- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: How does R80 assist in saving time handling ac...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
How does R80 assist in saving time handling activation of IPS protections?
Other than the new user interface, which features in R80 SmartConsole reduce the time required to decide activation of IPS protections?
- Tags:
- ips
- protections
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The IPS Protections view in R80 leverages the new stronger back-end. Protections load and get filtered much faster than previous versions. As the Management server is more powerful, the SmartConsole process no longer needs to load all the protections into its memory but rather uses paged results, which reduces the process size and the dependability on Windows hardware.
The view also had a user experience overhaul, making working on the protections a more intuitive work. We believe that this is important in saving time and giving more clear information to the user.
The bottom pane presents logs per protection. By observing actual traffic that was matched to the protections, the administrator can make faster decisions in changing the protection actions.
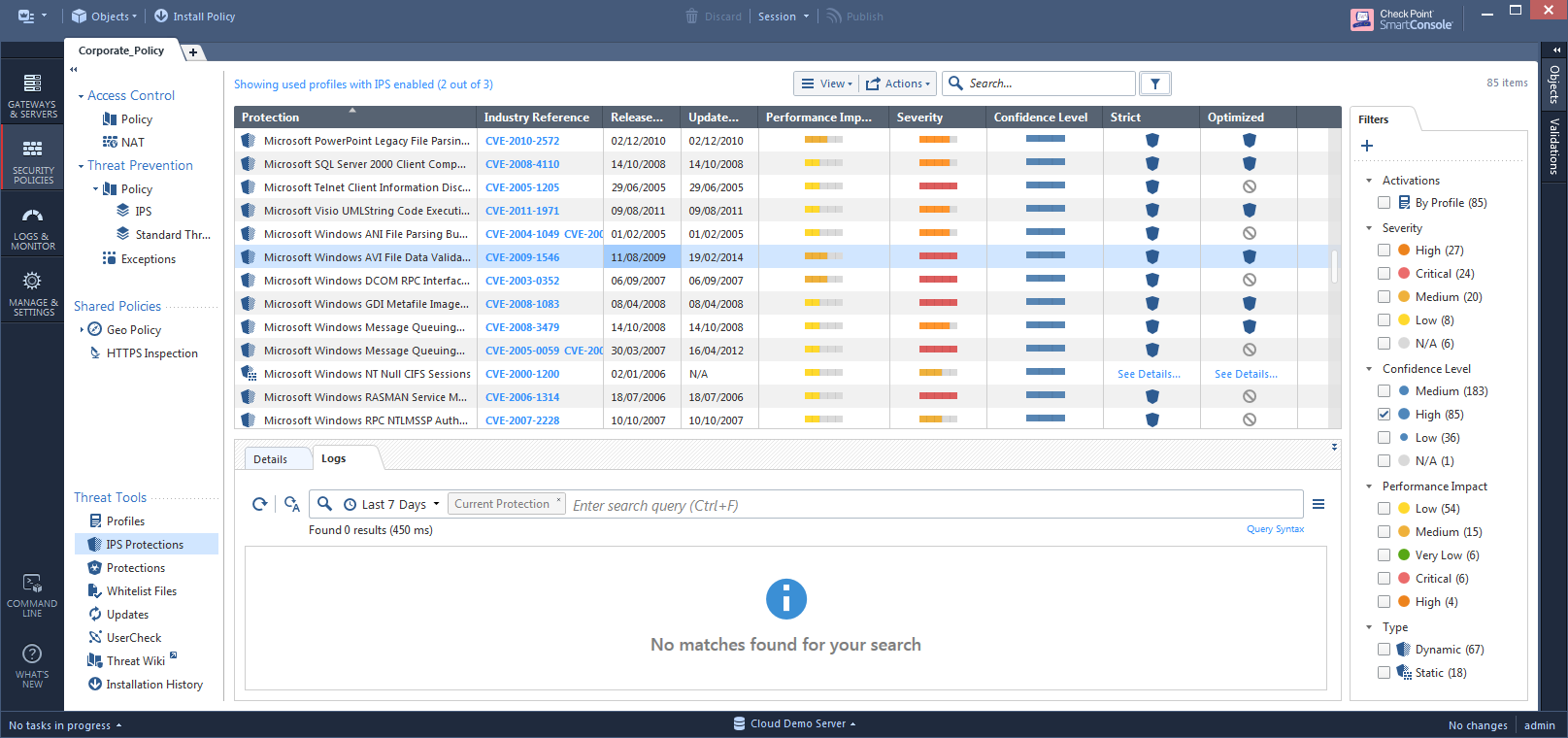
Finally, a new key feature on IPS Profiles is activation by tags. Each protection has various tags related to the OS, the exploited application, protocols and more. A user can customize his IPS profile to automatically prevent or deactivate protections by their tags. This feature works on all versions of the Gateways.
Please let us know if there are additional tags that you wish we could add to protections in order to further automate the decision making of protection actions.

Edit: Managing IPS in R80 has a new concept: Staging Protections. For more, see What are IPS Staging Protections? And how do we clear them?
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The IPS Protections view in R80 leverages the new stronger back-end. Protections load and get filtered much faster than previous versions. As the Management server is more powerful, the SmartConsole process no longer needs to load all the protections into its memory but rather uses paged results, which reduces the process size and the dependability on Windows hardware.
The view also had a user experience overhaul, making working on the protections a more intuitive work. We believe that this is important in saving time and giving more clear information to the user.
The bottom pane presents logs per protection. By observing actual traffic that was matched to the protections, the administrator can make faster decisions in changing the protection actions.

Finally, a new key feature on IPS Profiles is activation by tags. Each protection has various tags related to the OS, the exploited application, protocols and more. A user can customize his IPS profile to automatically prevent or deactivate protections by their tags. This feature works on all versions of the Gateways.
Please let us know if there are additional tags that you wish we could add to protections in order to further automate the decision making of protection actions.

Edit: Managing IPS in R80 has a new concept: Staging Protections. For more, see What are IPS Staging Protections? And how do we clear them?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could you offer advice on how to activate every IPS protections marked as 'Staging'?
Currently you can only select the staging protections on a single page because the selection resets if you scroll the page.
Ctrl + A does not work, neither does page up/down.
So no, I don't think r80 is any improvement at all regarding IPS
Best regards,
Henrik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Henrik,
Can you please elaborate on the way you usually handle your IPS protections? Are you saying that following an IPS update, you select all staging protections, override their action to Detect, and install policy? We are interested with your use case.
This is indeed a limitation of the R80 GUI application. We plan to address that in later releases.
A workaround could be writing a tool using the following R80 API commands.
Edit: This is actually a combination of the GUI and the API commands. This could be automated a little bit but here it goes:
1. Inside the IPS Protections view, filter to only show protections in staging mode. Select Actions-->Export to export them to a CSV file.
2. copy the names of these protections and create a batch API file to set all of their actions to Detect. For example, let's say we have 3 profiles - Optimized, Strict and Basic, and 2 protections currently in staging - "MyApplication Params Overflow" and "GigaCom Protocol Abuse". Their CSV will look like this:
Protection,Industry Reference,Release Date,Update Date,Performance Impact,Severity,Confidence Level,Optimized,Strict,Basic
MyApplication Params Overflow,,12-11-15,12-11-15,Medium,Medium,Medium,Inactive,Detect,Inactive,
GigaCom Protocol Abuse,,19-05-15,26-05-15,Medium,N/A,Medium,Inactive,Detect,Inactive,
modify it so that it now looks like this:
set threat-protection name "MyApplication Params Overflow" overrides.1.profile Basic overrides.1.action Detect overrides.2.profile Optimized overrides.2.action Detect overrides.3.profile Strict overrides.3.action Detect
set threat-protection name "GigaCom Protocol Abuse" overrides.1.profile Basic overrides.1.action Detect overrides.2.profile Optimized overrides.2.action Detect overrides.3.profile Strict overrides.3.action Detect
save that file.
3. Open the Command Line.
4. Open that file and run it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree, you also can no longer view logs for ALL protections that are in Staging - which is very annoying. Going through each protection to view the logs is very time consuming.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for this feedback Raj.
As you may have noticed, we retired the Follow Up flag for IPS Protections in R80 in exchange for automatic Staging and Tags.
Are you saying that you used the SmartView Tracker query for "IPS Protections in Follow Up" as a way to decide the actions for newly downloaded protections? We are planning to give better tools for handling protections in Staging Mode in the next releases so I would also like to hear whether you have other deciding factors. You can contact me privately if you prefer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tomer, I was unable to figure out how to send a private message. No problem.
Our Operations team used the SmartView Tracker query for "IPS Protections in Follow Up" to view logs and decide if the protections are relevant and Prevent or Disable as needed so they do not impact business-related traffic. This has been valuable to use in our IPS implementation process. Since follow up has been replaced by staging, if there is a way to filter in Smart Log for protections that are in "staging" that would be great, or on the IPS Protections page, have a filter to not only view protections in staging but all logs instead of just individual logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for this feedback.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
we are a Check Point partner in Austria and also do handle some customers IPS database.
As I am responsible for some of them I can double check Raj's comment. We do (or did..) use the follow-up flag to see if there were events from new protections to decide if it needs to be prevented or not.
A similar thing would be nice in R80(.10) too. Everything else is kind of a downgrade 😕
Best regards,
Manuel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I managed to select more protections than those on the current page by selecting one protection, pressing shift and then move down the list by pressing the down-arrow.
That allowed me to clear staging for more than 100 protections at a single time...
Really un-intuitive and not what I want from a "new" GUI....
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a limitation of R80. A workaround for R80 would be the command-line approach that I demonstrated above.
We plan to have a better solution for that limitation in our next releases of the GUI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's great, more than great it's a must, to have ways to mitigate the time expensive task of IPS tunning.
Every improvement on that is very welcome. I ask myself, when will Checkpoint made use of the great ammount of information and knowledge about the traffic on the network to pruppose IPS rules to the customer?
In that sense I'm thinking on the Cisco approach, analizyn logs you know a lot about the network: OS, Services, some versions of apps, etc... with a litle work you can do a passive information gathering (ie: getting some service banners) and with all that pruppose some rule activation or deactivation.
Thanks for your work!
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I can now confirm several additions to the IPS Protections page for R80.10 (currently available in EA through Check Point User Center):
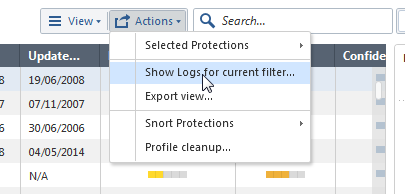
- Profile Cleanup: Supports bulk cleanup of all staging protections or all action overrides, per profile. Available from the toolbar under "Actions".
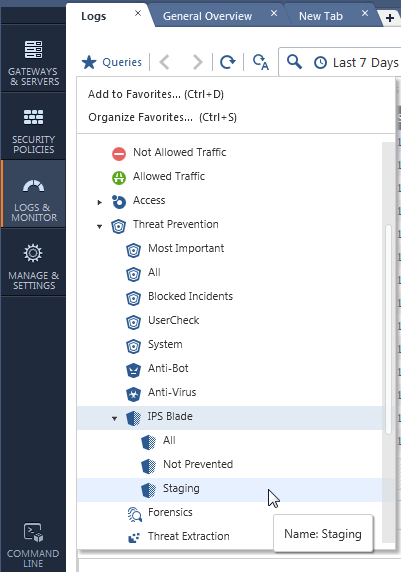
- Logs for all protections in current filter: When you filter the protections, you can select to see logs for all the given protections by the filter. Available from either the toolbar under "Actions", or from the logs bottom pane by clicking "Show logs for all protections in this view". This can be used to see logs for all protections marked as staging which, as some of you mentioned, is a gap closure from R77.30. Logs for IPS Protections in staging is also available from the SmartLog or SmartEvent queries tree.
Another closed gap from R77.30 is the integration for SNORT protections.
Your feedback is welcome.
Updated toolbar:
Updated bottom pane:
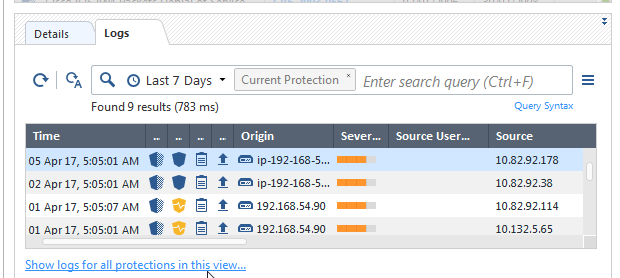
IPS-related queries from Logs & Monitor:
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 13 | |
| 8 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


