- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Changing IP on management server - How long do I h...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
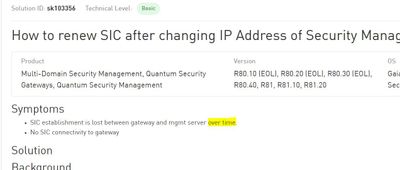
Changing IP on management server - How long do I have before I have to redo SIC
Hey everyone, We need to change the IP on our management server, and had initially been told by TAC that reestablishing SIC wouldn't be required, since the certificate was based on DNS name, which wasn't changing. Now I'm reading that SIC does need to be reestablished, since the management server IP is stored in the $CPDIR/registry/HKLM_registry.data file. BUT...the documentation also says this;
Symptoms
- SIC establishment is lost between gateway and mgmt server over time.
- No SIC connectivity to gateway
Since it says "over time", does anyone know what the trigger is that will cause SIC to start failing? Trying to plan this out, want to make sure I know exactly what's going to happen, and when.
Thx,
dp
16 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Where precisely are you seeing this "over time" statement?
You should be able to re-establish SIC with the relevant gateways after changing the IP on the management by performing an Install Policy action to all gateways.
This will update the management IP on all the relevant gateways and re-establish connectivity.
Remember that the management is also the Internal Certificate Authority.
Part of that functionality is gateways checking on the validity of certificates issued by the ICA.
If the IP is different, then the Certificate Revocation List is not available.
At least for VPN, this will cause VPNs to start failing after 24 hours or so.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have personally never seen this happen, not that it means it doesn't happen. I just always make sure to do an install database before I push the policy. It was my understanding that the Masters was all it was checking, and that is object-based. @PhoneBoy isn't the CRL pulled from the VPN certificate and not the SIC certificate?
Aka, Chillyjim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
They state this in this article, https://support.checkpoint.com/results/sk/sk103356.
So are we all in agreement that SIC will automatically happen after I change the management IP, install database, then push a policy? Wondering if that file on the gateway automatically updates itself with the new IP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats my experience, BUT, that does not always guarantee SIC wont need to be reset.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect the "over time" might be talking about automatic renewal of the SIC certificates. Eventually, the cert will get close to expiring and will try to renew itself. Not sure which method it uses to get the management's IP to try to renew the cert, but if it doesn't try the new IP, the SIC cert will eventually expire. Doesn't disrupt traffic, but it does prevent policy installation and other things which depend on SIC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are referring to below:
https://support.checkpoint.com/results/sk/sk103356
In my experience, last time I did this, worked fine, no SIC reset, but then 3 times before that, it was needed...so, I have no clue in the world why its inconsistent : - )
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did just have a look on one of my VPN gateways, and that HKLM_registry.data file shows that it was updated 20 mins ago, even though no policy was pushed to it. Wonder if that file automatically updates on a certain interval, as the gateway is communicating with the management server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats most likely true...I will let someone else confirm, but it would make logical sense.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just checked my lab and though I never modified this file, shows today's date, so Im 100% sure its all automatic. Never knew that was the case, so thank you for bringing that point up 👍
Andy
[Expert@quantum-firewall:0]# cd /opt/CPshrd-R81.20/registry/
[Expert@quantum-firewall:0]# stat HKLM_registry.data
File: 'HKLM_registry.data'
Size: 143613 Blocks: 288 IO Block: 4096 regular file
Device: fc01h/64513d Inode: 35062378 Links: 1
Access: (0660/-rw-rw----) Uid: ( 0/ admin) Gid: ( 0/ root)
Access: 2023-07-20 10:06:59.652972485 -0400
Modify: 2023-07-20 10:06:59.482972476 -0400
Change: 2023-07-20 10:06:59.503972477 -0400
Birth: -
[Expert@quantum-firewall:0]#
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I verified 100% based on test on 4 different VMs and 4 different CP versions *R80.30, R80.40, R81.10 and R81.20) that HKLm_registry.data file gets "refreshed" every 60 seconds...thats what it shows when I ran watch -d stat command on the file
Not sure if TAC would have any other official answer, but thats result I get.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you try to cut the connection between gateway and management? Wondering if that file is refreshed only in case there is communication between GW and management.
Do you also see if there is some difference in regards to content of the file ? Is the content always the same, or some timestamps are updated within the file itself ? You can use "diff" command to compare the file before refresh (make a copy) and after refresh.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Content is exactly the same every time I check it.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hmm...what happens when you change the IP on your management server? Hehehe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did that test today in my lab and all worked fine, no need to even do SIC reset. File content was the same.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That file contains the IP of the management server though, so I assume that this entry at least changed?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes...I changed it back since and its updated accordingly
Andy
[Expert@quantum-firewall:0]# grep -i 172.16.10.203 /opt/CPshrd-R81.20/registry/HKLM_registry.data
:ICAip (172.16.10.203)
[Expert@quantum-firewall:0]#
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 23 | |
| 15 | |
| 13 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter