- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Identity Collector - Cisco ISE SXP mappings su...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Identity Collector - Cisco ISE SXP mappings support
Hi,
I've been doing some testing with an R80.20 gateway, Identity Collector and Cisco ISE 2.4 pxGrid.
I've managed to interconnect these components so the basic communication is working fine (the certificate setup is quite cumbersome to be honest).
I'm am trying to get SXP-learned IP-SGT mappings into the CP IA blade, but it seems the identity collector is not picking these up. Does this mean that identity collector will only learn IP-SGT mappings from dynamic user sessions and not from SXP-learned IP-SGT mappings?
E.g. I've got the following static mapping on my test switch:
cts role-based sgt-map 172.20.21.151 sgt 6
Which is then learned over SXP by ISE: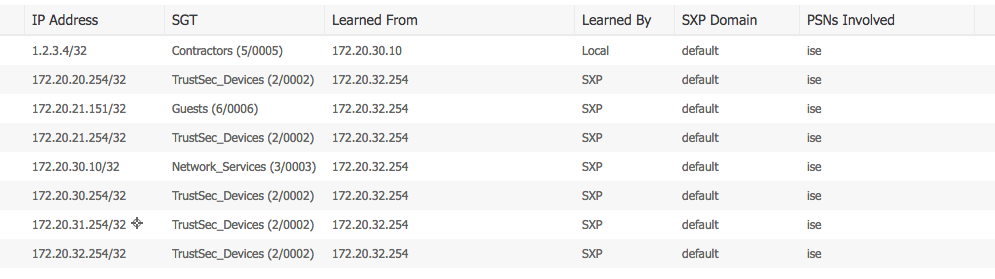
I've tried adding and removing the mappings as well but no mappings are being received on the collector, even though it is fully connected to pxgrid (and has an approved connection).
The identity collector does not seem to receive these SXP mappings at all... the ISE is set to publish these on pxgrid:
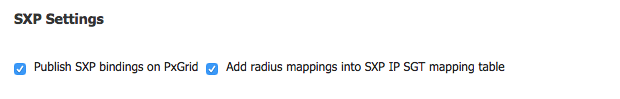
If this is not supported right now, is this on the roadmap?
Thanks,
Tom.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Of course. Go to the CloudGuard Controller admin guide, chapter about ISE
23 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you follow this steps in Identity Collector Reslese Notes ?
---
4. Optional: If you want to enforce the Cisco Security Groups Tags (SGTs) on the Gateway:
a. In the Users and Administrators menu, click Create Group > User Group > New Group.
b. Name the new group: CSGT-<SGT_NAME>.
c. Assign the group to an Access Role.
5. Install policy.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, I used the new "Identity Tags" feature instead. cfr https://community.checkpoint.com/thread/8800-how-to-use-identity-awareness-tags-in-r8020m1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could you share what you did with certificates?
I’m struggling with it also and not getting much support from our ISE admins.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, it is pretty messy to get working.
I basically generated a self signed client certificate from the ISE web interface (Adminstration -> PXgrid Services -> Certificates).
Converted that p12 file to .jks with "keytool" (you need the Java SDK installed for that)
$ keytool -importkeystore -srckeystore win2016-1.lab.p12 -destkeystore client.jks -srcstoretype PKCS12
Importing keystore win2016-1.lab.p12 to client.jks...
Enter destination keystore password:
Re-enter new password:
Enter source keystore password:
Entry for alias win2016-1.lab_ successfully imported.
Also exported the pxgrid ISE certificate, converted that to DER with openssl
$ openssl x509 -outform der -in OUCertificateServicesSystemC.pem -out iselab.der
And then converted that to a .jks with Java Keytool:
$ keytool -import -alias ise.lab -keystore server.jks -file iselab.der
Enter keystore password:
Re-enter new password:
Owner: CN=ise.lab, OU=Certificate Services System Certificate
Issuer: CN=Certificate Services Endpoint Sub CA - ise
Serial number: 53b3e07890554133b93b0e9d3fb77d93
Valid from: Thu Nov 22 08:45:29 CET 2018 until: Thu Nov 23 08:45:24 CET 2028
Certificate fingerprints:
SHA1: 92:87:FA:0E:E5:62:1B:46:3A:15:00:13:3E:F1:7D:78:4D:78:F4:ED
SHA256: F2:F4:80:2F:DD:4B:6F:24:03:66:32:5A:6A:87:48:C1:DF:0B:CC:A1:ED:E3:80:94:AD:AA:BD:0B:40:7D:1B:41
Signature algorithm name: SHA256withRSA
Subject Public Key Algorithm: 4096-bit RSA key
Version: 3
Extensions:
#1: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 7B AE 66 EA 2F 60 6F 61 FA 12 64 4E BF 74 52 FD ..f./`oa..dN.tR.
0010: 32 AD BE 88 2...
]
[CN=Certificate Services Node CA - ise]
SerialNumber: [ 1d51f5ee bb2445aa 9328ac72 6a7858a1]
]
#2: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:false
PathLen: undefined
]
#3: ObjectId: 2.5.29.37 Criticality=true
ExtendedKeyUsages [
serverAuth
clientAuth
]
#4: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Non_repudiation
Key_Encipherment
]
#5: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 20 86 63 F5 C1 02 3F 1D 8D 45 41 74 15 A6 C4 48 .c...?..EAt...H
0010: 63 F5 31 41 c.1A
]
]
Trust this certificate? [no]: yes
Certificate was added to keystore
I then used these certificates in the Identity Collector setup. You also have to "approve" the pxgrid client in ISE (also under "Pxgrid services" the first time it connects.
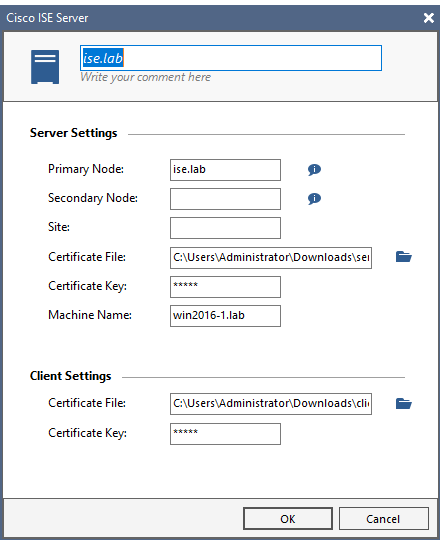
I had some issues to make it connect, but that was caused by the fact that I had not added the ISE to a query pool in Identity Collector. It will not connect if it is not part of a query pool...
Good luck,
Tom.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, now it's clear with certs, i was not aware that from pxgrid ISE certificate provided and was trying to use same cert for client/server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well the pxgrid api doc speaks of generating the client cert on the client, that probably will work as well but you definitely need a different cert for client and server...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
Is there a way to push the collector to connect to ise?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to create query pool for that..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did, and also tied the query pool to the gateway. The collector and gateway are connected, but ISE does not show any attempts from the identity collector to connect, there are no pending requests... Now I did issue a client cert without CSR, I do not know if that matters...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you ever get your issue resolved?
I think we are in the same situation, I've created the client and server certificates (jks) and created the identity source and added it to a Query Pool, but no luck.
Wireshark shows that there is no trafik to or from our ISE.
Edit: Nevermind, hadn't installed JRE...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Reading all this i would rather suggest to involve TAC in configuration...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
They will not support with generating certs on ISE for sure ![]() as documentation state, "follow Cisco pxGrid documentation"
as documentation state, "follow Cisco pxGrid documentation"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What i meant was help by TAC to get SXP-learned IP-SGT mappings into the CP IA blade, the certs for communication were configured successfully already - did you not read the original question ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, I doubt Cisco TAC will want to help with the way a checkpoint product (identity collector) consumes SXP IP-SGT mappings. Also, this is a test lab setup for which I have no support contract... I was just hoping some of the checkpoint developers would be able to confirm if it is supported or not 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have never talked of Cisco TAC here in community.checkpoint.com, but of CP TAC and can not understand why you do assume something else - but if you do not have any support contract and no CP customer in the back that needs this configured you are very well off and can just forget about this as an academic issue...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My mistake, when you say "TAC" I immediately think of Cisco TAC 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As i do nothing with Cisco, for me it is always CP TAC 😉
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tom,
Did you ever deploy or do you use identity based access control (in combination with SGT's) in a production environment and could you share your experience's with me?
I try to collect as much information as possible for a project. A question that is still on my list is "Reliability". Since there are no use cases available i am trying to figure out if this solution is realable enough to use in a production environment. With our experiences regarding Identity Awareness in the back of our heads, this has become a very important aspect. To give you an indication, this solution must be able to handle 5000+ users with ease and we cannot permit any malfunctions...
Regards,
Jelle Hazenberg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does Identity Collector support IP-SGT mapping?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The recommendation is to use GloudGuard Controller to import SGT-IP though REST API
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your reply, do we have any document or guide for this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Of course. Go to the CloudGuard Controller admin guide, chapter about ISE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks a lot for your big help, it is work😀
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 16 | |
| 11 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


