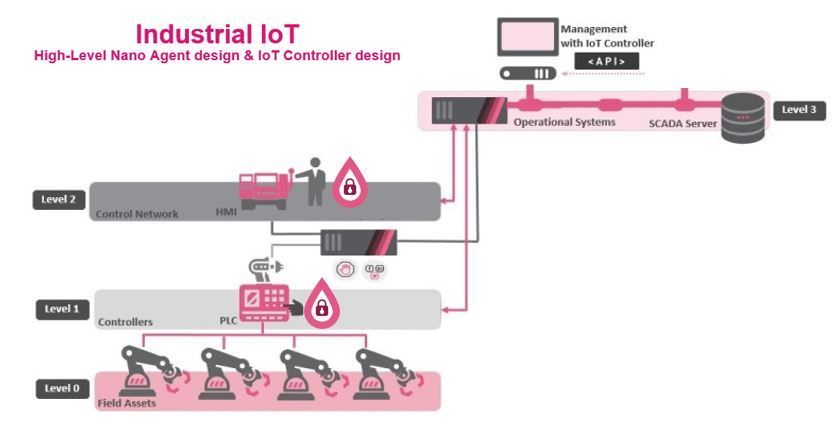
Figure 1: High-Level OT network diagram, using Quantum IoT Embedded and Quantum IoT Controller with Spark gateways
Today I want to discuss processes, protocols, procedures and people in the OT, Operational Technology realm.
Processes
- Discrete/manufacturing | Discrete manufacturing is an industry term for the manufacturing of finished products that are distinct items capable of being easily counted, touched or seen. Discrete manufacturing involves parts and systems like nuts and bolts, brackets, wires, assemblies and individual products. Examples of products made from discrete manufacturing include automobiles, furniture, airplanes, toys, smartphones and defense systems. In theory, a discrete product can be broken down at the end of its lifecycle so its basic components can be recycled.
Figure 2: Example of an discrete OT process
- Service / Distribution | Service and distribution setup is used by energy companies.
 Figure 3: Example of Service/Distribution process
Figure 3: Example of Service/Distribution process
- Continuous | Continuous production system involves a continuous or almost continuous physical flow of materials. It makes use of special purpose machines and produces standardized items in large quantities. Examples are petrochemical, cement, steel and sugar.
Figure 4: Example of a continuous process
Protocols
Insight and visibility on the critical assets with protocols, traffic flows etc. in the OT network is a must. We offer with IoT Controller in depth visibility on all assets. Another OT need is segmentation. Our security gateways could be a nice fit to segment or microsegment the network. Besides that you need (dedicated passive/detection only) security controls. We all remember Maersk. Why do people need to have internet access to the environment over unsecure protocols? Why is SMBv1 open and available from the internet? NotPetya was a nasty ransomware attack, it exploited the EternalBlue vulnerability in windows. What other protocols do we see in those environments? Think of MQTT, CIP, BACnet, Modbus and DNP3. Did you know we even have a category (tag) SCADA protocols in place on our gateways? It contains 1507 applications!
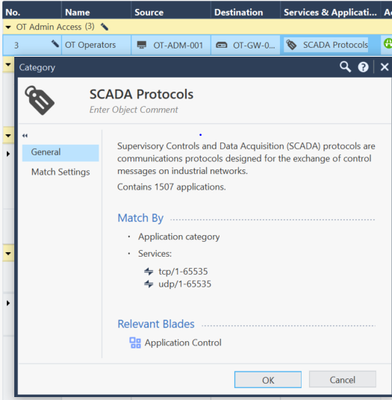
Figure 5: OT Access Policy example
We also offer special SCADA IPS signatures. It is up to you to configure those in detect or prevent mode!
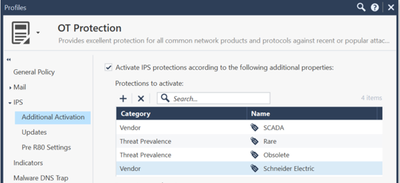
Figure 6: Custom OT Threat Prevention profile
Procedure
We have a great solution, the Compliance Blade. Below an overview of the standards and regulations we have in place in our management for OT environments. You can add a report as a view, create a dashboard and schedule recurring tasks for emailing the Compliance report.
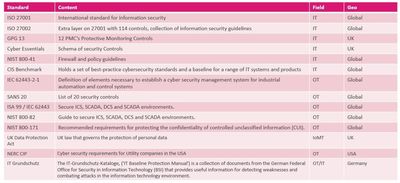
Figure 7: Random selection of OT related, supported regulations and standards
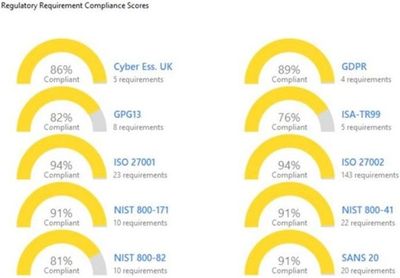 Figure 8: Compliance score overview of selected regulations
Figure 8: Compliance score overview of selected regulations
People
People, OT admins, OT operators, contractors and suppliers need to have (remote) access to specific critical OT assets to do for example maintenance. We recommend to use the principle of least privilege, zero tolerance and zero trust. Minimizing the possible attack surface with the right security controls in place.

Figure 9: Access Policy example to Robot
Overall we recommend to address the 4 "P" pillars to ensure safety and integrity!
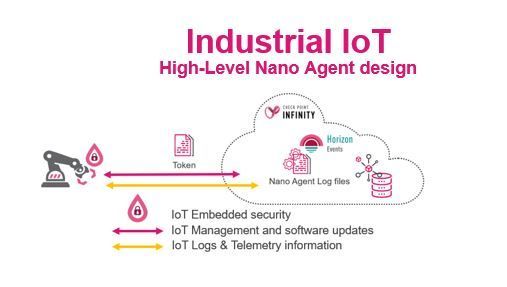 Figure 10: Quantum IoT Embedded, Nano Agent deployed in "online" setup
Figure 10: Quantum IoT Embedded, Nano Agent deployed in "online" setup












