- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- interaction between VRRP and CXL - why is there a ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
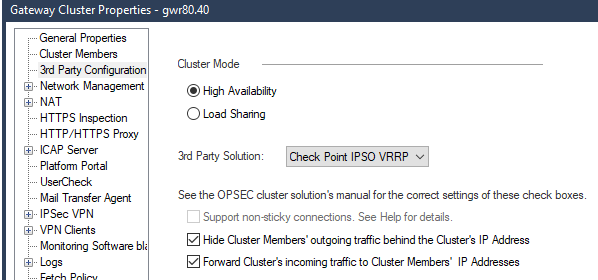
interaction between VRRP and CXL - why is there a tickbox for ClusterXL when the cluster is VRRP
There is a good deal of posts on the difference between VRRP and CXL in this community but they are contrasting one against the other.
I stumbled over the question of the interaction between the two: The question arose …
- whether or not to tick the ClusterXL check box for VRRP deployment and …
- what benefit/change it would have/bring and …
- what use cases would make you choose one over the other.
Initially I was suspicious whether VRRP without CXL would potentially not do session sync but testing this revealed that CCP packets are going across the sync link which seem to transfer the traffic tables between cluster members.
With regards to how to configure this there seems to be contradicting information in various resources:
The following make a point for enabling the CXL tickbox:
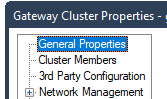
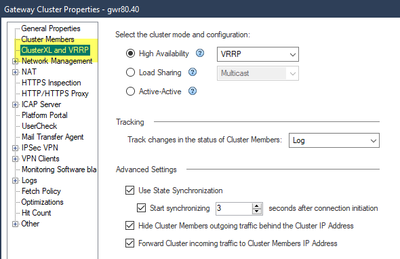
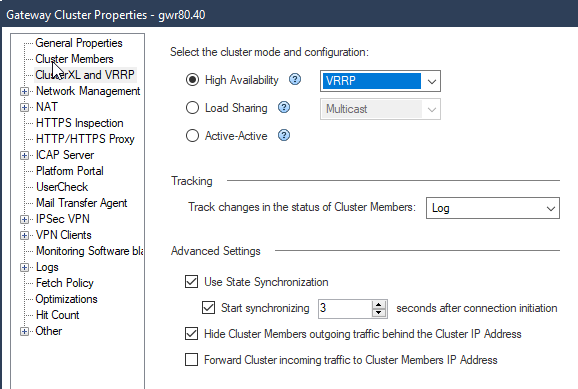
- The fact that the menu changes from “3rd party configuration” to “ClusterXL and VRRP” indicating there is a use case for enabling both at the same time:
changes to - SK on “How to configure VRRP on Gaia”: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
The following make a point against enabling the CXL tickbox:
3. R77.30 ClusterXL Guide:
4. and similarly R80.30 ClusterXL Guide, p73:
5. If session sync already happens without CXL what's the point of enabling the tickbox for CXL. As per the above screenshot only ENABLING the ClusterXL tickbox will give you the option to DISABLE state sync ... which is the opposite of what I expected. But I guess this is another reason that fuels my naive view that it looks as if there would not be any noteworthy additional functionality that the CXL checkbox unlocks.
Any ideas?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Albert
The admin guide is wrong we will fix it today. The source of confusion is the difference between the VRRP implementations:
- VRRP for Gaia - Must select the ClusterXL check box (blade)
- VRRP for IPSO - Must NOT select the ClusterXL check box (blade)
Hope this makes it clear - let me know if not or further information is required
Uri
24 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I understand some confusion. Here is the deal:
When you choose VRRP for clustering, VRRP itself is responsible for Virtual cluster IPs and probing, and ClusterXL is used for sync. The former is happening on OS level, the latter is on FW level.
To install VRRP cluster, as the documentation clearly states, do not mark ClusterXL checkbox in the first time wizard process. You will have to configure VRRP settings through WebUI or Clish later on, follow OS admin manual for that.
On the cluster object, configure 3rd party and VRRP, as in your screenshot. ClusterXL CCP will only be used on FW level for sync, and it will not be active on OS level, relying on VRRP for virtual IPs and network probing.
Hope this help,
Val
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Val,
thanks for the quick response but it doesn't answer my question yet. I fully agree with your approach w.r.t. the first time wizard, but I meant to enquire about the setup in SmartConsole and only after the FTW has completed and whether or not to tick the ClusterXL tickbox and what difference it makes:
You can configure VRRP as the clustering protocol either way, with or without ClusterXL tickbox enabled.
Thanks
Albert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I fail to understand what you are asking.
If you set up VRRP, you should use VRRP for clustering in SmartConsole, exactly as it is shown in your screenshots. There is nothing else to do. You only set up your cluster to ClusterXL if you set it up as such through FTW on each of the GWs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
... yet the SK (see the screenshot from my first post) explicitly states that you have to enable the ClusterXL tickbox when using VRRP wheras you seem to indicate you shouldn't choose ClusterXL anywhere unless I am misunderstanding you?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think the difference is in the OS used.
If you are using some old systems with IPSO or XOS (Crossbeam), than 3rd Party Clustering (ClusterXL disabled) will be correct.
But if you are using Gaia with VRRP, you should enable it as stated in the documentation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Norbert, thanks for chiming in:
I would have intuitively agreed with you and @_Val_ Val who also suggests that CXL is adding functionality for session sync, but session sync works even after I removed the CXL from the GW properties, I'll explain more in my post to Val below, as it matches both your and Val's statements. I would also fully see why an unusual OS choice could impact the choice of whether or not to tick CXL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hmm, you've indeed pointed me to somthing I didn't see before and maybe the clue is indeed in the OS: when CXL tickbox is DISABLED, it specifically says Check Point IPSO VRRP. This clouds everything for me even more...
- Not sure if you agree but shouldn't this trigger a verification warning when your (as per the "IPSO" label) OS-specific clustering mechanism doesn't match the selected OS (which is Gaia)?
- The policy installation worked and VRRP seemed to work fine - what's the IPSO-specific part of it at all?
These questions are not meant to criticise your post, quite the opposite. They are meant as a challenge for the community as I really can't get my head around whether this is just highly unintuitve and results in identical behaviour, or whether one is a "bad" or at least "functionally different" configuration that CP just doesn't alert you to, even if incompatible to your device.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Uh, finally got the source of confusion.
That is the step you are asking about, right?
So, for sync to work, you need to enable ClusterXL kernel module of your FW. It is being done for a cluster object at the General Properties tab.
As I have mentioned before ClusterXL is still required for FW, but not for OS to form a cluster with VRRP.
Personally, I do not see any reason other than habit, to use VRRP and not full ClusterXL solution. But the final decision is up to you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yep, that ClusterXL exactly the tickbox that changes the menu and both with and without having it ticked your failover mechanism can be VRRP. Now the question for me is whether the CXL tickbox choice will make any functional difference at all.
As stated in my initial post:
Initially I was suspicious whether VRRP without CXL would potentially not do session sync but testing this revealed that CCP packets are going across the sync link which seem to transfer the traffic tables between cluster members.
To explain the background of this whole post better, it's based on my customer's (I work at a reseller) question who used to have his old VRRP cluster with CXL ticked and now found that the cluster was migrated to a different CP object that had CXL unticked, so he asked me about which one is correct and whether there is any difference in functionality. There is no current issue, just headscratching on all sides.
So I did the following:
- created my R80.40 lab cluster as VRRP, played around somewhat
- then ticked CXL (but left the clustering mechanism as VRRP in the pane labled "ClusterXL and VRRP")
- disabled the CXL tickbox again,
- pushed policy
...only to find out that session sync STILL worked to my surprise (as verified with fw tab -t connections -u -f). I rebooted but it didn't change, session sync and the typical 8116/udp CCP packets were still happening on the sync link. Maybe I tainted my cluster by enabling CXL and disabling doesn't really work? If you agree that this is the only explanation why CCP packets are on the sync link even after disabling CXL, I'll be testing this again in 10days after some days off again with a fresh cluster that NEVER had CXL enabled (i.e. "3rd party configuration") to see whether it will already sync sessions, contrary to what I think is everybody's expectations unless there is any other suggestions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I admire your curiosity.
I suspect the checkbox in question is related to some legacy settings. Once upon a time, we have supported many different platforms and OSs, and things on Gaia might be more fool-proof than on third party. Anyhow, please stick to the book to be on the safe side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You say stick to the book... That's exactly the problem: The VRRP On Gaia sk92061 and the admin guide provide opposite configuration instructions as per my initial post. I have commented to the documentation team using the SK comment field as follows:
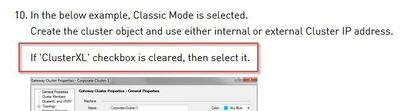
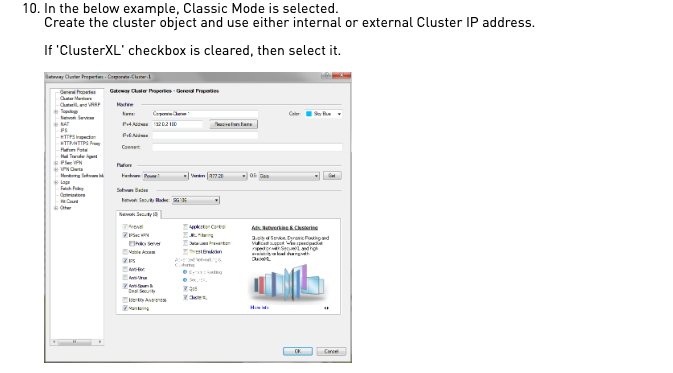
This SK states "If 'ClusterXL' checkbox is cleared, then select it."
In contrast,
https://sc1.checkpoint.com/documents/R80.30/WebAdminGuides/EN/CP_R80.30_ClusterXL_AdminGuide/html_fr... states that you should clear the tickbox.
"To work with VRRP on Gaia cluster, clear ClusterXL.
Go to VRRP pane and configure the applicable settings."
I have tried the community forum to find out what this tickbox does (is it only opening/changing the SmartConsole menu or actually changing the behaviour of the firewall?) and why the configuration instructions contradict each other. Could you provide guidance on these two questions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have to say, I respect your attention to the details, @Albert_Wilkes
You are right, there is a contradiction. The admin manual is incorrect, the SK is correct. When removing ClusterXL, you end up with IPSO VRRP. That is legacy and no longer support config.
I will take it with the relevant team to fix
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
|
Last Updated: 12-Feb-2020
|
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there, these limitations are worthwhile knowing about, but is there anything specific that applies to this post's topic? Sorry, I might just be blind 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, a passage that explains the difference:
|
Not supported by design when VRRP cluster is configured per sk92061 - How to configure VRRP on Gaia (i.e., the "ClusterXL" is enabled in the cluster object). Only one Backup address is supported per interface. |
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for pointing me to it. So it does come with a limitation when enabling the CXL tickbox. Are there any advantages in ticking the box? See my update to Uri below as well which better explains my remaining question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Albert
The admin guide is wrong we will fix it today. The source of confusion is the difference between the VRRP implementations:
- VRRP for Gaia - Must select the ClusterXL check box (blade)
- VRRP for IPSO - Must NOT select the ClusterXL check box (blade)
Hope this makes it clear - let me know if not or further information is required
Uri
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Uri,
many thanks for clarifying this, it's good to get confirmation.
Given that from a functionality POV, my cluster seemed to have worked identically in terms of backup IPs and session sync whether the tickbox was enabled or not at least as far as my quick test went, therefore my questions remain:
Session sync already works, failover IPs are provided by VRRP, so what "other" functionality is put into action by just ticking the box and pushing policy?
To put it differently, does anything functionally change on the firewall by JUST ticking the box or does it initially only unlock other menus in SmartConsole - which then in turn allow you to configure things differently, e.g. disable session sync if you wanted to do so?
I hope I am not overcomplicating things, it's just that the behaviour didn't change in a way that I could recognize between pushing policies with and without the CXL tickbox.
Cheers
Albert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Albert
This is a good question, I don't know what the implication are but I don't think there are any. When testing this on an already configured ClusterXL running on Gaia (the ClusterXL checkbox was cleared and IPSO VRRP selected) I was not able to push the policy.
When this checkbox is clear - this means the underlying high availability protocol is either IPSO VRRP or an OPSEC high availability solution (e.g. F5) but like mentioned above policy installation failed so there are no implications.
When working with ClusterXL there shouldn't be any implications other than the way the HA protocol is implemented if using ClusterXL or VRRP
HTH,
Uri
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In the R80.30 Dashboard, checking/unchecking the tickbox for ClusterXL changes the title of the configuration page from ClusterXL and VRRP to 3rd Party Configuration 8)...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
(1)
We are in the process of correcting the ClusterXL Admin Guides (R80.10 - R80.40).
Example of the fixed section:
(2)
Comparing to the native ClusterXL, VRRP cluster on Gaia has many limitations described in this SK article (as Mr. @G_W_Albrecht provided earlier):
sk105170: Configuration requirements / considerations and limitations for VRRP cluster on Gaia OS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One point out of my experience with VRRP in combination with the central deployment tool and this setting.
If you don't tick ClusterXL in the general Properties and then select VRRP under "ClusterXL and VRRP", CDT won't detect the cluster correctly as VRRP cluster and you can't update/upgrade the cluster automatically.
If everything is set as above, CDT will perform the upgrade on the backup member, fail-over and the upgrade the former active member.
Cheers
Markus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sergei,
thanks for the update, but I find the section is still unchanged - or at least not changed to resolve the discrepancy with the SK. It reads...
To work with VRRP on Gaia cluster, clear ClusterXL.
Go to VRRP pane and configure the applicable settings.
Shouldn't it read:
- To work with ClusterXL or VRRP on Gaia, select ClusterXL.
Go to ClusterXL or ClusterXL and VRRP pane and configure the applicable settings. - To work with VRRP on IPSO or other 3rd party OPSEC cluster, clear ClusterXL.
Go to VRRP pane and configure the applicable settings.
Cheers
Albert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
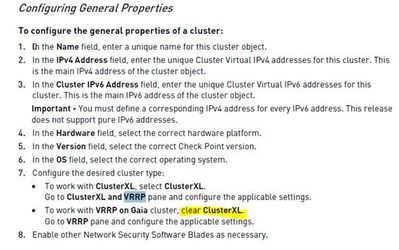
The admin guide has now changed indeed and all looks good and consistent now:
Configure the desired cluster type:
- To work with ClusterXL or with VRRP on Gaia, select ClusterXL.
Go to the ClusterXL and VRRP pane and configure the applicable settings.
- To work with any other cluster mode, clear ClusterXL.
Go to the 3rd Party Configuration pane and configure the applicable settings.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 36 | |
| 16 | |
| 8 | |
| 7 | |
| 7 | |
| 6 | |
| 4 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Wed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchWed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter