- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Clarification about connection persistence and SK1...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
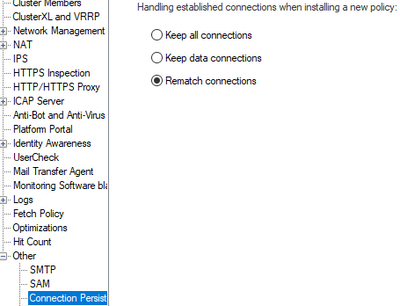
Clarification about connection persistence and SK115871
Helloes.
We have Rematch connections set in the options for Connection Persistence, on our gateway.
We figured it would remove the "additional engines" alerts in the logs, but it hasn't really made any difference.
When i read SK115871 it speaks of an additional option you can set in the firewalls, but could i get some clarification on what it actually means if it's turned off?
"Drop connection that were opened prior to policy installation and new policy can't be applied to them due to engines activated on the connection"
Would old connections be instantly dropped and unable to be renegotiated?
The bigger question would be why we still see so many alerts in the logs? it's been a while since we altered the setting for connection persistence and we figured they would ebb out.
4 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The SK article in question is related to a situation when you have advanced software blades: AC/URLf, AVI, Ani-Bot, Threat Emulation/Extraction, Content Awareness - enabled in your security policy.
Connection persistence filed is related to the classic FW security policy, where decision is simple, and the question is - what to do with the connections in progress that are no longer allowed by the new security policy. If you re-match, then connections that are now disallowed, will be dropped.
Now, let's say, you are moving from basic filtering to AC & Content awareness. Both SBs require streaming. For ongoing connections that you allow through connection persistence feature, streaming will fail, hence the log alert.
The logic here is simple. Since building the full stream for ongoing connections is impossible, you can either accept them through the new policy (and alert about it), or drop, with up_rematch_accept_possible_action parameter mentioned in SK.
If you decide to drop, you are risking to break legitimate connections where stream is unavailable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are using AppControl/URL Filtering, right? AppControl works by scanning the first bytes of each new connection (SNI, HTTP-Header, etc) to detect the Application. Once you apply a new rulebase AppControl has to match old established connections to the new rules, but since the connection is already established its impossible to scan for certain markers e.g. the SNI Field. This is where the kernel parameter value "int up_rematch_accept_possible_action" comes in.
The SK says:
... "New" policy installation will trigger the rule base execution on the next packet, that will now require ‘Application Control' engine inspection on this connection in order to reach a final decision. This cannot be done for connections that are already open. The final action will be determined by the value of kernel parameter "up_rematch_accept_possible_action". Default value is "1", therefore the connection will be accepted."...
> Would old connections be instantly dropped and unable to be renegotiated?
Old connections would be dropped if you set int up_rematch_accept_possible_action to 0 and the firewall is unable to match them to a rule. I don't know what you mean by "renegotiated", but new connections should work provided they are allowed by the new rulebase.
> The bigger question would be why we still see so many alerts in the logs? it's been a while since we altered the setting for connection persistence and we figured they would ebb out.
You will see this alert for some time after a new policy has been installed because the gateway is trying to rematch old connections to a new rulebase.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ok, then I understand better what it does.
Yes, we have AppControl/URLF. We actually have 2 near-identical rules, one where we would like to identify certain things with AppControl/URLF and one where we let through the rest with any as service.
with renegotiated I meant that the application would re-establish the session if it died.
we've had this setting for at least 3 months and still see this error, so i don't feel like there should be any old connections left. But we can think about changing the fw parameter then.
oddly enough this alert shows up a lot for normal microsoft-ds traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"Old connections" here means those which were crossing through FW before the last policy was installed.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 13 | |
| 13 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter