Hi Masher
I use SAML tracer. Please find the steps
1. Init test
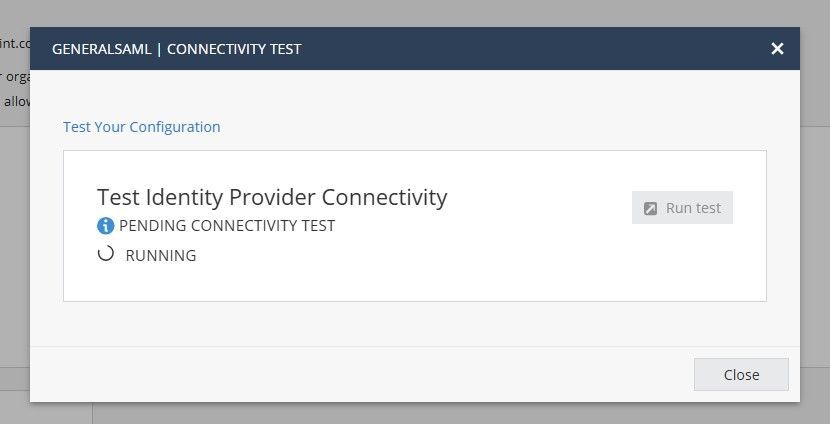
2. IDP log in with SAML request
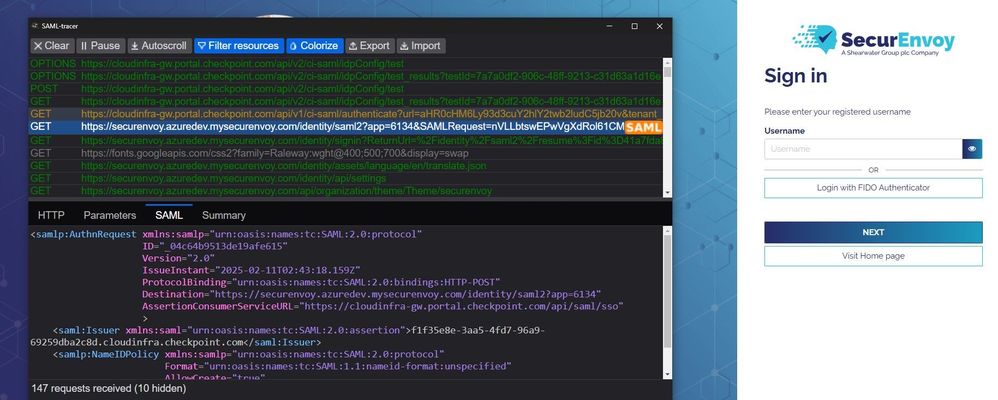
<samlp:AuthnRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"
ID="_04c64b9513de19afe615"
Version="2.0"
IssueInstant="2025-02-11T02:43:18.159Z"
ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Destination="https://securenvoy.azuredev.mysecurenvoy.com/identity/saml2?app=6134"
AssertionConsumerServiceURL="https://cloudinfra-gw.portal.checkpoint.com/api/saml/sso"
>
<saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">f1f35e8e-3aa5-4fd7-96a9-69259dba2c8d.cloudinfra.checkpoint.com</saml:Issuer>
<samlp:NameIDPolicy xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"
Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified"
AllowCreate="true"
/>
</samlp:AuthnRequest>
3. Log in successfully. Redirect to https://cloudinfra-gw.portal.checkpoint.com/api/saml/sso. After a while, it show 504 Gateway timeout. The Test is still running
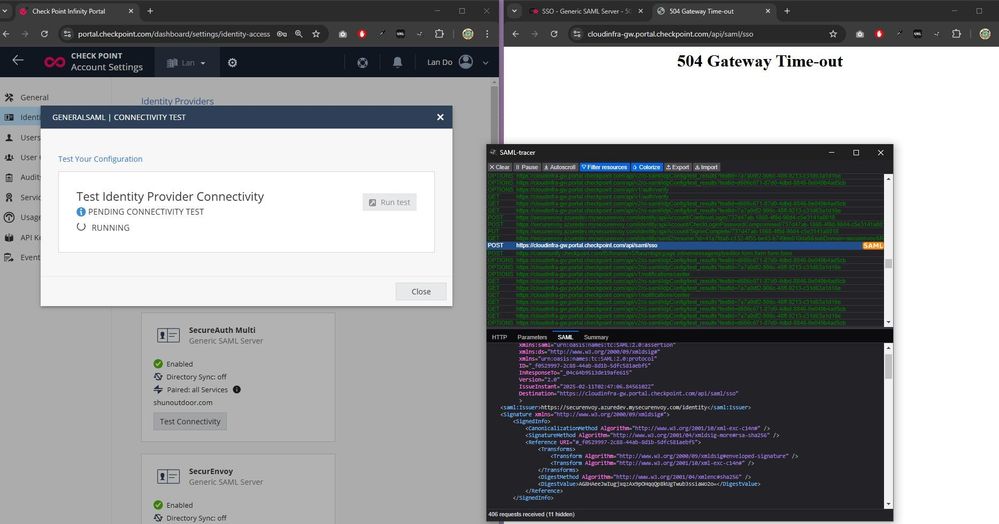
Detail SAML response
<Response xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
xmlns:ds="http://www.w3.org/2000/09/xmldsig#"
xmlns="urn:oasis:names:tc:SAML:2.0:protocol"
ID="_f0529997-2c88-44ab-8d1b-5dfc581aebf5"
InResponseTo="_04c64b9513de19afe615"
Version="2.0"
IssueInstant="2025-02-11T02:47:06.8456102Z"
Destination="https://cloudinfra-gw.portal.checkpoint.com/api/saml/sso"
>
<saml:Issuer>https://securenvoy.azuredev.mysecurenvoy.com/identity</saml:Issuer>
<Signature xmlns="http://www.w3.org/2000/09/xmldsig#">
<SignedInfo>
<CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
<SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256" />
<Reference URI="#_f0529997-2c88-44ab-8d1b-5dfc581aebf5">
<Transforms>
<Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" />
<Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
</Transforms>
<DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256" />
<DigestValue>AG8HAeeJwIugjxqzAx9pOHqqQp8kUgTwub3ssiaWo2o=</DigestValue>
</Reference>
</SignedInfo>
<SignatureValue>e+cg7CAbFqb375RMTrkn6Pu3e3VLvAwjHxHXfDlwjvT/qiwwL5aO3AS6SJf0wx71Vy7FhZoHoYsvr9J+BgSOrcmAJjWeAfkCyzQDI28Q1qj+16rnDO2BWt9SDyY0nnoGGRuhjTixZrgU3OwZ+XQTlbgSvmZSJ8RteTfSvPSr6T6VipAT7OtqWMgB8F5zBfwKV7rWkc5q3TAdGGu2Uyg/dhUI5ToVb/Bi6pc3h02jT/PEh/TxXFCEAPXhFiqYVmWjXgM9wOKmfsDm8I4WNcN3OUS3Eh5Sc4IcCtSfmYP+uLKH18yr4vhmgbBGRjbkRD7B6Qdk4ExltVusC+v4MSCVow==</SignatureValue>
<KeyInfo>
<X509Data>
<X509Certificate>MIIEMzCCAxugAwIBAgIUKncZWBUy7vm/+GNbBcsaT7OGaUkwDQYJKoZIhvcNAQELBQAwgagxCzAJBgNVBAYTAkdCMRIwEAYDVQQIDAlIYW1wc2hpcmUxFDASBgNVBAcMC0Jhc2luZ3N0b2tlMRMwEQYDVQQKDApTZWN1ckVudm95MRQwEgYDVQQLDAtFbmdpbmVlcmluZzEdMBsGA1UEAwwUc2VjdXJlbnZveS5kaXJlY3RvcnkxJTAjBgkqhkiG9w0BCQEWFnN5c3RlbXNAc2VjdXJlbnZveS5jb20wHhcNMjMwNTA5MDc1NDIyWhcNMjgwNTA4MDc1NDIyWjCBqDELMAkGA1UEBhMCR0IxEjAQBgNVBAgMCUhhbXBzaGlyZTEUMBIGA1UEBwwLQmFzaW5nc3Rva2UxEzARBgNVBAoMClNlY3VyRW52b3kxFDASBgNVBAsMC0VuZ2luZWVyaW5nMR0wGwYDVQQDDBRzZWN1cmVudm95LmRpcmVjdG9yeTElMCMGCSqGSIb3DQEJARYWc3lzdGVtc0BzZWN1cmVudm95LmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBALIyLdFrHvJEU5OgC8KqCqJ2+F5jwho+fusouu8DIBAx2L/ShhmekZqBbtHvwtLU73iHmHor3QZ7l1PzCAQnvBhUyg3nOmlxt2GwONtUlQ7+GYTWhVU1aF3fmKKuirxwK6l1kuAfvQi3BpeCh8pmKsmBIKyaaV5Rh3GdwqoUYq7lBFuPsL5XWWGhUNDjuSxl6EAPQ6a9HDG2CVKtALlNkZaLTE489eajXM+ifs2Ag/k8tqPv/LZrSbwjMsk1BJo/H9Bb3PxdDAkBK7c4KSear013sXj6QYPMi1o1nZAfA+F5JlPWnqd2VeQ76agQYzuMnh1jHI5ts6Ir2dgpB4R41K8CAwEAAaNTMFEwHQYDVR0OBBYEFLYWadrDG9Ghm8+xcYcdnujYy584MB8GA1UdIwQYMBaAFLYWadrDG9Ghm8+xcYcdnujYy584MA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEBAE1x1I0zgSDoZrd3Bc8r6RTStAsqAt4TARFHVlFcCY8MDy9kilMS5C57fWDtOeHgVeC4CsFc+cQuoensJ/NQTUFtze42bMwBjzloD+ZOt2plJspVJK/JBXZuSaKvn3cTQ8NhYeYJaGaxi/NhoAPjgZUItT9kSdiotVVpAXXR7QqgR6bX36qAW8QeASk4WZRCpMBjY5t8x34Iab8VzmJE38frjryYheglBs1zOYIMJNWIU+TDIjVjkBojAszCFikreELowGTkKq6uqtvYS24bHY0liIndZ7VKibfTqXdAjmswS/8uf9WJqvrkTmdFwj5OlZCeEIOOAwmCELrr2Bg2loI=</X509Certificate>
</X509Data>
</KeyInfo>
</Signature>
<Status>
<StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success" />
</Status>
<saml:Assertion Version="2.0"
ID="_41d43c47-b69c-4434-b3ca-3021232a3d09"
IssueInstant="2025-02-11T02:47:06.8460516Z"
>
<saml:Issuer>https://securenvoy.azuredev.mysecurenvoy.com/identity</saml:Issuer>
<Signature xmlns="http://www.w3.org/2000/09/xmldsig#">
<SignedInfo>
<CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
<SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256" />
<Reference URI="#_41d43c47-b69c-4434-b3ca-3021232a3d09">
<Transforms>
<Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" />
<Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
</Transforms>
<DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256" />
<DigestValue>gDV6ZL8hUGrL56yGFVs6jgfKa/47ZiRsg2pZdMzhN9E=</DigestValue>
</Reference>
</SignedInfo>
<SignatureValue>ZtIRRMaVhUoQVM97/UjnIEHDWA71FLcQZoEnaNFaS5St0Cjx0midtTfiEIuFQtjjAUSMpw23xbBFolareRoFfZy/qn20KdynxBZXISw+OurBSiI9rYgKoenbAqpmACFcPoqc7SGlRAADL1GUV8CGzs/6PaYLzSO0UfPj8m61EUEeoymCoOgIV1KKfB+NIh3SRIn5+/a1FlxUZAuXh8OQ0RXGCvAUnwmB9A1iFKq8gvuJyxzFcXU4gPNNZzTJXQnCVAXHNjBUKBk0nwau6dlX69Hxg4j35Csmlsj33KJJi8UbZjKI+xTsCSmmKbJe1BfoVPPUISUjUFtZC6Eo+UGpGQ==</SignatureValue>
<KeyInfo>
<X509Data>
<X509Certificate>MIIEMzCCAxugAwIBAgIUKncZWBUy7vm/+GNbBcsaT7OGaUkwDQYJKoZIhvcNAQELBQAwgagxCzAJBgNVBAYTAkdCMRIwEAYDVQQIDAlIYW1wc2hpcmUxFDASBgNVBAcMC0Jhc2luZ3N0b2tlMRMwEQYDVQQKDApTZWN1ckVudm95MRQwEgYDVQQLDAtFbmdpbmVlcmluZzEdMBsGA1UEAwwUc2VjdXJlbnZveS5kaXJlY3RvcnkxJTAjBgkqhkiG9w0BCQEWFnN5c3RlbXNAc2VjdXJlbnZveS5jb20wHhcNMjMwNTA5MDc1NDIyWhcNMjgwNTA4MDc1NDIyWjCBqDELMAkGA1UEBhMCR0IxEjAQBgNVBAgMCUhhbXBzaGlyZTEUMBIGA1UEBwwLQmFzaW5nc3Rva2UxEzARBgNVBAoMClNlY3VyRW52b3kxFDASBgNVBAsMC0VuZ2luZWVyaW5nMR0wGwYDVQQDDBRzZWN1cmVudm95LmRpcmVjdG9yeTElMCMGCSqGSIb3DQEJARYWc3lzdGVtc0BzZWN1cmVudm95LmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBALIyLdFrHvJEU5OgC8KqCqJ2+F5jwho+fusouu8DIBAx2L/ShhmekZqBbtHvwtLU73iHmHor3QZ7l1PzCAQnvBhUyg3nOmlxt2GwONtUlQ7+GYTWhVU1aF3fmKKuirxwK6l1kuAfvQi3BpeCh8pmKsmBIKyaaV5Rh3GdwqoUYq7lBFuPsL5XWWGhUNDjuSxl6EAPQ6a9HDG2CVKtALlNkZaLTE489eajXM+ifs2Ag/k8tqPv/LZrSbwjMsk1BJo/H9Bb3PxdDAkBK7c4KSear013sXj6QYPMi1o1nZAfA+F5JlPWnqd2VeQ76agQYzuMnh1jHI5ts6Ir2dgpB4R41K8CAwEAAaNTMFEwHQYDVR0OBBYEFLYWadrDG9Ghm8+xcYcdnujYy584MB8GA1UdIwQYMBaAFLYWadrDG9Ghm8+xcYcdnujYy584MA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEBAE1x1I0zgSDoZrd3Bc8r6RTStAsqAt4TARFHVlFcCY8MDy9kilMS5C57fWDtOeHgVeC4CsFc+cQuoensJ/NQTUFtze42bMwBjzloD+ZOt2plJspVJK/JBXZuSaKvn3cTQ8NhYeYJaGaxi/NhoAPjgZUItT9kSdiotVVpAXXR7QqgR6bX36qAW8QeASk4WZRCpMBjY5t8x34Iab8VzmJE38frjryYheglBs1zOYIMJNWIU+TDIjVjkBojAszCFikreELowGTkKq6uqtvYS24bHY0liIndZ7VKibfTqXdAjmswS/8uf9WJqvrkTmdFwj5OlZCeEIOOAwmCELrr2Bg2loI=</X509Certificate>
</X509Data>
</KeyInfo>
</Signature>
<saml:Subject>
<saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">ldo@securenvoy.com</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<saml:SubjectConfirmationData Recipient="https://cloudinfra-gw.portal.checkpoint.com/api/saml/sso"
NotOnOrAfter="2025-02-13T14:47:06.8460558Z"
InResponseTo="_04c64b9513de19afe615"
/>
</saml:SubjectConfirmation>
</saml:Subject>
<saml:Conditions NotBefore="2025-02-08T14:47:06.8460585Z"
NotOnOrAfter="2025-02-13T14:47:06.8460588Z"
>
<saml:AudienceRestriction>
<saml:Audience>f1f35e8e-3aa5-4fd7-96a9-69259dba2c8d.cloudinfra.checkpoint.com</saml:Audience>
</saml:AudienceRestriction>
</saml:Conditions>
<saml:AuthnStatement AuthnInstant="2025-02-11T02:47:06.8460604Z"
SessionIndex="_41d43c47-b69c-4434-b3ca-3021232a3d09"
>
<saml:AuthnContext>
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef>
</saml:AuthnContext>
</saml:AuthnStatement>
<saml:AttributeStatement>
<saml:Attribute Name="groups"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"
>
<saml:AttributeValue xsi:type="xsd:string">Everyone</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="urn:mace:dir:attribute-def:userId"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"
>
<saml:AttributeValue xsi:type="xsd:string">67768004</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="identity/claims/givenname"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"
>
<saml:AttributeValue xsi:type="xsd:string">Lan</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="identity/claims/name"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"
>
<saml:AttributeValue xsi:type="xsd:string">Do</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="identity/claims/emailaddress"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"
>
<saml:AttributeValue xsi:type="xsd:string">ldo@securenvoy.com</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
</saml:Assertion>
</Response>
Thank you for looking into this issue
Lan





