- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Maestro Masters
Round Table session with Maestro experts
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Maestro Masters
- :
- monitoring Maestro
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
monitoring Maestro
Hello CheckMates,
I'm looking for a solution to monitor the state of the individual gateways (not the MHOs).
Last week one of the gateways crashed and was not was available. If you login to a MHO or the SG no statement shown about the failing appliance. Only if you did a mouse over in the orchestrator-view you could see a small hint for lost connectivity with these appliance.
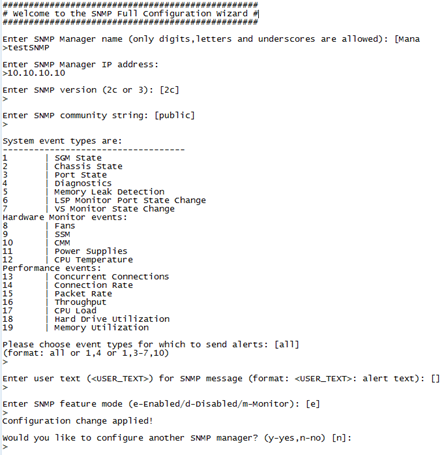
Best way would be to monitor the state via SNMP from external monitoring system, but how can I achieve this ?
How do you monitor your Maestro environments?
Wolfgang
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Install Zabbix and import one of the many available CPFW templates and go from there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1.) asg monitor
2.) asg alert
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks for your answer.
"asg monitor" needs ssh into the environment to look what happens.
"asg alert", will be fine but is it possible to monitor these states, those for they are alert sending will be configured ?
Maybee with SNMP-Monitoring Tools like CheckMK, PRTG, Nagios, Zabbix etc.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Wolfgang,
I personally use Indeni, which makes ssh connection to all managed devices and runs various commands to ascertain the state and health of the firewall. I would recommend it over snmp based tools, simply for its flexibility and as it uses ssh, you can make use of any Check Point or linux os command, rather than trying to work out which OID is useful..... I have no affiliation to Indeni, i am just a user of the product
I personally use Indeni, which makes ssh connection to all managed devices and runs various commands to ascertain the state and health of the firewall. I would recommend it over snmp based tools, simply for its flexibility and as it uses ssh, you can make use of any Check Point or linux os command, rather than trying to work out which OID is useful..... I have no affiliation to Indeni, i am just a user of the product
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For awareness R80.20SP JHF T309 provides some monitoring enhancements.
See sk155832 for details.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Wolfgang,
same problem here.
Monitoring the SMO is ok, when all traffic is active on SMO side. (I don't want to say it is good as sometimes there are diffent states on single sgms)
I want to run VSX in VSLS mode on maestro with both sites active.
Implementing monitoring in the existing snmp monitoring would be the easiest.
So I am looking forward the outcome of this threat 😉
Regards
Sven
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In case the below is helpful to some, appreciate that it may not be detailed enough for everyone's taste however.
# snmpwalk -v 2c <snip> .1.3.6.1.4.1.2620.1.48.28.5.1
…
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.2.1.0 = STRING: "1_01"
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.2.2.0 = STRING: "1_02"
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.2.3.0 = STRING: "1_03"
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.2.4.0 = STRING: "1_04"
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.2.5.0 = STRING: "1_05"
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.2.6.0 = STRING: "1_06"
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.2.7.0 = STRING: "1_07"
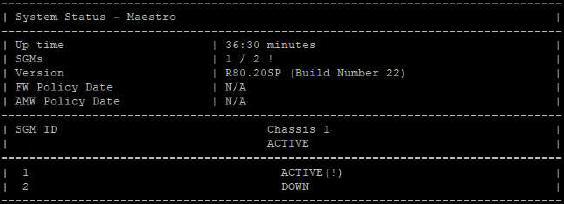
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.3.1.0 = STRING: "ACTIVE"
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.3.2.0 = STRING: "ACTIVE"
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.3.3.0 = STRING: "DOWN"
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.3.4.0 = STRING: "ACTIVE"
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.3.5.0 = STRING: "DOWN"
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.3.6.0 = STRING: "ACTIVE"
SNMPv2-SMI::enterprises.2620.1.48.28.5.1.3.7.0 = STRING: "ACTIVE"
Source: sk168878
CCSM R77/R80/ELITE
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter