- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Security Operations
- :
- Incident Response
- :
- Visualising MITRE ATT&CK® Techniques in IR Reporti...
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Visualising MITRE ATT&CK® Techniques in IR Reporting
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2023-12-04
05:34 AM
In the previous posts (MITRE ATT&CK as a common vocabulary in (IR) reporting and Generating Mitigations/Detections/Validations based on a set of MITRE ATT&CK® Techniques), we decomposed the MITRE ATT&CK® data structure, focused on extracting the available information from the Framework in an automated way for a given set of ATT&CK® Sub-(Techniques).
In this third instalment, we’ll address a couple of options to visualise the given set of ATT&CK® (Sub-)Techniques and their associated Tactics, to support the understanding of the events related to the Incident Response investigation.
In a similar approach as to the previous post, we wanted to retain options which were capable of being automated, at best to the full extent. We obviously may have missed other options to consider and would be grateful if these were pointed out to us.
Navigator Layers
The most straightforward option for visualising the MITRE ATT&CK® Techniques and associated Tactics is adopting the MITRE Navigator Layers.
In essence, the MITRE ATT&CK Navigator Layer is a visual aid and interactive tool that makes it easier to use the vast information in the MITRE ATT&CK framework effectively.
The MITRE Navigator is an application to manipulate the matrix of the Tactics and MITRE ATT&CK® Techniques and generate these Navigator Layers as a result. The Navigator Layers can be created manually by selecting the required (Sub-)Techniques, but it’s also possible to upload a previously exported or custom Navigator Layer. Navigator Layers are in JSON format and are as such a perfect candidate for generating automatically.
Different uses of these Layers can be envisioned, such as demonstrating the applied known Techniques by a perpetrator per Tactic, mapping the combined coverage of the ATT&CK® Techniques through implemented security solutions in the environment, or even combining several layers with your own logic to generate heatmaps based on the user’s requirements. For the last use case, an example could be demonstrating which Techniques with a higher or lower occurrence, requiring the most or the least attention to address, another one could be the theoretical coverage of the security solutions against the Techniques used by one or more perpetrators, etc
Some (commercial) solutions offer a focused and more detailed approach on the aforementioned use-cases, such as Tidal Cyber, which provides mappings of Security Vendor’s solutions to MITRE ATT&CK® as well as a variety of groups, malware families and so on. We’re not diving deeper into this particular application, but it’s worth mentioning one could even upload a custom JSON Navigator layer, such as the ones we’re about to discuss.
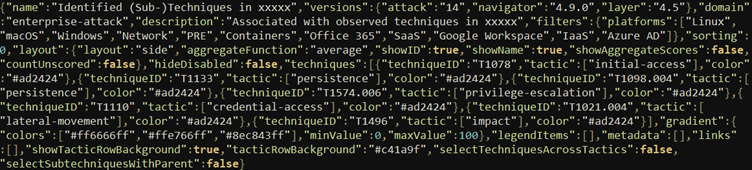
As can be seen in the screenshot of a JSON Layer above, few elements are required to generate a Navigator Layer nor do all the elements need to be defined. In other words, in this context there’s no need to set values for the (Sub-)Techniques you don’t want to annotate, with a small caveat ahead.
However, if the Tactic is not specified, the (Sub-)Technique will be available across the relevant Tactics associated with the (Sub-)Technique. This outcome may or may not suit the individual needs, but as part of our IR Reporting, we require specifying the Tactic as narrow as possible. The comparison of both results is just ahead.
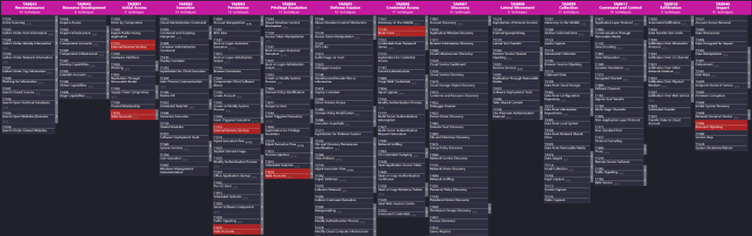
In the first screenshot below, selectTechniquesAcrossTactics equals true and information with regards to the tactics was omitted, resulting in the selection of all (Sub-)Techniques-Tactics pairs. In the second screenshot, only the relevant (Sub-Technique-Tactic pair are kept, reducing the selection of T1078 Valid Accounts being the most obvious change. The latter is also the result from the previous screenshot of a JSON Layer.
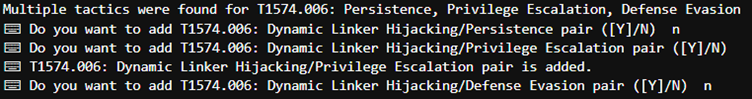
The scripts (https://github.com/nightly-nessie/attack-ir-reporting-ps and https://github.com/nightly-nessie/attack-ir-reporting-py) mentioned in the previous post, do offer this refinement by checking for associated Tactics per (Sub-)Techniques and query the user when more than one Tactic is identified to ensure the relevant pairs are presented. An example interaction is shown below.
Finally, the use of a template ensures the JSON structure is not broken up when filling in the details. This also allows for predefining colour settings, gradients, filters, selection behaviour, disabling the Technique and so on.
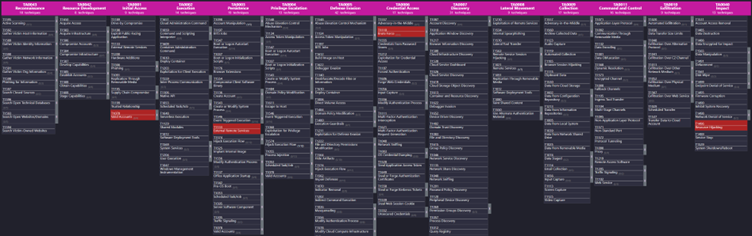
This is where the previously mentioned caveat raises. By default, the user is presented a full matrix including the (Sub-)Techniques which may not be relevant. Consider this to be the full image like in the previous screenshots. However, we also wanted to generate Navigator Layers in a condensed form, so that only the annotated (Sub-)Techniques are visible. This can be achieved by explicitly setting all non-relevant (Sub-)Techniques to be disabled. A JSON extract and a screenshot of the resulting Navigator Layer are shown below. The JSON extract demonstrates the explicit setting of non-relevant (Sub-)Techniques in the upper half, the declaration of the relevant (Sub-)Techniques-Tactic pairs in the lower half.
This approach allows for focusing on the subset of (Sub-)Techniques relevant for the IR Reporting at hand.
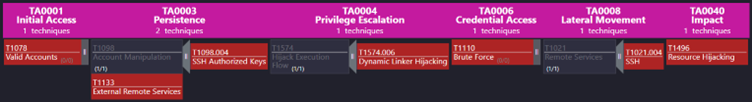
These are the kind of Navigator Layers you would be able to map or compare to other Layers to present a heatmap, as previously discussed. An example could look like below, showing the mapped capabilities of the environment against the identified (Sub-)Techniques across all the Tactics, clearly showing the gap of any coverage against T1098.004 SSH Authorized Keys.
Although this is perfect as a tool for supporting decisions and prioritisation, it does not thrive well in a static environment such as a DOCX presenting the IR Report.
Condensed Navigator (PNG)
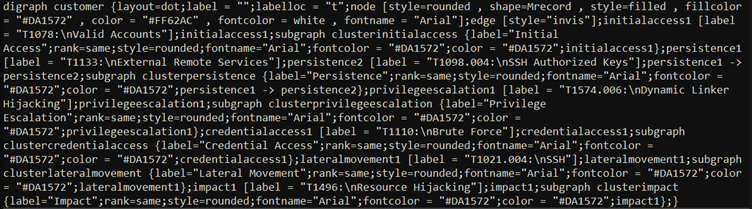
Meet Graphviz and the DOT language which allow us to generate a Navigator alike representation of the information in nearly every graphic format available, including those that are easily added to DOCX documents in the course of generating these documents.
Below demonstrates the content of a DOT file, which was then exported as a PNG file to include in the DOCX.
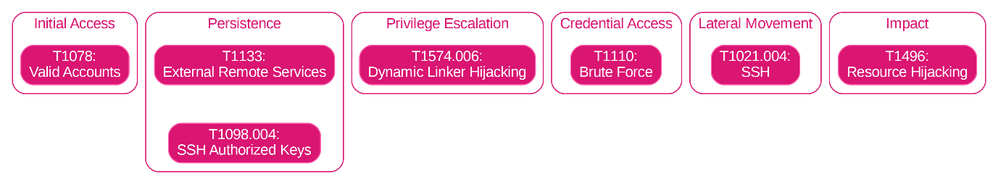
This below resulting image is referred to us by condensed Navigator.
You may have observed that the resulting selected (Sub-)Techniques are exactly the same as in the previous screenshot from the Navigator Layer only presenting the relevant (Sub-)Techniques-Tactic pairs, but this time, no screenshot was required to be taken from the Navigator and the PNG was simply automatically generated and dropped in the document.
CTID Attack Flow Builder
The last option we would like to address in generating a visualisation, is the use of the CTID Attack Flow Builder.
This option provides the least possibilities for automation, as it would require finding a way to translate the discovered or most plausible sequence of used Techniques into the JSON representation of an Attack Flow Builder File (extension .afb).
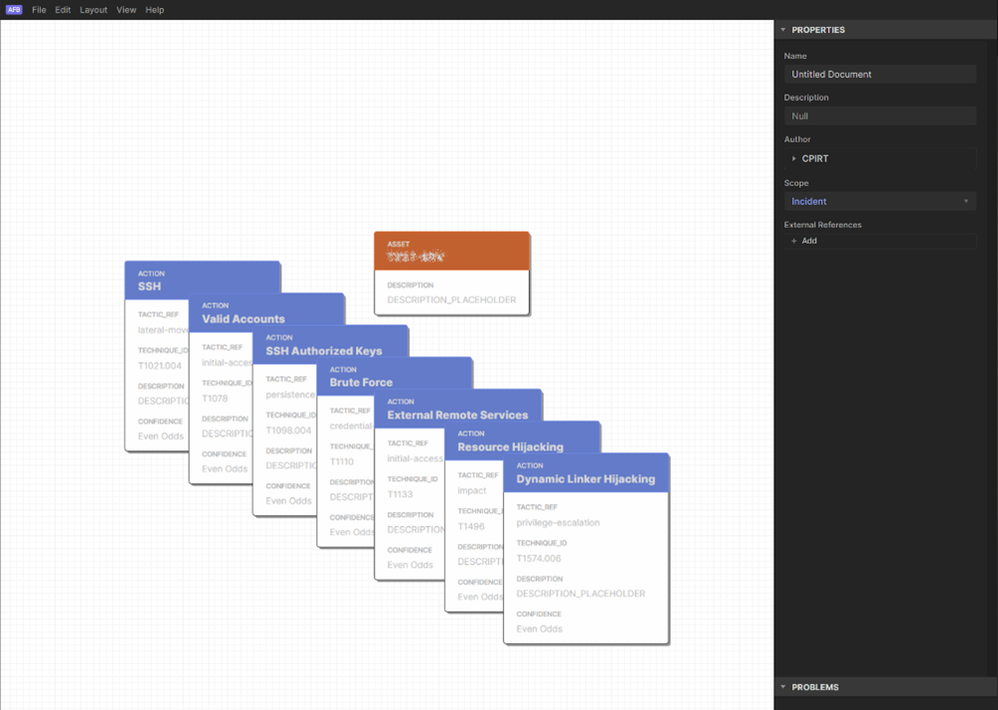
We ultimately ended up with automatically generating an Attack Flow Builder File including the identified (Sub-)Techniques which have been used up to now and added the option to include a list of known involved assets for that particular investigation, prior to generating the Attack Flow Builder File.
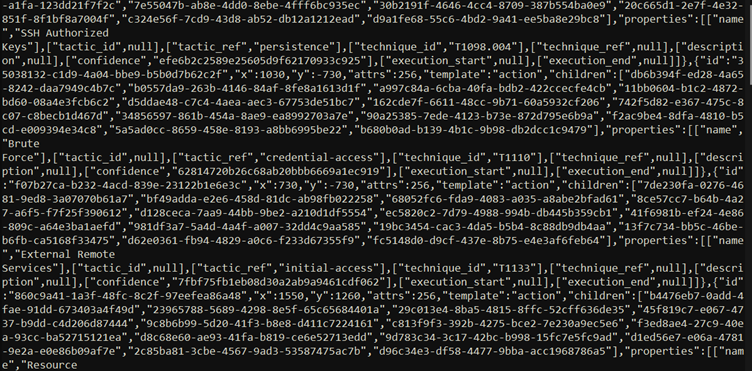
An extract of this generated Attack Flow Builder File is presented below. It seemingly is a rather complex JSON construct.
This approach reduces the time for the analyst to get going with the Flow and establishing the occurrence and flow of events. It should be noted, however, that the way how we adopted the Attack Flow would not adhere to the requirements for sharing in a fully compliant STIX format, as we may exclude mandatory fields, such as the tactic, to reduce the overall resulting image, avoiding an information overload for the reader. After all, the goal is to generate a general overview of the activities, assets involved and impact results, supporting the written investigation results.
The below screenshot is an example of what is being generated in an automated way, ready for the analyst to be imported in the CTID Flow Builder and build the entire flow from this.
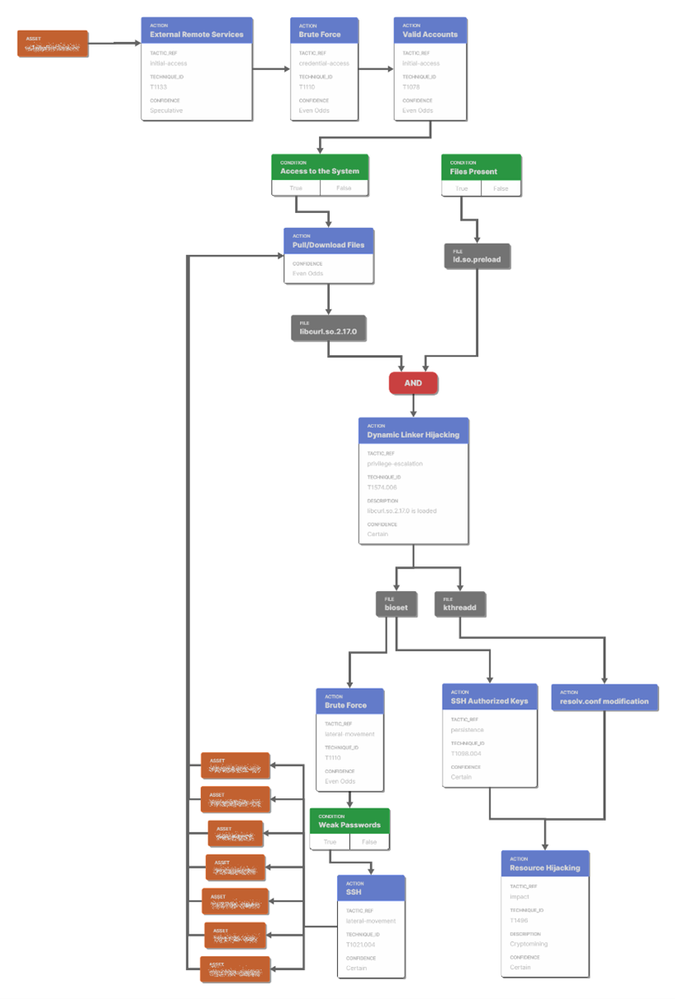
Below is the final result of the Flow representation supporting a real case IR investigation. This visual support helps in many cases to fully understand what occurred and is therefore worth the additional resources required to produce this.
Conclusion
In summary, leveraging MITRE ATT&CK® Navigator Layers proves to be a robust strategy for visualizing cyber threat tactics and techniques. The MITRE Navigator's interactive platform, coupled with JSON automation, facilitates diverse use cases, from mapping security solutions to generating heatmaps. Commercial solutions, exemplified by Tidal Cyber, offer specialized insights, demonstrating the versatility of Navigator Layers.
Additionally, the application of Graphviz and the DOT language provides an alternative for static environments, enabling graphical representations in documents. The CTID Attack Flow Builder, though less automated, offers a comprehensive visualization of attack flows, streamlining incident response investigations.
In essence, the flexibility of these tools, from automated Navigator Layers to graphical representations and detailed attack flows, enhances the efficiency and efficacy of incident response reporting, catering to diverse preferences and requirements from the intended audiences.
References
- MITRE Navigator, https://mitre-attack.github.io/attack-navigator/
- Tidal Cyber, https://app.tidalcyber.com
- Graphviz, https://graphviz.org
- DOT language, https://graphviz.org/doc/info/lang.html
- CTID Attack Flow Builder, https://center-for-threat-informed-defense.github.io/attack-flow/ui
Labels
Labels
-
ATTA&CK
1 -
CPIRT MDR
1 -
Cyber Detective
1 -
DDOS
1 -
DDOS ATTACK
1 -
DDOS PROTECTOR
1 -
Gushers
1 -
Incident Response
7 -
IR
2 -
IRT
2 -
Managed Detection & Response
1 -
Managed Detection and Response
1 -
MDR
2 -
MITRE ATT&CK
1 -
MOVEit
1 -
Podcast
1 -
Ransomware
1 -
Rorshack
1
- « Previous
- Next »
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter