- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- IoT Protect
- :
- Re: Newsletter - IoT Insider | December 2023 Editi...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Newsletter - IoT Insider | December 2023 Edition
Welcome to the December 2023 edition of IoT Insider, your go-to source for the latest news and trends in the world of Internet of Things. In this edition, we bring you a curated selection of news and regulations to keep you informed and empowered in the digital age.
1. Cyber Threats on the Rise | Protect Your Digital Fortress!
As technology advances, so do the risks. We highlight the latest cyber threats making headlines, from sophisticated ransomware attacks to data breaches affecting millions.
- Millions of sensitive patient scan and health records spilled online thanks to decades old protocol .... The research team scanned the internet for 6 months and found that DICOM (Digital Imaging and Communications in Medicine) are exposing 43 million health records. This article clearly outlines the urgency of addressing security challenges in medical scans and health records to safeguard patient data and protect the privacy and trust of individuals
- Have you heard about the Dieselgate but for Trains? BadCyber.com's article "Dieselgate but for Trains: Some Heavyweight Hardware Hacking" sheds light on potential train system manipulation through computer hacking. It's a must-read for anyone interested in train technology and cybersecurity
- Forescout found 21 high-risk vulnerabilities in OT/IoT routers. The vulnerable Sierra Wireless routers are very popular. Over 245,000 networks worldwide running Sierra Wireless for various applications. For example, Sierra Wireless routers are used for police vehicles connecting to a central network management system or to stream surveillance video in manufacturing plants for industrial asset monitoring, in healthcare facilities providing temporary connectivity and to manage electric vehicle charging stations. One of the 21 vulnerabilities has a CVSS score of 9.6!
- The Danish critical infrastructure attack was all about exploiting 3 critical vulnerabilities (CVSS score 9.8) in Zyxel devices. Resulting in RCE (Remote Code Execution) and a buffer overflow with potentially DoS (Denial of Service)
- A new report from Claroty has found that 37 percent of ransomware attacks targeting industrial organizations have a significant impact on both their IT and OT environments
- Exploitation of Unitronics PLCs used in Water and Wastewater Systems. Exploitation of a weak and default password “1111”. Not a best practice at all. In Shodan with a quick search over 1700 exposed devices can be found!!!
2. Global Cybersecurity Regulations | Navigating the Compliance Maze
Governments worldwide are tightening their grip on cybersecurity regulations. Stay updated on the latest compliance requirements, privacy laws, and data protection regulations that can impact businesses and individuals alike. We decode complex jargon and provide practical insights to help you navigate the compliance maze effortlessly.
- Australia issued their 2023 - 2030 Cyber Security Strategy. One of the 6 “Shields” is Protected Critical Infrastructure. There is also an Action Plan. “Activate enhanced cyber security obligations for Systems of National Significance” is all about ICS security.
- New ISO/IEC 27032 standard addresses IoT cybersecurity. According to IEC, the most common types of cyber attacks on IoT devices include: distributed denial of service attacks (DDoS attacks), man-in-the-middle attacks, which involve intercepting or altering the communication between IoT devices and their servers or controllers, brute force attacks, which involve hacking a device by trying different username and password combinations, and eavesdropping attacks, which involve spying on the data transmitted by IoT devices in order to gain personal or sensitive data. The standard is divided into four parts: Part 1 - Overview and introduction, Part 2 - Security requirements analysis, Part 3 - Security implementation and Part 4 - Security assessment and evaluation. Part 1 provides an overview of the standard and its scope. Part 2 provides guidance on how to identify and assess security risks. Part 3 provides guidance on how to implement security controls. Part 4 provides guidance on how to assess and evaluate the effectiveness of security controls.
- The Artificial Intelligence Act (AIA) is a proposed regulation by the European Commission that aims to regulate artificial intelligence (AI) in the European Union. The AIA was first proposed in April 2021, and the European Parliament and the Council of the European Union reached a provisional agreement on the AIA on December 9, 2023. The AIA is the first comprehensive regulatory framework for AI in the world. It aims to ensure that AI is developed and used in a safe and ethical manner, and to protect the fundamental rights of individuals. The AIA will apply to all AI systems that are developed, deployed, or used within the European Union. It will also apply to AI systems that are developed or deployed outside of the European Union, but that are used within the European Union. The AIA will create a four-tiered risk-based regulatory framework for AI systems. The four tiers are: Unacceptable risk: AI systems that pose an unacceptable risk to human rights, safety, or fundamental freedoms will be banned. High risk: AI systems that pose a high risk to human rights, safety, or fundamental freedoms will be subject to strict requirements, such as human oversight and risk assessments. Limited risk: AI systems that pose a limited risk to human rights, safety, or fundamental freedoms will be subject to transparency requirements, such as providing users with information about how the AI system works. Minimal risk: AI systems that pose a minimal risk to human rights, safety, or fundamental freedoms will not be subject to any specific requirements. The AIA will also create a European Artificial Intelligence Board (EAIB) to oversee the implementation of the AIA. The EAIB will be composed of representatives from the European Commission, the European Parliament, the Council of the European Union, and national data protection authorities.
- EU Cyber Resilience Act reaches political consensus to strengthen cybersecurity standards for products
3. Industry Spotlight | Cutting-Edge Innovations in Cyber Defense
Discover groundbreaking advancements and innovative technologies in the world of cyber defense. From artificial intelligence and machine learning to blockchain and quantum computing, we explore how these game-changing technologies are revolutionizing the fight against cyber threats. Get inspired by success stories and learn how to implement these solutions in your own digital ecosystem.
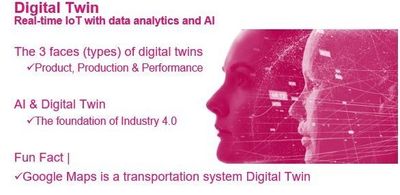
Digital twins
Digital twins are virtual models of real-world systems that can be used to monitor, analyze and optimize their performance. They can be used in a variety of industries, including manufacturing, healthcare and energy.
Some of the benefits of using digital twins include:
- Improved efficiency: Digital twins can help to identify and address inefficiencies in real-world systems.
- Reduced costs: Digital twins can help to reduce costs by preventing unplanned downtime and by optimizing the use of resources.
- Improved safety: Digital twins can help to improve safety by identifying potential hazards and by providing insights into how to mitigate them.
- Increased innovation: Digital twins can help to increase innovation by providing a platform for testing new ideas and by providing insights into how to improve existing products and services.
Here are some examples of how digital twins are being used in different industries:
- In manufacturing, digital twins are being used to monitor and optimize the performance of production lines. They can also be used to predict when machines are likely to fail, so that preventive maintenance can be scheduled.
- In healthcare, digital twins are being used to create virtual models of patients. These models can be used to simulate the effects of different treatments, so that doctors can make more informed decisions about patient care.
- In energy, digital twins are being used to monitor and optimize the performance of power plants. They can also be used to predict when outages are likely to occur, so that preventive measures can be taken.
Digital twins are a rapidly evolving technology and new applications are being developed all the time. As the technology continues to mature, it is likely that digital twins will play an increasingly important role in a wide range of industries. Check out this article from Toobler handling 10 amazing Digital Twin examples.
Did you know that Google Maps is a transportation system Digital Twin?
4. Expert Interviews | Insights from Cybersecurity Gurus
Gain exclusive access to interviews with industry experts, thought leaders, and cybersecurity gurus. Uncover their strategies, predictions, and best practices to protect yourself, your organization, and your loved ones from the ever-evolving cyber landscape. Stay updated on emerging trends, emerging threats, and expert tips to stay cyber resilient.
- Interesting read of Business Growth Reports about IoT Market 2024 Size, Share and Forecast Report
- Another engaging read is of IoT Analytics about Predictive maintenance market: 5 highlights for 2024 and beyond
5. Cybersecurity Awareness Corner | Empowering You with Knowledge
Knowledge is power! Our cybersecurity awareness corner equips you with practical tips, best practices, and actionable advice to enhance your online safety. Learn how to spot phishing attempts, secure your passwords, protect your personal information, and stay safe in the digital world. Be the cybersecurity champion your friends envy!
- Want to test your knowledge of cybersecurity? Take the Cybersecurity Fundamentals Practice Quiz of ISACA
We hope you find this edition of The IoT Insider both informative and engaging. Stay tuned for more exciting updates in the next edition, where we'll dive deeper into the world of cybersecurity. Remember, vigilance and knowledge are key to staying safe in our interconnected world.
Stay secure, stay informed, and stay one step ahead!
3 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Another awesome read, thank you @AntoinetteHodes
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Andy!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Keep them coming, I really love reading these things.
Cheers,
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 1 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter