- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Register HereCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
MVP 2026: Submissions
Are Now Open!
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Best practices for inline layers
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Best practices for inline layers
Hi, we're running R80.10 and would like to start cleaning up our policy that has become cluttered and outdated and inline layers look like they could assist in keeping things organized as we clean up the old clutter but I can't find a lot of info about best practices for them.
Should you try to limit how many inline layers/rules you use in a policy?
Is there a preferred method for crafting the parent rule? Should it be vague and then get more particular with each inline layer rule? Or should the parent rules be crafted very specifically as well?
I've read a few of the threads here on CheckMates and any relevant SK's but was just wondering if there was any specific guidance on the best way to utilize inline layers.
16 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Eric,
If I were you, I would be reading up on the following:
- Best Practices for Access Control Rules
- Unified Rule Base Cases
Both sections can be found in the following link:
I hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I wouldn’t nest inline layers more than 3 or 4 deep. Top-Level rules should be fairly generic but there are use cases when a specific rule at the top might be useful.
Also think "reusable policies" with layers. For example, you might create a layer specific to Internet access that you want to apply in multiple policies. That would be a layer you make shared so it can easily be reused.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Today we have hit the limit of 251 layers in a policy. Using more than 251 layers in the policy, we get a policy installation error with error code 1-200008.
Article sk154435 (scenario 1b) mentions the 251 limit.
For our customer this means a redesign of the whole security policy. So be aware of this limit.
Regards,
Martijn.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would love to learn more about this policy design method. Is every rule using a layer?
I've never seen a security policy yet with more than just a couple layers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I also have a customer that has loads of inline layers.
They have external and internal DMZ's, for each direction (in and out) the network itself is on a rule, and the rule has a layer to be more specific with hosts, also on the external DMZ out layer has a shared sub layer that allows all external DMZ servers to go out to a specific service.
With about 20 DMZ sets times 8 layers per DMZ set = 160 and then the additional shared layer (is this counted per occurrence in this case?)
They have external and internal DMZ's, for each direction (in and out) the network itself is on a rule, and the rule has a layer to be more specific with hosts, also on the external DMZ out layer has a shared sub layer that allows all external DMZ servers to go out to a specific service.
With about 20 DMZ sets times 8 layers per DMZ set = 160 and then the additional shared layer (is this counted per occurrence in this case?)
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Customer creates security rules between VLAN's with inline layers. In these inline layers the rules are specified for traffic between servers in these VLAN's. All inline layers end with a 'Any' 'Any' 'Drop' rule.
With this method all unwanted traffic is dropped by a 'Drop' rule in one of the inline layers without going through the whole policy before traffic is dropped. This means the clean up rule at the end is almost not used and when they see the clean up rule being hit, they know they made an error in the policy / layers.
So yes, all rules are using inline layers. With the exception of clean up, stealth and some management rules. With almost 260 rules, we hit the 251 limit.
Support mentioned the following limites regarding policies.
Limitation for NAT rules in the policy - 16384.
Limmitaion of the layers in the policy - 251.
Limmitaion of the rules in the policy - No limit.
Regards,
Martijn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh BTW this is indeed exactly the idea, end of the layer is a drop, either implicit or explicit, depending on the layer properties.
However do keep in mind as well that once the flow is into a layer that is also where it ends, so when you put an allow rule at the end it will allow ALL ELSE that fits the parent rule.
However do keep in mind as well that once the flow is into a layer that is also where it ends, so when you put an allow rule at the end it will allow ALL ELSE that fits the parent rule.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Martijn Sounds very complex and not really how the layers are meant to be used.
The main purpose is to make policies more efficient and manageable.
Below are my guidelines for access control policy layers.
- Inline layers are sub-policies
- Use security zones as "parent" rules
- Use access roles to allow user access when possible
- Add a clean-up rule after each layer (drop or accept depending on the purpose)
- Limit the number of rules per layer to under a hundred. If you have a feeling that you should have hundreds of rules per layer, consider adding more layers instead of one very big one.
- Make your layers shareable if you have many policies that could utilize them.
- If you have any pre-R80.10 gateways only ordered layers are supported.
- Implement segregation of duties with layers if this is necessary in your organization.
- You can give layers specific admin privileges (specific admins can be allowed access to manage only certain layer).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Lari_Luoma Thanks for these tips.
Do you know if the limit of 251 is per Access Policy or per Unified Policy. Or is the type of policy not relevant?
Regards,
Martijn.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you know howto count the inline layers used in the policy?
Thanks,
Peter
Thanks,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Found it!
With this you can count the Inline Layers:
https://wiki.linuxnet.ch/bin/view/Vendors/Check%20Point/Operation/Check%20Point%20Useful%20CLI%20Com...
With this you can count the Inline Layers:
https://wiki.linuxnet.ch/bin/view/Vendors/Check%20Point/Operation/Check%20Point%20Useful%20CLI%20Com...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Peter_Baumann FYI, the link is dead
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, I moved to a new cms, the link is now here:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just an FYI if you have it, the Compliance Blade last I checked sadly doesn't evaluate in-line rules. A good example if you App/URL policy is an in-line rule the compliance blade will show 'Poor' for blocking high risk categories even if you are blocking them. Not sure if this is even addressed in R80.30. Also other policy auditing tools such as Nipper Studio don't evaluate or even list the child rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
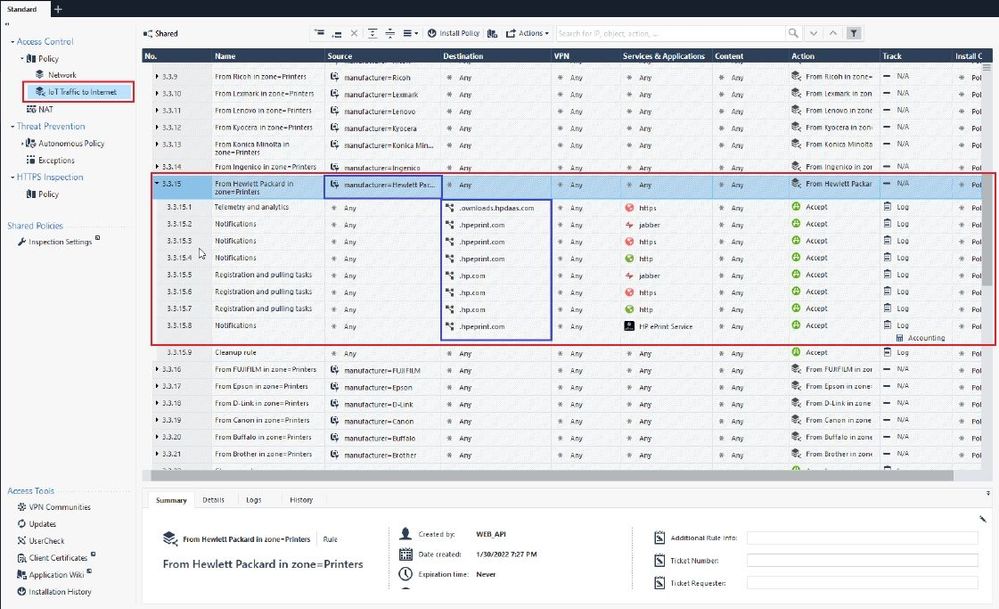
In this topic there have been a few mentions of the limit of 251 inline layers (sk154435).
The new IoT protect functionality will also add many layers, according to what I've seen in a demo (see screenshot below).
What will the impact be for the 251 limit? Will this limit be removed? Will these rules count against that limit?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As I recall, the 251 layer limit was in early R80.x releases.
Not sure if we still have that limit in current versions.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 15 | |
| 9 | |
| 6 | |
| 5 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter