I took a closer look at Check Point's Compliance Blade.
It's quite an interesting tool aiming to ensure various regulatory and compliance checks.
However, while the concept is great in theory, there's definitely room for improvement in terms of product maturity and transparency. For example, it doesn’t provide enough insight into how certain checks are performed, it doesn’t guide the user on remediation steps, it lacks automatic refreshes on scores, and it just detects and alerts compliance violations instead of a prevention-first approach. Essentially, it’s a promising tool that still needs some polish to meet real-world expectations.
Let's start our deep dive using a real world scenario:
Scenario: CISO wants to know the CIS benchmark score of all Check Point Appliances that are securing the company's network. Specifically it should be verified that a correctly configured firewall stealth rule is in place and actively drops all unwanted access to the Check Point systems and also protects itself from getting deleted or deactivated.
Network Topology: Company LAN gets segmented and protected by a Check Point Security Gateway Appliance with a dedicated Smart-1 Management Appliance, that is directly connected the gateways' management port. Company's external network perimeter gets protected by another Check Point Firewall Security Gateway.

Compliance Blade details:
Training
CIS Benchmark details:
- Latest benchmark version: 1.1.0
- Checklist consists of three parts:
CISO expectations:
| Expectations |
Result |
| CIS benchmark score per appliance |
? |
| Support for all Check Point appliance types |
? |
| Numbering of checks matches CIS summary table: 1.1 - 3.20 |
? |
| Execution of benchmark checks as technically described by CIS |
? |
| Documentation on the function of preconfigured test elements |
? |
| Cloning and customisation of preconfigured test elements |
? |
| Intuitive creation of custom test elements |
? |
| Easy creation of custom regulatory standards |
? |
| Prevention-first approach |
? |
| Provides clear steps for alert remediation |
? |
ATRG findings:
- "Compliance Blade currently only supports regular Gateways and Clusters"
- Result: No benchmark check for our Smart-1 Security Management.
- "Each Security Best Practice is assigned to one or more regulatory requirements"
- Result: No regulatory-specific checks, Check Point assigns their own Best Practices as Test Elements (TE) to their vendor-specific estimation of the checks of the regulatory standards.
- Compliance checks are neither real-time nor proactive as they always require a reactive mini-scan or full-scan. This typically takes place after changes have already been published.
- Compliance Blade doesn't provide a specific help file.
- Compliance Blade may skip inspection of Inline Layers when it doesn't like the parent rule definition.
Positive findings from this review:
- Regular gateways includes Maestro and ElasticXL
- Compliance Blade supports Managements in standalone deployments
- Enabling the blade is just a simple click on a checkbox at the Management object
- Receiving an alert notification after publishing changes that lead to compliance score degradation is really helpful and allows revisits of the last changes
- Policy installation is not required to make updates to the compliance blade effective. Publishing changes is enough.
Datasheet promises:
| Promises |
Result |
| 300+ Check Point Security Best Practices |
? |
| Monitor changes in real-time |
? |
| Translate regulatory requirements into actionable steps |
? |
| Increase Security |
? |
| Avoid Human Error |
? |
| Comply with regulations |
? |
| Clear requirements and regulations layed out |
? |
| Fine-tuning of custom best practices |
? |
Datasheet findings:
- Gaia OS Best Practices are only available for security gateways
- What about security managements, event managements, etc.?
Relevant files on the Security Management:
- $FWDIR/bin/interpreter
- $FWDIR/log/grc_interpreter.elg
- $FWDIR/conf/grc*
- $FWDIR/cpm-server/grc.jar
- $FWDIR/cpm-server/mgmt_ compliance.jar
Compliance scan procedure:
- interpreter
- verifies compliance blade licenses
- checks management database for grc test elements
- utilizes psql_client to retrieve the Main IP of each connected CP security gateway
- utilizes cprid_util to retrieve the "show configuration" data from all CP security gateways
- runs custom user scripts on the security gateways
- performs cleanup routines
- updates the scan results for SmartConsole Views and Reports
Drill down on CIS check 3.1 for Firewall Stealth Rule:


Note: As Check Point supports distributed firewall environments, i.e. firewall managements run on a dedicated host, the firewall stealth rule also has to include the firewall management host > sk103369.
CIS definition of a proper firewall stealth rule:
| Source |
Destination |
Service |
VPN |
Action |
| Any |
Gateway + Management |
Any |
Any |
Drop |
Firewall Stealth Rule definitions
There are various ways to configure a proper stealth rule, depending on the requirements of the security infrastructure.
Security policies with multiple installation targets may want to configure multiple firewall stealth rules for each target, others may use an object group of gateways (and managements), and others may use DAIP gateways, SMB gateways, inline layer policies and many other different settings that need to be considered and properly handled by an automated compliance verification engine to avoid false positives. Additionally there should be a high level of transparency in regard to how a score was achieved, i.e. how the check routine operated in detail and how remediation steps, alternative best practice and recommended approaches would look like.
Real world test
Ordered layer #1 - Standard

- Compliance blade

- Result: Success, the 'FW Stealth' rule was found to be compliant.
- Finding: Compliance blade properly detects a firewall stealth rule, when it's configured according ti Check Point's pre-configured best practice.
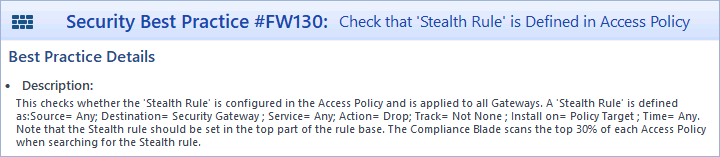
Ordered layer #2 - Multiple installation targets

- Compliance blade

- Result: Success, the existing 'FW Stealth' is only found to be compliant, when all installation targets are added to the destination field.
- Finding: Compliance blade handles this situation perfectly. This compliance check even works, when there are dedicated 'FW Stealth' rules for each installation target. Good job, Check Point!
Ordered layer #2 - No log

- Compliance blade

- Result: Fail, the existing 'FW Stealth' rule wasn't found.
- Finding: Compliance blade requires, that the 'FW Stealth' rule has an action that is not 'None'. This is not defined by CIS's stealth rule definition.
Ordered layer #3 - Missing Management

- Compliance blade

- Result: Fail, the existing 'FW Stealth' rule is missing the Management object and is therefore not a complete firewall stealth rule.
- Finding: Compliance blade doesn't verify, that the 'FW Stealth' rule includes both, the firewall gateway AND firewall management.
Inline layer
- Compliance blade

- Result: Double fail, the 'FW Stealth' rule #2.3 wasn't identified as stealth rule and the final Cleanup rule #18 got incorrectly counted as stealth rule, that is A - not part of the first 30% of the rule base and B - has 'Any' in it's Destination field, which disqualifies it as firewall stealth rule.
- Finding: Compliance blade is not capable to handle inline layers yet.
DAIP gateways
- Compliance blade

- Result: Fail, the 'FW Stealth' rule #4 wasn't identified.
- Finding: Compliance blade is not capable to handling DAIP gateways yet. sk167473 doesn't mention if Compliance blade supports DAIP gateways.
Group of firewall gateway and management objects
- Compliance blade

- Result: Fail, the 'FW Stealth' rule #4 wasn't identified.
- Finding: Compliance blade is not capable to handling object groups yet.
Compliance score degradation

- Findings: Compliance blade shows an alert if the score of a compliance check drops.
Not real-time, as the change needs to be published first. Datasheet promised real-time alerts.
Anyhow, the alert is still helpful!
Final conclusion
Compliance blade, formerly easy2comply, was officially introduced in R80.x versions, offering:
It is now an integrated, scalable, and automated solution for enterprise customers, while it requires a friendly push to maturity as it doesn't support a list of standard features yet (grouped objects, inline layers, etc.), as outlined in this audit. Currently, it should only be used with caution and verification, as it is also not free of some inconsistencies. Example:

Customers are currently quite limited in their choice of available customization options. Compliance blade currently only supports custom firewall access control and Gaia OS best practices. While Gaia OS best practices can be highly fine-tuned via shell scripts, the access control policy can neither be filtered by nested queries nor advanced conditional checks. It's currently just a simple rule filter with some standard options for negation, tolerance levels, string settings etc.

Customers looking for more flexibility and compliance verification before firewall changes are published may want to check out Check Point SmartTasks, which (unfortunately) are not available for Smart-1 Cloud customers yet.
CISO expectations fulfilled:
| Expectations |
Result |
| CIS benchmark score per appliance |
No |
| Support for all Check Point appliance types |
No |
| Numbering of checks matches CIS summary table: 1.1 - 3.20 |
No |
| Execution of benchmark checks as technically described by CIS |
No |
| Documentation on the function of preconfigured test elements |
No |
| Cloning and customisation of preconfigured test elements |
No |
| Intuitive creation of custom test elements |
Partially |
| Easy creation of custom regulatory standards |
No |
| Prevention-first approach |
No |
| Provides clear steps for alert remediation |
No |
Datasheet promises fulfilled:
| Promises |
Result |
| 300+ Check Point Security Best Practices |
Yes |
| Monitor changes in real-time |
Partially |
| Translate regulatory requirements into actionable steps |
Partially |
| Increase Security |
Yes |
| Avoid Human Error |
Partially |
| Comply with regulations |
Partially |
| Clear requirements and regulations layed out |
Partially |
| Fine-tuning of custom best practices |
Partially |
@erankov , @RobertoQ , @Corinne_Vakulen , @Chris_Atkinson




















