just don't look at their rules. This tells me Check Point QA is not really testing much because they would immediately see something like this if they were. "Default Firewall view doesn't work properly with ordered layers" -- what's more obvious of an issue than that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
This behavior is expected - when traffic is accepted - show first rule, when dropped show the rule it will match the drop on.
This behavior is not related only to inline layers but separate layers policy as well (which beside being in use today, was important for backwards compatibility). This might influenced the decision.
I can strengthen Rock's guess, unified layers was introduced during R80.10 and updateable object were introduced in R80.20 if I'm not mistaken.
I understand that this is not optimal for your needs and you rather have the last rule. I think SmartEvent works very well with this though, you might consider using it. The attached is part of a view I created with recorded traffic from my lab.
Kind regards, Amir Senn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good to know thats expected, I was not aware, learnt something new today 🙂
Cheers,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Amir_Senn for the clear and accurate explanation!
Indeed there were challenges when adapting the log behavior that had a single rule match to the new paradigm where multiple matches are possible.
In the last year or so, we see a significant rise in ordered layer usage. Both by customers trying to logically separate parts of their policy, and by our own products who leverage ordered layers to add additional enforcement capabilities (such as Playblocks and IoT).
In case of a block action, I believe that it's the correct choice to put the rule that actually blocked the traffic. Since ordered layers are evaluated in order, that's the first matching rule that has a block action.
In case of an accept action, we understand the feedback that the first layer may not be the correct choice to use in the log. However, the last layer doesn't always make sense either.
@Meital_Natanson's team is looking into a slightly more "intelligent" mechanism for Accept logs. In this mechanism, Check Point's extra layers (Playblocks, IoT) will be skipped when choosing the rule to place in the log, so that we will choose the layer that matters more to the admin. In case you have your own ordered layer that you want to skip, you'll be able to mark it with a tag or prefix, and we'll take that into account as well.
We'll update the community once we have something available to try.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You might be able to manipulate this by using this as a separate layers policy instead of unified with inline layers. If the first layer would be Geo policy it would show it first.
Kind regards, Amir Senn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Many of our customers don't like this showing first accept rule number being Playblocks rule and not the actual network layer rule.
We would like to see the network layer rule number easily on main view, without having to open the individual log record.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
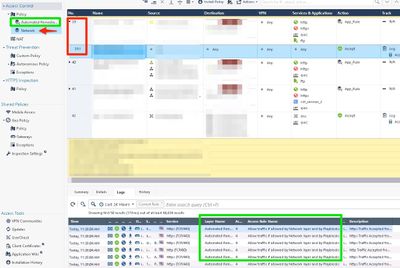
I will reiterate the word "worthless." If this is expected design, then the it is terrible. Everything in my logs on every gateway is now showing being accepted at rule #4. This is the new automated remediation rule named "Allow traffic if allowed by Network layer and by Playblocks" This effectively makes filtering by rule number useless. You can't move the automated remediation or its not effective. This is just pretty ugly no matter which way you cut it if you are working these logs on a daily basis. YUK! The only way to get what I'm looking for at this point is to click each rule and then click on "matched rule." Four clicks per log entry when I used to be able to filter by rule number with one click. I can't emphasize how bad this is. Every one of my customers using playblocks is complaining about this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Respectfully, I would disagree that its terrible. To me, it makes total sense, specially if traffic is matched on multiple rules/layers.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you ever use the rule number as a filter in SmartLog?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Absolutely I do.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you use playblocks?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Used to, just as PoC, dont believe we have any customer using it atm.
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 14 | |
| 8 | |
| 7 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter