- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: CPLogToSyslog Utility Now GA
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CPLogToSyslog Utility Now GA
Check Point has recently made available publicly a tool that allows you to export Check Point logs from the management to a syslog server.
Refer to the following SK: How to export Check Point logs to a Syslog server using CPLogToSyslog
42 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Worth noting this is not for R80.10 just yet, but it is planned for the near term.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi team,
on sk117549 supprt explain how to send syslog to microsoft OMS. Those syslog messages need to be in BSD format. My customer have many gateways here and it dont want to specify for each gateway to send logs both to smartcenter and to syslog proxy on my lan.
i tried to use cplogtosyslog utility sk115392 but the logs are in the wrong format.
I am using a package for hotfix 205 i got from you. The issue is i can't specify BSD format on the CPLOGTOSYSLOG config.
thanks in advance
aner.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't believe cplogtosyslog supports this.
However, if you are using R77.30 management, you can configure gateways to send BSD Formatted syslog directly using the following SK: How to Configure R77.30 Security Gateway on Gaia OS to send Firewall logs to an external Syslog serv...
Note that there are plans to improve syslog support in general during the next several months.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The R80.10 version of CPLogToSyslog tool is now available in the SK: How to export Check Point logs to a Syslog server using CPLogToSyslog
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dameon, I have tried implementing it in a lab, using utility version provided for R80, but no dice. Can you confirm that it is working and, if at all possible, provide a sample of annotated config file?
In looking for solution to this issue, I have stumbled on suggestions located at using:
fw log -f -t -n -l 2> /dev/null | awk 'NF' | sed '/^$/d' | logger -p local4.info -t CP_FireWall &
which does seem to work, but I would like to understand how the logs on management server will be rotated and if the space allocated to them could be limited and reused.
Thank you,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have not heard the tool not working for anyone.
The SK includes a sample annotated configuration file as well as installation and troubleshooting steps.
If you're not understanding something specific in the commands or the output of those commands, please post a more specific question.
For R80 in particular, there are two versions--make sure you're using the right one for your patch level.
CPLogToSyslog is basically a LEA client that is reading from the Check Point logs similar to how third parties do it.
Those logs are then sent via syslog to the destination you've configured.
What you've presented there as a possible workaround has been well known for some time--I had it on my site back in the day.
As I recall, it's not particularly reliable.
Management of the storage of logs on the log/manager is controlled by settings on the relevant object in SmartDashboard.
You can configure at what point logs are deleted there.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
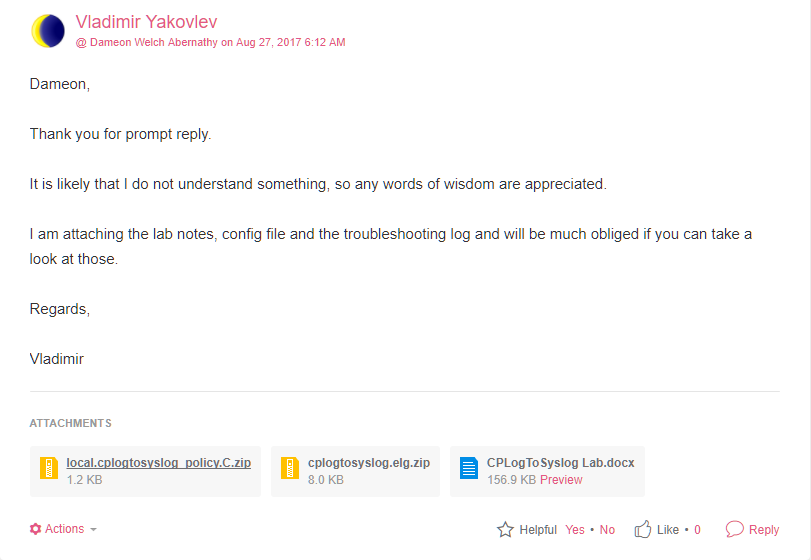
Dameon,
Thank you for prompt reply.
It is likely that I do not understand something, so any words of wisdom are appreciated.
I am attaching the lab notes, config file and the troubleshooting log and will be much obliged if you can take a look at those.
Regards,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The attachments you sent (assuming via email) did not come across.
You will need to come to the community website to attach those.
You may also wish to open a support ticket with TAC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Weird, I have uploaded those from the community, can see them in the post above and was able to download and open all three files:
As to TAC, they are not keen on supporting lab environments, hence looking for suggestions in community.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Issue is on my end ![]()
Apparently they don't show in the "inbox" view on the community, which is...problematic.
Looking at the logs you provided, it looks like CPLogToSyslog is sending the logs over TCP
Your syslog server is listening on UDP.
Looking at your configuration file, it seems you've configured it for UDP.
Clearly this setting is getting ignored.
You have two options:
1. Open a TAC case to investigate (it's a bug, whether lab or not is irrelevant)
2. Configure your syslog server to accept connections over TCP
Unrelated question: if this is lab, why are you using R80 instead of R80.10?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think there are more issues with communities: I have replied to your last post via email, but it did not show-up in a thread (about 4 hours ago).
TAC is not keen on investigating lab reports of observed issues. I have forwarded my test results to four people at CP, but did not hear from them in a while.
I can use TCP in my lab, but am working on replicating client's environment, hence R80.
Thank you for help with the sanity check!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you forward the email you tried to send to checkmates AT checkpoint DOT com?
I’ll have someone take a look at it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apologies, false alarm: I've found it in my drafts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can confirm that R80.10 works in the lab.
Now I need to do something intelligent with the entries in SPLUNK 😉
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm trying to get this working, but the only logs I'm getting are anti-malware events, no drops nor accepts.
Can you share your config file ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kristof,
I've also made in my lab some tests with management version R80 and gateway version R77.30 as in your lab, and also with the latest version R80.10 for the management and gateway.
In both cases the logs are exported to my syslog server (in my case as syslog server I'm using the Extreme Management Server for made a distributed IPS system because Extreme Networks has developed a module for this purpose), but you first need to force Check Point to export the logs via UDP instead TCP (by default use TCP, so follow the Check Point solution sk109016 for use UDP instead that I attach to) and then define the filter rules for the log events you want to export to the external syslog server in the local.cplogtosyslog_policy.C file.
The log structure is in some parts changed between version R80 and version R80.10 of Check Point management (for example in R80 the action was no a field mapped, instead it is in R80.10 version).
I attach my local.cplogtosyslog_policy.C file that I use in my lab for version R80.10 and the file that I use in version R80 as your lab is (remove the _r80.10 or _r80 from the file name if you want to use these files and change the ip address as in your environment).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does anyone know if this tool works on a log server running NGSE?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I recommend contacting the TAC to see if they can provide a version of this for NGSE: Contact Support | Check Point Software
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
BTW, if you need the ability to differentiate gateways by name in the forwarded logs, (i.e. if you are shipping logs to external SIEM provider to be parsed):
Below are the steps to have the syslog contain the origin_sic_name field.
Perform these steps on the Log server that has CPLogToSyslog installed:
1. Stop services on the Log Server.
[Expert@HostName]# cpstop
- Backup and modify $FWDIR/conf/log_fields.C
[Expert@HostName]# cp -pv $FWDIR/conf/log_fields.C
$FWDIR/conf/log_fields.C_ORIGINAL
[Expert@HostName]# vi $FWDIR/conf/log_fields.C
- Search for "origin_sic_name" and under ":display_mode" there will be a
field, ":application_name (FWLog)". Change from:
: (
:AdminInfo (
:chkpf_uid ("{5DF46778-79F6-487B-AF90-8CE40333E117}")
:ClassName (application_display_mode_object)
)
:application_display_mode (none)
:application_name (FWLog)
)
TO:
: (
:AdminInfo (
:chkpf_uid ("{5DF46778-79F6-487B-AF90-8CE40333E117}")
:ClassName (application_display_mode_object)
)
:application_display_mode (own_column)
:application_name (FWLog)
)
- Start services.
[Expert@HostName]# cpstart
The logs will now contain the origin_sic_name field:
Nov 9 2017 14:39:50
Nov 9 2017 19:39:50 GMT
Thu Nov 9 14:39:50 Log host CPLogToSyslog: 0 16386 encrypt 52.184.158.74 >eth1 LogId: <max_null>; ContextNum: <max_null>; OriginSicName: <max_null>; log_sequence_num: 0; is_first_for_luuid: 131072; inzone: Internal; outzone: External; rule: 90; rule_uid: {AE182161-16C0-4367-A732-B036B35935E9}; rule_name: Internet access; service_id: domain-udp; src: 10.aaa.aaa.aaa; dst: 10.bbb.bbb.bbb; proto: 17; scheme: IKE; methods: ESP: AES-128 + SHA1; peer gateway: 62.aaa.bbb.ccc; community: Onprem-AzureCloud; fw_subproduct: VPN-1; vpn_feature_name: VPN; origin_sic_name: CN=gatewayname,O=managementserver.domain.com.d4w394; aba_customer: SMC User; date: 9Nov2017; hour: 14:29:57; type: log; Interface: < eth1; ProductName: VPN-1 & FireWall-1; svc: 53; sport_svc: 9679;
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
just adding to the general discussion, we tested the CPLogToSyslog function over TCP and UDP.
TCP seems to die after some time whereas UDP seems fine. Its possible that our parser on our SIEM was slowing things down and causing backlog that ultimately kills CPLogToSyslog. Still looking into this issue
Shoutout to Dameon Welch Abernathy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TCP is stateful, UDP is stateless.
Curious if you're losing logs on your SIEM as a result.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect we were because the parser was inefficient. I'm guessing that was causing CPLogToSyslog to die when on TCP. We'll retry TCP and update everyone here
Also in case anyone is wondering there is a CPLogToSyslog HF equivalent for R77.30 HFA 286.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm having issues in getting my utility to run over UDP, as it's using TCP. I've refered to sk109016 but we're still seeing it running over TCP then our utility stops.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you rebooted your management server after implementing changes described in the sk?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have yes, rebooted it last night and checking the connection using netstat it's still using TCP. I thought that sk doesn't apply to R80.10? It doesn't say so.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please paste the output of "netstat -anp | grep -E "PID|CPLogToSyslog" in reply.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
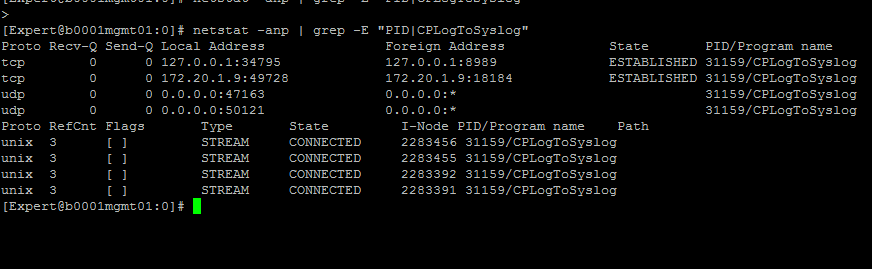
Here you go.
Tom
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
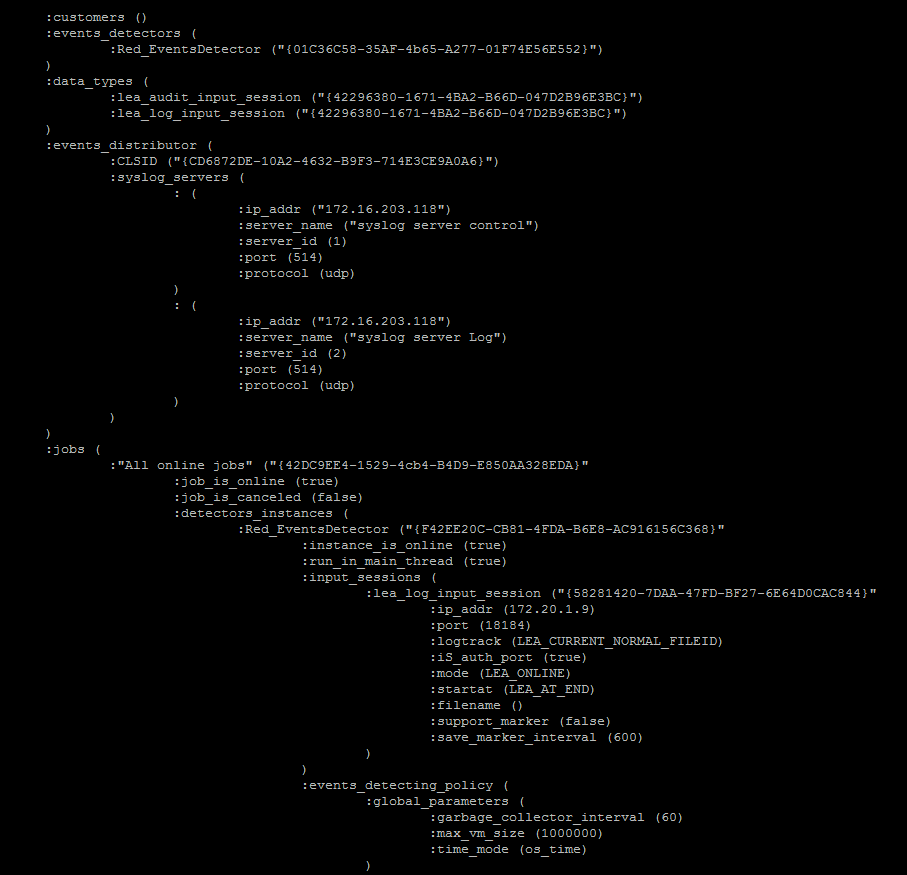
please let me know what is the host 172.20.1.9.
Additionally, please paste the pertinent section of the $FWDIR/state/SEAM/local.cplogtosyslog_policy.C file.
I am not sure if you've had a chance to read this document that I have posted few months ago:
https://community.checkpoint.com/docs/DOC-2205-cplog-to-syslog-for-r80-managed-environments
But it may make sense to go over it to confirm that all is configured appropriately.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
172.20.1.9 is the IP of our Management server. And is this the right part you want out of the configuration file?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 16 | |
| 14 | |
| 11 | |
| 8 | |
| 6 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


