- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Inbound https inspection only
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Inbound https inspection only
Hello,
I wanted to turn on Inbound https inspection only and not outbound. Is there a way to do this?
Going through documentation it says when you enable https inspection on the gateways, it creates an outbound CA certificate as well which means outbound https inspection is enabled as well.
Thanks,
Chandru
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect what you're doing in this case won't work without another IP address.
You can try creating a NAT rule to redirect traffic to the external IP on port 443 to the relevant server on the backend.
If there is more than one IP involved on the backend, this definitely won't work.
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Chandhrasekar_S,
I don't know what version your gateway is but I believe you can still follow the guide for R80.10 as below:
I would focus on this section:
To enable inbound HTTPS traffic inspection:
- From the SmartConsole Gateways & Servers view, edit the Security Gateway object.
- Click HTTPS Inspection > Step 3.
- Select Enable HTTPS Inspection.
- Import server certificates for servers behind the organization Security Gateways.
- Define an HTTPS inspection policy:
- Create rules
- Add a server certificate to the Certificate column of each rule.
Let us know if that answers your question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Nick,
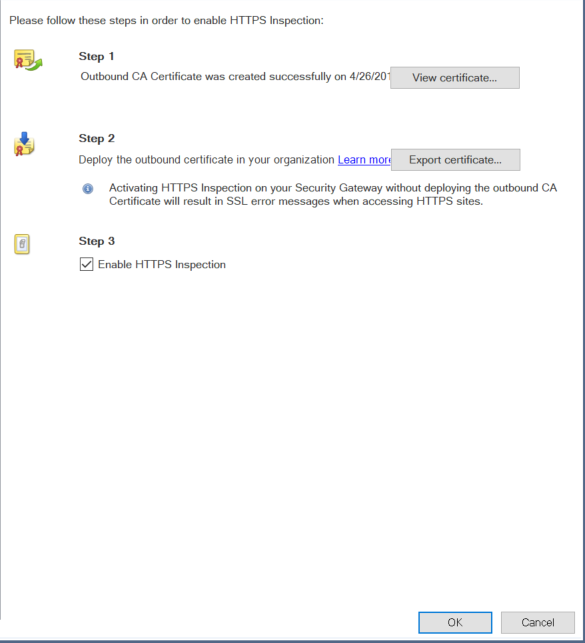
We are running R80.10 gateways. Under HTTPS Inspection
Step1 : Outbound CA certificate creation
Step2: Deploy outbound certificate in your organization (Which is we distributing the CA certificate to all the internal systems )
Its only in Step3: you enable HTTPS inspection, hence my question is it not possible to enable https inspection for inbound traffic only.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I can see the confusion but as far as I'm aware, it's still the same box that you have to tick in order to enable HTTPS inspection regardless of direction.
The main difference is that instead of exporting the outbound certificate etc you will need to import the server's certificate in the section shown below:
To my knowledge, you would need to import a certificate as I don't think you have the option to generate an inbound one on the gateway in the same way that you can for outbound certificates.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Nick. Yes I am aware of importing the internal server SSL certificates etc for configuring https inbound inspection.
I believe we need to delete the default https inspection rule, in order to stop the outbound https inspection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're correct.
While you may have to configure an outbound certificate as part of the process, if there is no outbound HTTPS Inspection rule, you won't get outbound HTTPS Inspection.
While you may have to configure an outbound certificate as part of the process, if there is no outbound HTTPS Inspection rule, you won't get outbound HTTPS Inspection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bear with me as I try to resurrect this thread.
We're using the Checkpoint outbound SSL/DLP inspection and that works well. We tried once to configure the inbound SSL inspection for the sake of IPS/Malware control but were not successful - unfortunately, it's been a while and details on that are somewhat sketchy.
Did anyone run into complications by configuring the inbound SSL inspection? Any one-off site issues? Any special cipher issues (as in, some supported/some not)? Anything else I need to know before trying this again? We on r80.40 and plan to upgrade to r81 1Q.
Thanks in advance.
KA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm also looking to do only inbound (from Internet) HTTPS inspection. Currently on R80.40, but plan to upgrade to R81 later this year.
The step in the documentation of "Create Rules" is pretty friggin' vague. We have multiple hostnames an only one external IP address, so I need the ability to route each SNI hostname to a different internal IP. Using NGINX configuration as an example:
server {
listen 443 ssl http2;
server_name web1.mydomain.com;
location / {
proxy_pass https://10.20.30.44:443;
proxy_set_header Host $host;
proxy_http_version 1.1;
}
ssl_certificate web1_mydomain_com.cer;
ssl_certificate_key web1_mydomain_com.key;
ssl_ciphers ECDH+AESGCM:ECDH+AES128+SHA:RSA+AES128+SHA;
ssl_prefer_server_ciphers on;
}
server {
listen 443 ssl http2;
server_name web2.mydomain.com;
location / {
proxy_pass https://10.20.30.65:443;
proxy_set_header Host $host;
proxy_http_version 1.1;
}
ssl_certificate web2_mydomain_com.cer;
ssl_certificate_key web2_mydomain_com.key;
ssl_ciphers ECDH+AESGCM:ECDH+AES128+SHA:RSA+AES128+SHA;
ssl_prefer_server_ciphers on;
}
What would this look like in CheckPoint's HTTPS inspection rules? I see fields for source, destination, services, and certificate, but no "translated destination" or "translated services" equivalent to the way you'd see in a NAT rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It would look like the answer I gave in this thread: https://community.checkpoint.com/t5/Security-Gateways/Is-there-SNI-support-for-inbound-HTTPS-inspect...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
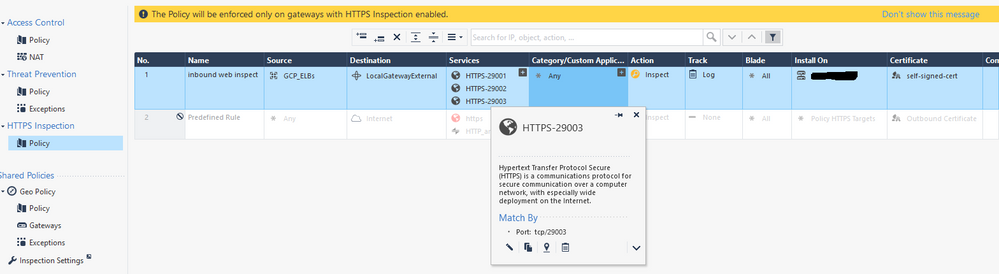
Right, that shows how to match hostnames with server certificates, but doesn't address how to actually route the requests to the backend web server after inspection. Here's my screenshot in R80.40:
When I got to the website, I do get the correct certificate, but the CheckPoint's GAIA portal is displayed. This heavily implies the CheckPoint is just fowarding the traffic to itself, since I have the Platform portal set to "accessible only through internal interfaces"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect what you're doing in this case won't work without another IP address.
You can try creating a NAT rule to redirect traffic to the external IP on port 443 to the relevant server on the backend.
If there is more than one IP involved on the backend, this definitely won't work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
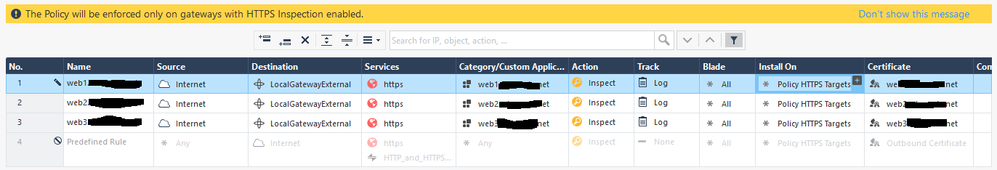
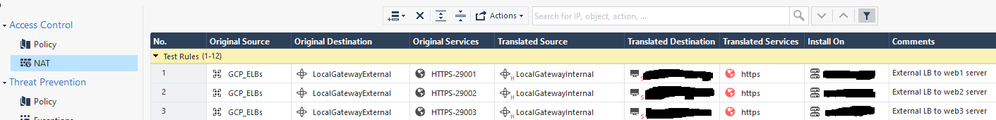
OK, so basically another HTTPS proxy will need to do the conversion between hostname and IP address/port. That's actually fine: I didn't mention it for the sake of simplicity, but this is a cloud deployment where we terminate the site on external load balancers and they do that very well with a minimal cost.
So, I just have each hostname hit a different external port on the CheckPoint cluster, and make some NAT rules to route to the corresponding internal web server:
Then write an inspection rule for those ports. No need to configure hostname, since that's already being done on the external load balancer. Likewise, a self-signed cert is fine since it doesn't perform backend server cert validation.
The one thing that got me: the firewall policy must explicitly allow the CheckPoint's internal interface to talk to the backend web server. This makes sense in hindsight since CheckPoints usually need an explicit rule when they initiate a connection, just was confusing to troubleshoot since the CheckPoint was reverting to bypass after a few seconds, giving the appearance that the inspection was slow or unreliable.
I would think that NATing port 443 on the external interface would break the SSL VPN features, so that may not be a viable solution for everyone.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 15 | |
| 13 | |
| 9 | |
| 8 | |
| 6 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter