- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Disabling 'out of state' checks between certain ho...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Disabling 'out of state' checks between certain hosts
I've read that it's possible to disabled 'out of state' check between subnets and certain hosts using the use.def.X using something like the example below.
I'm ok with the version of the user.def file I should be using, but my challenge is I have 5 source ip's of which any could be used to communicate with 10 destination ip's. Not sure how to reflect that in the example below.
Any ideas ?
/* Start of INSPECT modification - sk11088 */deffunc user_accept_non_syn() { ((dst = x.x.x.x) and (src = y.y.y.y)) or ((dst = y.y.y.y) and (src = x.x.x.x)) };/* End of INSPECT modification */
21 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would rather ask myself why TCP is out of state - this is not a healthy status afaik!
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is a pain but in my experience you have to write all the possible combinations ... In your case that is 50 different tuples.
As Gunther said it might be might be better to look into why there are TCP packets out of state, usually it is asymmetric routing but I've seen before very old applications causing this issue (it seemed to be mainly legacy applications directly querying SQL servers).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agreed, that is something that is being looked into, but an example of how it might look would be useful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In my experience, whether you need to do anything about "TCP out of state" messages depends on the specific TCP flags being reported in the log entry, please see my post here:
https://community.checkpoint.com/message/9300-re-first-packet-isnt-sync?commentID=9300#comment-9300
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
While I agree with the other comments, you may be able to also do something like the following (if I remember INSPECT correctly):
deffunc user_accept_non_syn() { (dst in { a.b.c.d , e.f.g.h }, src in { i.j.k.l, m.n.o.p }) };
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Would something like this work or can you only use the 'deffunc' statement once on one line ?
(ip's changed) where 172 is the source communicating with multiple 192's ?
/* Start of INSPECT modification - sk11088 */
deffunc user_accept_non_syn() { (((dst = 192.168.1.1) and (src = 172.16.1.1)) or ((dst = 192.168.1.1) and (src = 172.16.1.1))) and (dport = 1521) };
deffunc user_accept_non_syn() { (((dst = 192.168.1.2) and (src = 172.16.1.1)) or ((dst = 192.168.1.2) and (src = 172.16.1.1))) and (dport = 1521) };
deffunc user_accept_non_syn() { (((dst = 192.168.1.3) and (src = 172.16.1.1)) or ((dst = 192.168.1.3) and (src = 172.16.1.1))) and (dport = 1521) };
deffunc user_accept_non_syn() { (((dst = 192.168.1.4) and (src = 172.16.1.1)) or ((dst = 192.168.1.4) and (src = 172.16.1.1))) and (dport = 1521) };
/* End of INSPECT modification */
#endif /* ifndef __user_def__ */
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No because you’re defining the function 4 times.
In my example, I showed you how you can define a list of source IPs and Destination IPs to compare.
You could theoretically add a port to it also.
Note the comma is treated as an AND.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, got it so one line defining both source & destination ip's and that would ignore 'out of state' for any of the ip's in the source/dest below ?
deffunc user_accept_non_syn() { (dst in { 192.168.1.2 , 192.168.1.3, 192.168.1.4, 192.168.1.5,etc... }, src in { 172.16.1.1, 172.16.1.2, 172.16.1.3, 172.16.1.4, 172.16.15 }) };
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That looks correct.
That said, my INSPECT knowledge is a little rusty ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Or:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried this initially and it didn't work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Huh... Dameon Welch-Abernathy, can you forward it to the R&D to take a look at.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are on R80.10 Management (take 154). The gateway I'm working with is a VS on R77.30
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Perhaps it is a factor, but I am not aware of this limitation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assumed it was a different check as 'out of state' checks can be turned off in global properties, but that's obviously global and not something I want to do globally.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah, you can only narrow the global setting to a particular gateway, not the pair of hosts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure those exceptions are effective on pre-R80 gateways.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
it is a little bit confusing for me.
To exclude a network from out of state' checks, is the recommended approach via user.def file or via SmartConsole exception settings? Changing the file is not visible in SmartConsole and vice versa.
sk11088 points to user.def
What is the correct approach assuming R80.40 environment?
Thanks
Best Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
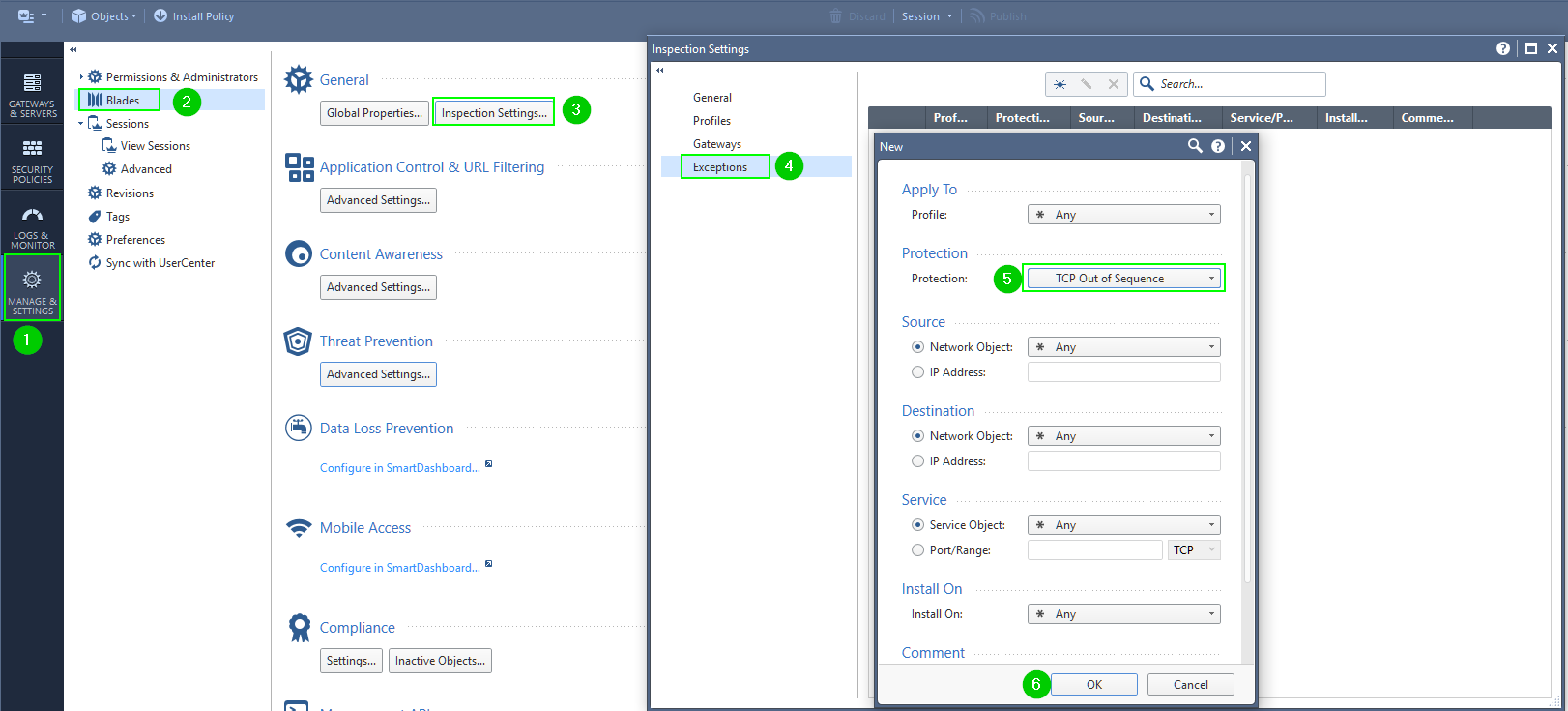
Partially disabling out of state checks is located under Global Properties...Stateful Inspection...Drop out of state TCP packets...Exceptions, but that only allows you to disable out of state checks for an entire gateway, not for individual networks. Or are you referring to somewhere else in the SmartConsole such as Inspection Settings...Exceptions?
The only way I know of to disable out of state checks for specific networks/addresses is the user.def method.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
thanks for confirmation.
So user.def is the way to go for dedicated networks.
Thanks
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
i have a nice example here:
exlclude all TCP out of State between three LAN segments ...
/* Start of INSPECT modification - sk11088 - */
troublenet1={ <10.1.1.0, 10.1.1.255> };
troublenet2={ <10.2.1.0, 10.2.1.255> };
troublenet3={ <10.3.1.0, 10.3.1.255> };
deffunc user_accept_non_syn() {\
((src in troublenet1) and (dst in troublenet2)) or \
((src in troublenet1) and (dst in troublenet3)) or \
((src in troublenet2) and (dst in troublenet1)) or \
((src in troublenet2) and (dst in troublenet3)) or \
((src in troublenet3) and (dst in troublenet1)) or \
((src in troublenet3) and (dst in troublenet2)) };
/* End of INSPECT modification */
#endif /* ifndef IPV6_FLAVOR */
#endif /* __user_def__ */
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 12 | |
| 9 | |
| 7 | |
| 6 | |
| 6 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Wed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


